Software Defined Networking - Adding layers of security
Bringing the Azure fabric into your datacenter
Windows Server 2016 Datacenter edition provides access to many great enterprise features that are now absent in the Standard edition product. One of these is Software Defined Networking (SDN). In conjunction with Software Defined Storage (SDS), particularly Storages Spaces Direct (S2D) this creates the first easily achievable single product Software Defined Datacenter (SDDC).
Well that's enough acronyms for one post. What does all this mean to the hardworking datacenter architect or administrator?
The traditional datacenter contains all of the elements below whether there are 50 physical servers or 5000. In this sort of environment if a typical three tier application is deployed, there are a number of physical tasks required. These include provisioning storage for the application, configuring the network switches and routers to allow or prevent access as required between tiers and provisioning the necessary network subnets and security within those to deploy the application in a secure manner. This can be time consuming and costly in man power and sometime equipment terms.
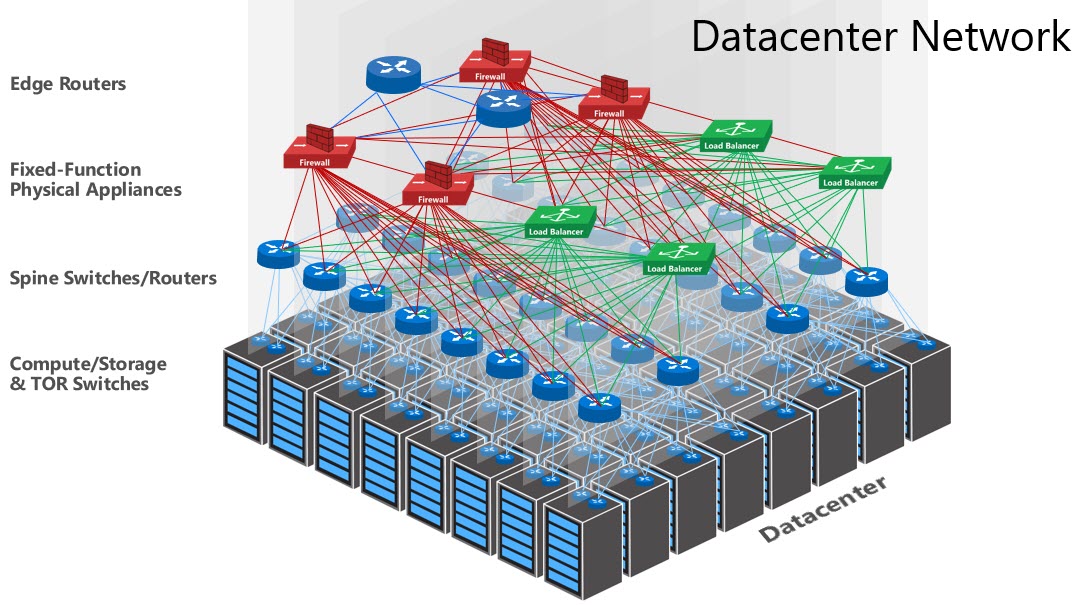
With the release of Windows Server 2016 Microsoft have updated and completely reinvented their Network Virtualization platform. For the techies amongst you in now uses the VXLAN technology instead of the NVGRE technology. In addition Windows Server 2016 now includes many parts of the Azure fabric such as Network Controller (NC), Software Load Balancer (SLB) and Network Security Groups (NSGs).
What can I achieve and why do I need it?
Network virtualization provides the ability to isolate applications and application tiers from other parts of your physical network. This enables multiple instances of the same network address on the same physical network without any conflicts or clashes. Perhaps, more importantly SDN and SDDC also provides the ability to carry out all the deployment actions required without any human intervention. The end result is a much more secure application with more layers of embedded protection.
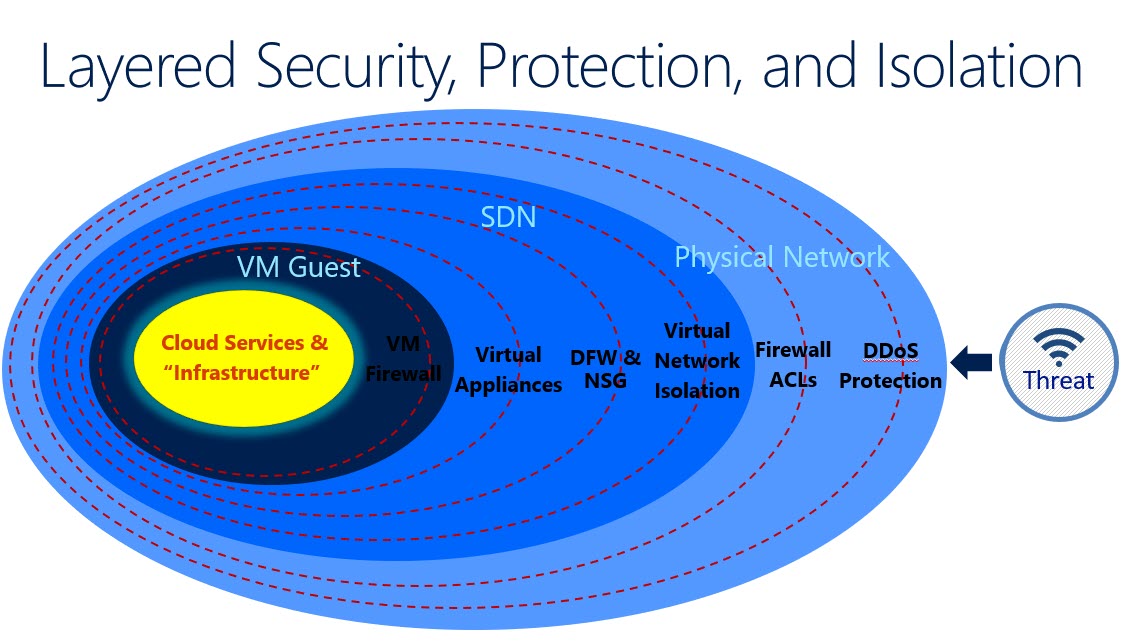
With a non virtualized network, the first two layers of defence should exist in most networks. Firewalls and DDOS defence. Once past those two layer any attacker would have unrestricted movement inside the network and free rein to attack workloads visible there. When you add the SDN layers you automatically gain another layer of network isolation requiring both routing and permissions to access. The Windows Server 2016 Datacenter Firewall (DFW) and the NSGs added to protect those layers add another level of security to the model. Finally the SDN technology allows for virtual appliances to be connected to either further protect or analyse traffic inside the network.
What is the process to achieve this?
To deploy and manage SDN in Windows Server 2016, you require the datacenter edition and you need to deploy a number of physical and virtual roles such as Network Controller and Software Load balancer. Once the architecture is deployed, you can then use either System Center VMM, PowerShell or a 3rd party REST API application to deliver the SDN.
As an example, imagine a three tier application with a web server, a file server and an active directory domain controller all of which require different levels of access depending upon your identity, location and role.
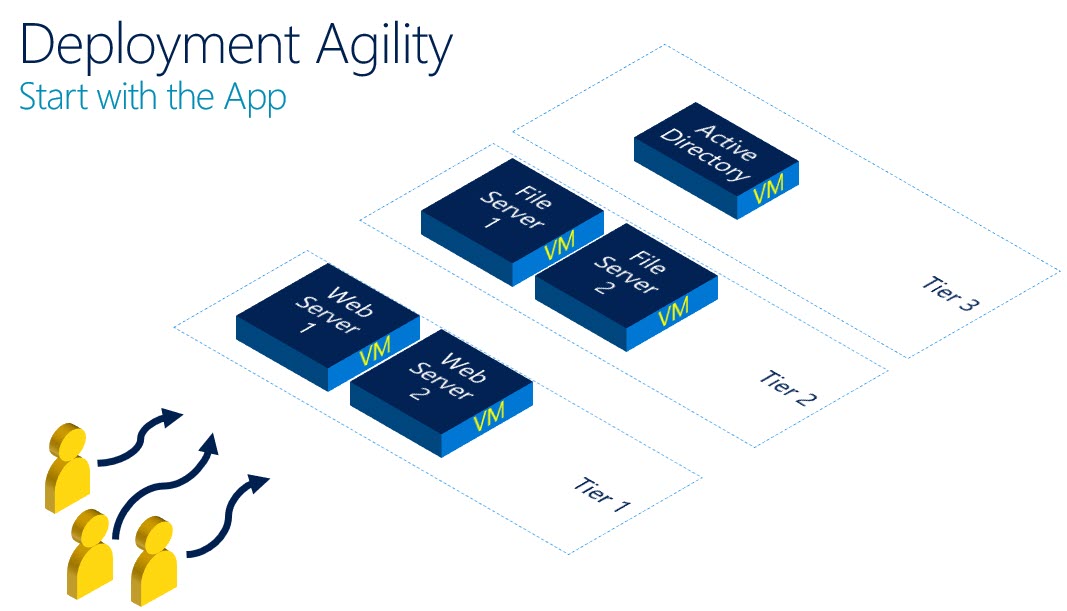
To fully isolate and secure this application requires only some clever creation of Network Controller policies and deployment using PowerShell. The end result is
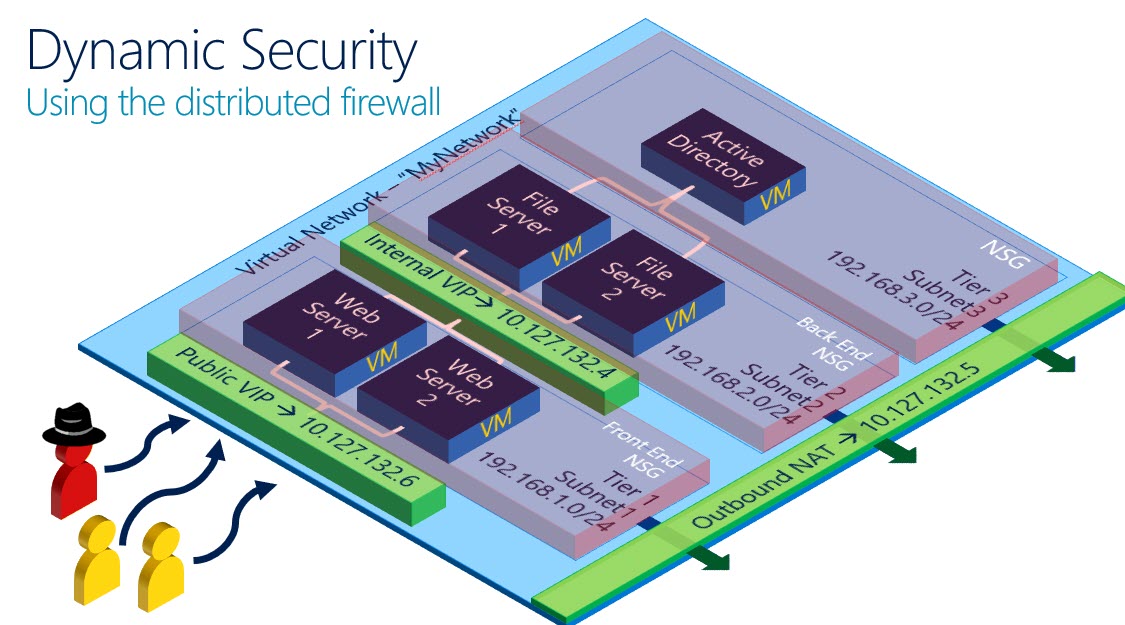
A fully secured multi-tier application with protection through network isolation, NSG and network address translation. All achieved without any human interaction (once policies are created). The effect is that this can be replicated many times for many different application depending upon demand and location requirements. External customers can access the web tier but not the file server or active directory. The internal application staff can also access the file server to collect data whilst no one but IT administrators can access the active directory. A fully secure application, and with the GDPR coming in to force on 25th May this is another great reason for investing in Windows Server 2016 datacenter.
Why not download the evaluation and check it out! If you haven't the time for that then head on off to https://www.microsoft.com/handsonlabs to experience all the joys of the new server features in short learning experiences.290 labs including this one helping you to deploy SDN without building the environment first.
Finally tweet @serverguyuk or email him at serverguy@microsoft.com letting him know how you got on.
Comments
- Anonymous
February 18, 2018
great article!