Sidebar Security
Brian Teutsch, Windows Sidebar Program Manager
The Windows Sidebar is a new Windows Vista component that provides a runtime for "gadgets." Gadgets are mini-applications designed to present the user with information or utilities. The Windows Vista Sidebar treats gadgets very similar to the way Windows Vista treats all executable code. The Sidebar team is completely committed to making Vista the most secure version of Windows ever, and that includes the security and trustworthiness of gadgets.
Sidebar Gadget development
In the version of the Sidebar included with Windows Vista, gadgets are developed using the capabilities of the Microsoft HTML engine, including HTML markup, script, images and many other capabilities. The Sidebar also provides a rich set of APIs available to the HTML script code as well as the ability to interact with previously installed ActiveX objects.
Gadget download
Gadgets are written using HTML and script, but this HTML is not located on an arbitrary remote server as web pages are. HTML content in the Sidebar is downloaded first as part of a package of resources and configuration files and then executed from the local computer. This download process is similar to applications (.exe files) downloaded from the Internet.
The files can be packaged using ZIP compression or as a Windows Cabinet File (CAB file). If the file is packaged as a CAB file it is possible to use a code signing certificate to provide information about the origin of the gadget. The user is presented with information about the gadget package before the gadget files are extracted. Signing a gadget can be accomplished with the application “signtool.exe” included with Visual Studio 2005.
Only after the user has viewed information about the gadget are the files extracted from the gadget package and loaded into the MSHTML control to render the content and run scripts.
Note: The following images are from pre-release software and may be subject to future changes.

Figure 1 - Installation dialog with code signing information
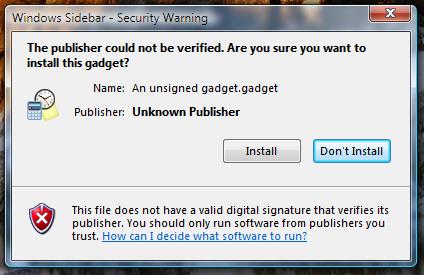
Figure 2 Gadget installation warning for an unsigned gadget.
Because code signing certificates are costly and not common among casual developers likely to create HTML gadgets, we have chosen not to place any requirements that gadgets must be digitally signed.
HTML runtime
HTML gadgets lead themselves to many comparisons with the security models found in Internet Explorer and associated with domain sandboxing security models. However, HTML gadgets have more in common with HTML Applications (HTA) than they do with HTML content in Internet Explorer. Because gadgets have a similar download and installation experience as other executable code, it is appropriate to provide them with a similar set of capabilities when run. The MSHTML runtime is configured similarly to the set of permissions given to HTML Applications or the Local Machine Zone security configuration.
For instance, gadgets are configured in several ways that web pages are not. Because gadgets are treated as executable code, they are allowed to create any installed ActiveX objects because the option “Initialized and script ActiveX controls not marked safe for scripting” is configured as such. Another option configured differently than web pages is “Access data sources across domains,” because gadgets can be more useful when they aggregate data from various locations. A final option specific to Sidebar gadgets is that the HTML pages are not allowed to download and install new ActiveX controls because the options to download signed and unsigned ActiveX controls are both disabled.
User Account Control interaction
User Account Control (UAC) is a new feature of Windows Vista that makes it easier to use Windows as a standard user. If the user is running as a standard user, the Sidebar Gadgets will run with standard user privileges as well and will be restricted from making dangerous system changes to the user’s PC. In the Administrator Approval Mode of UAC, even if the user is a member of the administrators group, by default Sidebar Gadgets will run with standard user privileges. This helps prevent code running in the Sidebar from modifying protected resources.
As an additional precaution, gadgets for the Sidebar Gadgets will not display the UAC elevation prompts that are used to allow programs to run with full administrator privileges. If a Sidebar gadget launches an application installed on the computer, however, that application may display UAC elevation prompts.
For example, if a gadget attempted to delete a file in the System32 directory, the delete operation would not succeed and no elevation prompt would be shown to the user. This failure happens because most critical files cannot be modified by standard users and the Sidebar does not display an elevation prompt.
Parental Controls interaction
Windows Vista includes a new feature named parental controls to help enforce various safe browsing and execution policies on a computer. For example, a parent in the home may only allow a child to run games that are rated G only and browse to only three specified Web sites. The policy for Web browsing also applies to Gadgets in the sidebar. For example, if the parental control policy only allows a child to browser to Web sites “A” and ”B,” and a gadget attempts to communicate with site ”C,” it will fail.
Windows Defender interaction
The download of gadgets is made more secure by the presence of Windows Defender in Windows Vista. When enabled, Windows Defender checks downloads initiated from within Internet Explorer. Thus, for example, Windows Defender will scan gadget packages that are being downloaded to examine for malicious code that may be present in the download. This scan protects users by taking place before a gadget is run or even installed.
Internet Explorer Protected Mode
Internet Explorer 7 in Windows Vista has a new security feature called Protected Mode. Protected Mode is an enhancement designed to protect users from malicious software running in the context of an untrusted remote web page while browsing the internet. Protected Mode is not applicable to gadgets as they are code present on the local computer and interact with files and APIs on the local computer.
Full trust only
Gadgets are mini-applications. Although an individual gadget may only have a single need – such as reading files and information from the computer, accessing information from one or more domains, or only displaying buttons and information for a utility – the full set of gadgets mix and match needs in a huge variety of ways. In aggregate, gadgets have the same set of needs as other code.
The choice to run a gadget is presented to the user in the same way that the choice to run any application downloaded from the internet is presented to the user. Information about the author is presented in a dialog that indicates there is risk associated with this file. After the first user acceptance, the gadget can be run without further prompting by using the Windows Sidebar’s “Add Gadget” dialog.
Additional security for corporations
If your users are in an environment controlled by group policy, it is possible to limit the use of gadgets beyond what is described above. The Sidebar supports a shared gadgets directory under Program Files that can only be modified by the administrator group on that computer. Gadgets can be placed in that directory for all users on the machine to use. Further, there is a policy option to disable the ability for users to install new gadgets into their user directories. This policy option also prevents the use of any gadget that is not present in the Shared Gadgets folder – which can only be modified by an administrator.
The Windows Sidebar has the following group policy options available:
- Turn off Windows Sidebar
This policy allows administrators to completely disable the Windows Sidebar. The user will not be able to start the Windows Sidebar if this policy is enabled. - Disable unpacking and installation of gadgets that are not digitally signed.
This policy allows an administrator to require that all gadgets installed by a user are digitally signed. This policy only affects gadgets that are downloaded and then run, such as double-clicking on a gadget package. All previously or manually installed gadgets will still function. - Turn Off User Installed Windows Sidebar Gadgets
This policy provides administrators with the ability to block all gadgets not placed into the Shared Gadgets or Gadgets folders (in the Sidebar’s Program Files folder), both of which can only be modified by a user in the administrator group. Gadgets in the user’s directory will not display in the Gadget Gallery dialog or otherwise be allowed to run. - Override the More Gadgets Link
The Gadget Gallery dialog provides a link where users can discover more gadgets. By default this link points to an online Microsoft website, however administrators can specify that this link open another website. Administrators can then more easily distribute gadgets that are approved for use within their organization.
These policies are described in more detail in other documentation regarding Windows and group policy options.
Comments
Anonymous
August 31, 2006
Brian Teutsch, Program Manager for Windows Sidebar posted an article on the sidebar security model in...Anonymous
August 31, 2006
I just noticed these blog posts related to Windows Vista security that may interest y'all.
Built-in...Anonymous
August 31, 2006
PingBack from http://heterogeneous.wordpress.com/2006/09/01/miscellaneous-windows-vista-security-stuff/Anonymous
September 01, 2006
In gadget.xml, there's a /gadget/hosts/host/permissions tag. All the samples I've looked at have "Full" as the value in this tag. Are there other legal values?Anonymous
September 02, 2006
"Full" is indeed the only value supported for the Windows Vista Sidebar. We have documentation on the syntax of the manifest that should be ready shortly to explain all elements, attributes and allowed values.Anonymous
September 04, 2006
I get a few questions about security of gadgets in the Vista Sidebar.  Brian Teutsch, PM on sidebar...Anonymous
September 04, 2006
The Windows Sidebar Team has launched their very own blog called "Gadget Corner."  Here, team members...Anonymous
September 05, 2006
<p><a href="http://blogs.msdn.com/sidebar/archive/2006/08/31/733880.aspx">http:/Anonymous
September 09, 2006
Actually, the code signing bit is not entirely correct. Certificates can be made for free using tools available with the Windows SDK, and can be used to sign CAB files.
I've signed gadget CAB files without paying a penny and had them show up alright with the yellow icon in the sidebar's dialog.
Although I don't like how the name is the file name rather than a friendly name. It would be great if the sidebar could extract a friendly name from the archive and gadget.xml file to use instead.Anonymous
September 11, 2006
It is true that test certificates can be easily created, however these certificates are usually only valid for the machine or domain in which they were created. Certificates that will work anywhere require a root certificate authority to issue the certificate, and these certificates cannot be created for free.Anonymous
October 24, 2006
Les Desktop Gadgets sont aussi connus sous le nom de Sidebar Gadgets ou Gadgets Vista. Ces gadgets sontAnonymous
November 08, 2006
PingBack from http://windows-vista.highdiy.com/index.php/gadgets-security/Anonymous
November 17, 2006
I just noticed these blog posts related to Windows Vista security that may interest y'all. Built-in AdministratorAnonymous
January 05, 2007
PingBack from http://www.vistalogy.com/2006/08/31/windows-vista-sidebar-security/Anonymous
January 30, 2007
The comment has been removedAnonymous
February 07, 2007
PingBack from http://4vista.info/?p=67Anonymous
February 10, 2007
PingBack from http://ipfreaks.com/dreamscene/?p=60Anonymous
February 15, 2007
PingBack from http://www.vista-word.com/?p=49Anonymous
May 05, 2007
PingBack from http://noh6.org/ic-computers.htmlAnonymous
October 30, 2007
PingBack from http://discount-perfume-hq.com/?p=1898Anonymous
October 31, 2007
PingBack from http://discount-perfume-hq.com/?p=2798Anonymous
January 25, 2008
PingBack from http://softwareinformation.247blogging.info/windows-vista-security-windows-vista-sidebar-security/Anonymous
January 25, 2008
PingBack from http://burrowowl.net/wordpress/200801/user_access_control/Anonymous
May 05, 2008
PingBack from http://alexa.freeairmedia.com/sidebargadgets.htmlAnonymous
July 01, 2008
Hi, Can you please describe or give a link to the html limitations in a Vista Sidebar Gadget? I know that iFrame and their inner forms are limited (opened up in Internet Explorer). Thanks, AsafAnonymous
May 29, 2009
PingBack from http://paidsurveyshub.info/story.php?title=gadget-corner-sidebar-securityAnonymous
June 30, 2010
Thank you for writing such an appealing post. Normall I see the same thing and it starts to get on my nearves. Thanks again and I’ll be back for more. <a href='http://nyc.cabcorner.com'>Cab Share in NYC<a/>