Non-Domain Servers (DMZ servers) monitoring
Operations Manager requires mutual authentication be performed between agents and management servers prior to the exchange of information between them. To secure the authentication process between the two, the process is encrypted. When the agent and the management server reside in the same Active Directory domain or in Active Directory domains that have established trust relationships, they make use of Kerberos V5 authentication mechanisms provided by Active Directory. When the agents and management servers do not lie within the same trust boundary, other mechanisms must be used to satisfy the secure mutual authentication requirement.
In Operations Manager, this is accomplished through the use of certificates issued for each computer. If there are many agent-monitored computers, this results in high administrative overhead for managing all those certificates. To reduce this administrative overhead, Operations Manager has a server role called the gateway server. Gateway servers are located within the trust boundary of the agents and can participate in the mandatory mutual authentication.
To support the mandatory secure mutual authentication between the gateway servers and the management servers, certificates must be issued and installed, but only for the gateway and management servers. This reduces the number of certificates required, and in the case of an intervening firewall it also reduces the number of authorized endpoints to be defined in the firewall rules. The following illustration shows the authentication relationships in a management group using a gateway server.
In this blog section, we will see how to install a Certificate Authority Server and How to create a template to issue Operations Manager Certificates.
All you have to do is to Add Active Directory Certificate Services role and the Certification Authority Web Enrollment.
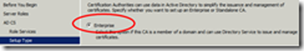
Open the Active Directory Certificate Services and Click on Certificate Template then Right click on IPSec (offline request) and choose Duplicate Template.
Once you click on Duplicate Template the following wizard will pop up
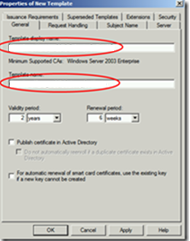
Name your certificate template
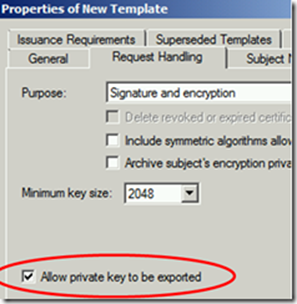
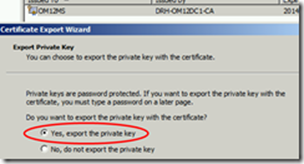
Ensure that Allow Private Key to be exported is ticked.
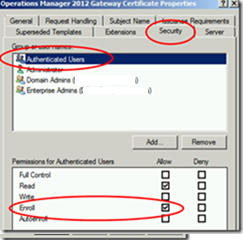
In the Security Tab Allow Authenticated users to Enroll Certificate.
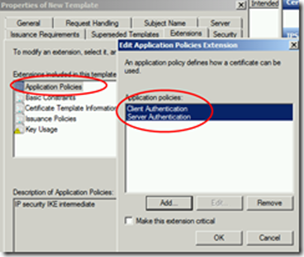
In the Extensions Tab, double click on Application Policies and remove PKI and add Client Authentication and Server Authentication.
Then right-click on Certificate Template > New > Certificate Template To Issue.
And Select the Template that you have just created.
Now we have our Certificate Authority ready to issue certificates that will be used for the mutual Authentication.
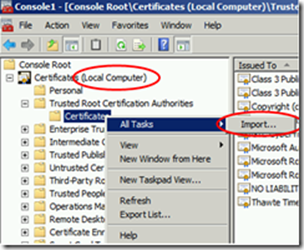
On all machines that are not joined to Domain including the Gateway server the Root CA Certificate must be installed and added to the Trusted root Citification Authorities because these machines don’t trust the Enterprise CA installed before.
To do that, Open MMC
Add you don’t trust the Enterprise CA, and choose Certificates Snap-in
Add both My user account and Computer account
The certificate from the Root CA needs to be added in this list.
Open the web browser on the gateway server, and go to the CA Web service: https://CAserver/certsrv
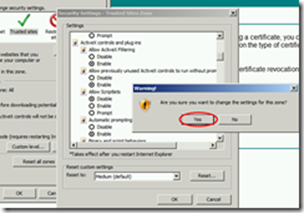
Add the certsrv website to the Trusted Sites.
Since the certsrv website uses ActiveX, change the security settings of Trusted Sites so that ActiveX is allowed.
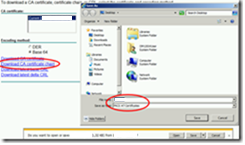
Here we need to request the CA chain
Ensure that ActiveX is enabled.
The certificate is now in the list of Trusted Root Certifications Authorities, meaning our workgroup gateway server will trust certificates issued by the Enterprise Root CA created before.
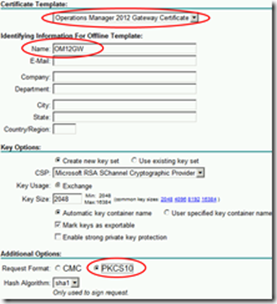
Now we need to request a certificate for our gateway server
Advanced request
Create and submit
Select the template that was created earlier, and fill in the Name and Friendly Name fields with the FQDN of your gateway server.
Since mine is in a workgroup, the NetBIOS name is sufficient.
And now the certificate is generated and we can install it
Done
When you install the certificate, it will be installed in the User store.
But since we are authenticating computer the certificate must be imported in the computer store.
So open the Certificates MMC and export the certificate from the user store and import it to the local computer store.
The certificate is now installed and you can verify if everything is installed correctly by opening the certificate and checking if the certification path is ok.
On the Management Server, we also need to install a certificate. Since we have an Enterprise Root CA, integrated with AD, the root CA certificate is already trusted by our MS that is a domain member.
Now we can start installing the agent on the non-domain machine.
Give the management group name - this can be found in the title bar of the console on the management server - and the management server name; note that you must add in the hosts file the name of the management server and its corresponding IP.
The port number can be changed if desired. By default it is 5723.Only this port needs to be open on the firewall from the non-domain agent to the Management Server.
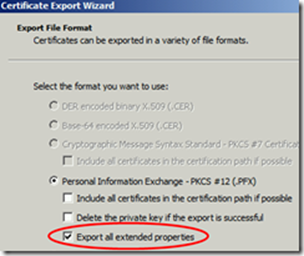
Then we have to Export the created certificate
And import it in the Personal Store of the Computer Account and User Account.
Then copy the MOMCertImport.exe tool to the non-domain agent.
MOMCertImport. execan be found in the SupportTools Folder
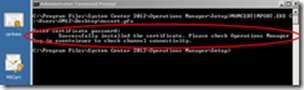
Run MOMCertImport. exe and point to the Imported Certificate
You’ll get a message that the action succeeded, and you can check progress in the Operations Manager event log.
Troubleshooting:
If you get event 21006, make sure the firewalls on the gateway and/or on the management server are not blocking communication
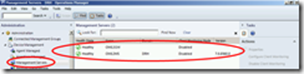
Don‘t forget to enable Agent Proxy for the gateway, as this one will act as a proxy for other systems connecting through the gateway server!
To check if it’s working, go to the Operations Manager Console – you should see something similar to this
Dany Abboud from NEPA PFE team.
Comments
- Anonymous
March 26, 2014
Excellent Guide - Anonymous
May 13, 2014
Easy steps :) - Anonymous
October 21, 2015
Thx , really easy and straight to the point.