Set WMI namespace security via GPO (script)
This was an example of setting WMI security via a script - the specific question was: “Is there a way I can change the permissions on WMI (need to grant remote enable access) so I can grant a service account read access to certain machines via Group Policy?”
This came up on the activedir mailing list.
The short answer is – no you can’t do this via a standard policy setting. You can however do this via an admin logon script or a machine startup script.
The technical goo lies within the SetSD method of the __SystemSecurity class. It takes one parameter – which is the byte array that makes up the security descriptor.
Now – without going to too much trouble the byte array would be hard to get at via a simple VBScript. So we can take a little shortcut here.
We know the service account – let’s say the account name is “Matt” and the permissions will be the same on all machines. So let’s preset this security descriptor on one machine.
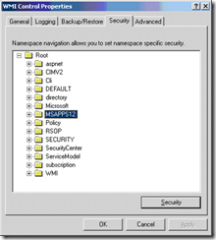
Open the compmgmt.msc snapin and go to the services \ WMI section. For this example I will be setting security on the \Root\MSAPPS12 namespace.
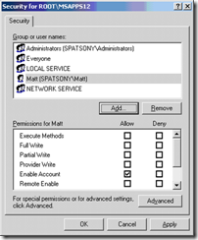
Add your security prinicipal and give him proper permissions ( for whatever you are trying to do )
Once you have done this you can close the snapin.
Now you need to retrieve the security descriptor in proper format..
You can use the following command to get this:
C:\>wmic /namespace:\\root\msapps12 /output:sd.txt path __systemsecurity call getSD
Now if we open c:\sd.txt
Here are the contents:
Executing (__systemsecurity)->getSD()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
SD = {1, 0, 4, 128, 148, 0, 0, 0, 164, 0, 0, 0, 0, 0, 0, 0, 20, 0, 0, 0, 2, 0, 128, 0, 4, 0, 0, 0, 0, 18, 24, 0, 63, 0, 6, 0, 1, 2, 0, 0, 0, 0, 0, 5, 32, 0, 0, 0, 32, 2, 0, 0, 0, 18, 20, 0, 19, 0, 0, 0, 1, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 18, 20, 0, 19, 0, 0, 0, 1, 1, 0, 0, 0, 0, 0, 5, 20, 0, 0, 0, 0, 18, 20, 0, 19, 0, 0, 0, 1, 1, 0, 0, 0, 0, 0, 5, 19, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 2, 0, 0, 0, 0, 0, 5, 32, 0, 0, 0, 32, 2, 0, 0, 1, 2, 0, 0, 0, 0, 0, 5, 32, 0, 0, 0, 32, 2, 0, 0};
};
The byte array we see is what we need.
Copy it and then place it into notepad – remove all the spaces and then insert it into the following script.
strSD = array( ** insert data here *** )
set namespace = createobject("wbemscripting.swbemlocator").connectserver(,"root\MSAPPS12")
set security = namespace.get("__systemsecurity=@")
nStatus = security.setsd(strSD)
Now, if we run this script as admin - it will replicate the same DACL on the namespace when run.
Here is a video of the whole thing in action.
No audio and its not the best quality - I didnt have time to do anything special to it,
The one part which could use some narration is the array from sd.txt :
You copy it then pop it into a clean instance of notepad - do a ctrl+h ( replace ) then in the top line just enter a space, and in the second line do a delete. You will replace all the spaces with this and then you can place it in the script.
Have fun..
spatdsg
Comments
Anonymous
December 11, 2007
Great info. Setting namespace security is not trivial and this is an excellent approach. Thanks!Anonymous
June 26, 2008
Wow, this was EXACTLY what I was looking for... I thought I was dreaming when I came across this page. Works perfectly for GPO and lets me deploy SNMP/WMI monitoring with Zenoss across all servers with little interference. THANK YOU! :-D!Anonymous
January 12, 2009
Thanks! I needed to complete this for 100+ devices throughout my domain, so I utilized Group Policy to push the finalized script... what a time saver!!!!! :)Anonymous
April 06, 2009
The comment has been removedAnonymous
September 28, 2009
I think you just made my day! :) Thank you very much.Anonymous
November 15, 2009
Amazing. Works perfectly. You're my hero of the day :) Thanks a lot.Anonymous
December 03, 2009
Top stuff. Exactly what we were looking for. Thanks :)Anonymous
February 15, 2010
This is one of those pages who will be a lifesaver for years to come. thank you very muchAnonymous
February 24, 2010
For Windows Server 2003 (and 2003 R2) the namespace may be \rootMSAPPS11 instead of 12. Awesome guide by the way. Real life saver.Anonymous
May 11, 2010
Thank you sooo much u just made my day !!!!! without this i would have to do the wmi secu config on 100 servers ;-PAnonymous
May 25, 2010
many thanks, this is so easy and simply saved my a lot of work doing this manualAnonymous
July 18, 2010
Thanks a lotAnonymous
January 12, 2011
So if lets say Matt & Chris are the account names on the one machine where we derive the bits from, if I run the cscript with those bits on the other machinie, will it add both Matt and Chris to the security of cimv2?Anonymous
January 12, 2011
So if lets say Matt & Chris are the account names on the one machine where we derive the bits from, if I run the cscript with those bits on the other machinie, will it add both Matt and Chris to the security of cimv2?Anonymous
January 21, 2011
is there a way to do this in batch script?Anonymous
February 28, 2011
@adam - yes.Anonymous
September 13, 2011
Thanks it take a snapshot of configuration but how to add a parameter in the configurationAnonymous
July 20, 2012
How to handle the fact that users created have different SID on the computers ?Anonymous
September 05, 2012
When I am deploying the script, and checked the security properties, I am unable see the specific account, it is showing as "Account unknown"Anonymous
November 12, 2013
I am late to this post, but I'm scouring the net for something to script perms for 1000 servers mixed between 2003, 2008, 2008R2 and I can't find anything. I want to set perms on rootcimv2 and somehow script it. I've found a powershell script to do 2008/2008 r2, but nothing for 2003, can anyone help? I'm lost on what's happening with this for some parts, I get the pulling of the permissions, but then deploying it through a script I would have to do someway, but can't do it via GPO due to a MESS of an AD organization I've inherited.Anonymous
December 01, 2013
Excellent! Thank you for this contribution!Anonymous
March 05, 2015
Virtual Kiss Was searching for this for days...Anonymous
April 09, 2015
The comment has been removedAnonymous
April 23, 2015
Thanks for such great script!! I've tried your script and it works perfectly fine! I need to do 1 more thing is to select user to setSD. For example user "Tifa" will have this binary SD. How to do this?Anonymous
April 28, 2015
Hi, thanks a lot for the script! How do I set WMI permission on a remote computer, for selected user groups?Anonymous
May 07, 2015
Thank you, much appreciated! Works like a charm.Anonymous
July 07, 2015
Nice, but this will overwrite the settings on the system. Is there also a way to add just one group without overwriting the other settings?- Anonymous
June 07, 2018
YES! It will replace lots of other permissions and break stuff. Trust me. I know.
- Anonymous
Anonymous
July 14, 2015
Thanks for an excellent guide! @Greg I have the same question. How will this work if I create a local user distributed via GPO on multiple Windows clients? I can see it working flawless using a domain account but when it comes to local accounts I guess the SID changes.Anonymous
December 01, 2017
been struggling with this a lot. thank you!