Let's Configure Azure Site-to-Site VPN with RRAS in Azure Resource Manager!
UPDATE 12/20/2016: The correct port forwarding rules need to be in place in order for the VPN to work. Here is a link to a blog with more information about which ports need to be configured on the router.
There are several blog posts about configuring an Azure site-to-site VPN with Microsoft RRAS in the old Azure portal. I did find that Cheryl McGuire wrote an article about creating a site-to-site VPN in Azure Resource Manager with PowerShell here. However this post is more specific about configuring RRAS and Azure site-to-site VPN.
In the old Azure portal once you configured a site-to-site VPN it would generate a script that would configure RRAS on a Windows Server. I have not been able to find where or even if that script is created in the new Azure portal. So we are going to manually configure RRAS.
NOTE: In this post I will be disabling IPv6 because it is not used.
Before you begin you will need a Windows Server 2012 R2 that has 2 NICs.
Configuring the RRAS Server's NICs...
Label one NIC to be External and one to be Internal.
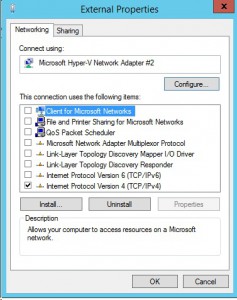
Go into the properties of the External adapter.
- Uncheck everything except for TCP/IPv4.
- Go into the properties of TCP/IPv4 and configure:
- IP Address
- Gateway
- DNS Servers
- Advanced Settings -> WINS -> Disable NetBIOS over TCP
Click OK to close out the External adapter properties.
Go into properties of the Internal adapter.
- Uncheck TCP/IPv6.
- Go into the properties of TCP/IPv4 and configure:
- IP Address
- DNS Servers
NOTE: If you configure a gateway for your Internal adapter then you will need to manually add a static route. This will ensure all traffic is routed through the External adapter. 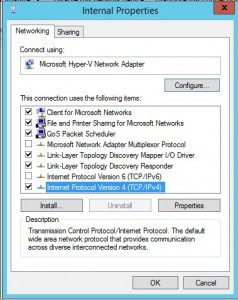 In other articles about setting up a site-to-site VPN with Azure it is recommended that you assign the External IP address in the DMZ on the router. I did not do that because this is just a home lab and it still works fine. However without the External adapter in the DMZ, Azure is unable to initiate the connection.
In other articles about setting up a site-to-site VPN with Azure it is recommended that you assign the External IP address in the DMZ on the router. I did not do that because this is just a home lab and it still works fine. However without the External adapter in the DMZ, Azure is unable to initiate the connection.
Installing the RRAS Roles and Features...
Now that the networking has been configured. Make sure that the server has the latest updates.
Open Server Manager. Select Manage -> Add Roles and Features.
On the Add Roles and Features Wizard
- Before You Begin: Click Next
- Installation Type: Role-based -> Click Next
- Server Selection: Select a server from the server pool -> RRAS-Server -> Click Next
- Server Roles: Check Remote Access -> Click Next
- Features: Click Next
- Remote Access: Click Next
- Role Services:
- Direct Access and VPN (RAS)
- Click Add Features on the pop-up window
- Routing
- Click Next
- Direct Access and VPN (RAS)
- Role Services:
- Web Server Role (IIS): Click Next
- Role Services
- Accept Defaults: Click Next
- Role Services
- Confirmation: Click Install
While that installs let's head over to Azure
Setting up / configuring the VPN in Azure...
NOTE: For this walk-through all resources will be specified in East US. As my own person best practice I place all my resources in the same location.
Go to Virtual Networks and click Add.
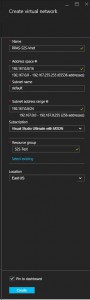
On the Create virtual network blade fill in the following:
- Name - RRAS-S2S-Vnet
- Address space - 10.2.0.0/16
- There will need to be 2 subnets created so the address space here will have to be big enough for your 2 subnets. I am going to have 2 /24 subnets under this to help clarify the differences in the 2 subnets.
- Subnet name - default
- This is the subnet you will use for your Azure VMs.
- Subnet address range - 10.2.0.0/24
- This is the address range that will be used for the Azure VMs.
- Subscription - pick your subscription
- Resource group - S2S-Test
- This is creating a resource group that we will use for the rest of the resources.
- Location - Pick the location you want your Virtual Network to reside.
Click Create.
Next you need to create a subnet for the virtual network gateway. Click on Virtual Networks.
On the Virtual Networks blade click the RRAS-S2S-Vnet network. Then click on All settings -> Subnets -> Add.
On the Add subnet blade fill in the following:
- Name - GatewaySubnet
- This has to be the name of the subnet for the Virtual Network Gateway.
- Address Range - 10.2.1.0/24
- This is the IP range for the RRAS server to use.
Click OK
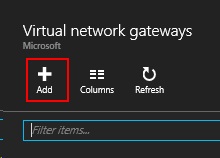
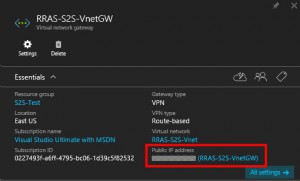
After the Virtual Network is deployed click on Virtual network gateways.
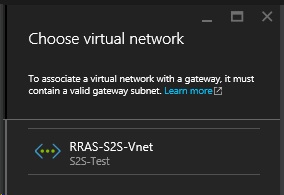
On the Create virtual network gateway blade type in the name of the virtual network gateway, RRAS-S2S-VnetGW. Then click choose virtual network and select the virtual RRAS-S2S-Vnet virtual network.
Back on the Create virtual network gateway blade click Choose public a IP address. Then on the Choose public IP address blade click Create new.
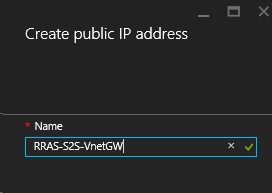
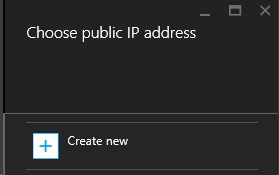 On the Create public IP address blade type in the name for the public IP address resource and click OK.
On the Create public IP address blade type in the name for the public IP address resource and click OK.
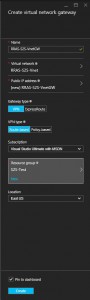
Back on the Create virtual network gateway blade select the following:
- Gateway type: VPN
- VPN type: Route-based
- Subscription: your Azure subscription
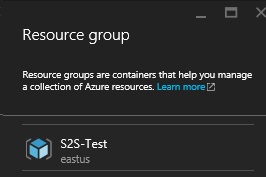
Click on Select existing under Resource group and then on the Resource group blade select the S2S-Test, click OK.
Back on the Create virtual network gateway blade select East US as the Location and then click OK.
Back on the Create virtual network gateway blade review the options and then click Create.
After the Virtual Network Gateway is created select Virtual network gateways and then select RRAS-S2S-VnetGW. The settings blade will appear. Make note of the Public IP address, this will be needed later.
Next go to Local network gateways and click Add.
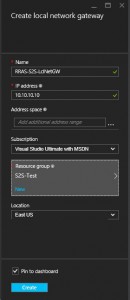
On the Create local network gateway blade enter in the following information:
- Name: RRAS-S2S-LclNetGW
- IP address: Enter the public IP address of network that the RRAS server is on
- Address space: This is where the on prem network address space is set (e.g. 192.168.1.0/24).
- Subscription: Select your Azure subscription
- Resource group: S2S-Test
- Location: East US
Click Create.
After the Local network gateway is created, go to Local network gateways -> RRAS-S2S-LclNetGW-> Settings -> Connections.
Click Add.
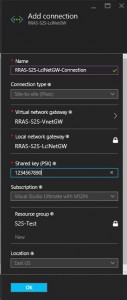
On the Add connection blade fill in the following:
- Name: RRAS-S2S-LclNetGW-Connection
- Connection type: Site-tosite (IPsec)
- Virtual network gateway: RRAS-S2S-VnetGW
- Local network gateway: RRAS-S2S-LclNetGW
- Shared key (PSK): Enter in any alphanumeric key as the key
- Resource group: S2S-Test
- Location: East US
Click OK.
The site-to-site VPN configuration in Azure is now complete.
Now we go back to the RRAS server...
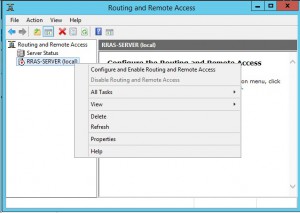
After the install of the Remote Access role is complete, open up Routing and Remote Access.
Right-click the RRAS-Server and click Configure and Enable Routing and Remote Acess.
The Routing and Remote Access Server Setup Wizard will appear.
- Welcome to the Routing and Remote Access Server Setup Wizard: Click Next
- Configuration: Select Secure connection between two private networks, click Next
- Demand-Dial Connections: Select Yes, click Next
- IP Address Assignment: Select Automatically, click Next
- Completing the Routing and Remote Access Server Setup Wizard: Click Finish
The Demand-Dial Interface Wizard will appear.
- Welcome to the Demand-Dial Interface Wizard: Click Next
- Interface Name: Type in Azure S2S, click Next
- Connection Type: Select Connect using virtual private network (VPN) , click Next
- VPN Type: Select IKEv2, click Next
- Destination Address: Enter in the Public IP address of the Azure Virtual Network Gateway, click Next
- Protocols and Security: Check Route IP packets on this interface, click Next
- Static Routes for Remote Networks: Click Add
- Static Route: Select Remote Network Support using IPv4:
- Destination: 10.2.0.0
- Network Mask: 255.255.255.0
- Metric: 24
- Click OK
- Click Next
- Static Route: Select Remote Network Support using IPv4:
- Dial-Out Credentials: Type Azure for the User name, click Next
- Completing the Demand-Dial Interface Wizard: Click Finish
In the Routing and Remote Access window select RRAS-Server -> Network Interfaces. Right-click on Azure S2S and select Properties.
Select the Security tab and under Authentication select Use preshared key for authentication. Type in the preshared key that was entered on the RRAS-S2S-LclNetGW-Connection. Click OK.
Right-click on the Azure S2S network interface and click Connect.
After it connects open up a command prompt and ping 10.2.0.0. You should get a response.
Now any Azure VM that you put on RRAS-S2S-Vnet will be able to communicate directly with your on-premise systems.
In order for any on-premise systems to communicate with the Azure VMs you will need to either setup a route for the Azure subnet to route through the RRAS server or set the gateway on your systems to be the RRAS server.
Troubleshooting
If you can connect to the VPN but cannot ping the Azure network then make sure that the route to your Azure external IP is set correctly. You can view this by right clicking on static routes under IPv4 in RRAS. Then select Show IP Route Table. If you do not see your Azure Public IP listed and going to the External network adapter then you need to manually add the route.
Comments
- Anonymous
June 20, 2016
Hi thereThe VPN is UP but"After it connects open up a command prompt and ping 192.167.0.0. You should get a response."No response to the ping and can't connect to any VMAny troubleshooting advice ?ThanksK- Anonymous
July 05, 2016
Verify that under IPv4 -> Static Routes, that your static route is set to use the Azure S2S interface and that the destination IP/subnet information is set correctly. - Anonymous
July 14, 2016
I had this problem and I fixed it by setting a static IP for the demand-dial interface. RRAS > Network Interfaces > MyDemandDialInterfaceName : Properties > Networking > Ipv4 : Properties > "your IP configuation data" - Anonymous
August 01, 2016
Yep - that was it!! I can Ping All Address in the 192.167.X.X network. I also had to set the static ID for the Dial Up Adapter on the Network Interfaces as Alan described. When you go into the "properties" of the adapter it will be set to use an assigned IP Address. I changed it to 192.167.0.1 and it connected and was able to ping other addresses. I hope this helps someone else
- Anonymous
- Anonymous
August 09, 2016
Spectacular blog! Thank you! - Anonymous
August 11, 2016
I can ping 192.167.0.0 using Alan's suggestion. However I can ping azure VMs nor can azure VMs ping anything on premise. I am certain I missed something but can't seem to figure out what. Both azure VMs can ping each other. Should I be able to ping Azure VMs from the RRAS server?- Anonymous
August 19, 2016
I am having the same issue, site to site is working but I cannot ping from onprem to azure and vice versa. Any idea anyone?- Anonymous
August 19, 2016
The VM has a Network Security Group associated with it just like the virtual network. So you have to go into the VMs NSG and add a rule in to allow ICMP.- Anonymous
August 22, 2016
The comment has been removed- Anonymous
August 22, 2016
Go to the NSG for that server and make a rule to allow RDP traffic. If the server does not have an NSG associated with it then it is the Windows Firewall. Verify that the Windows Firewall is configured correctly. If you are connected try connecting to remote desktop from the RRAS server by way of the internal Azure ip of the Azure VM.
- Anonymous
- Anonymous
August 22, 2016
Hi, There is currently no NSG applied to the VM on Azure. But that does not explain why from Azure I cannot ping on prem (RRAS) server. Any clue?- Anonymous
August 22, 2016
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
August 30, 2016
Hi, Thanks for your assistance but I am still not able to ping or RDP from onprem to azure and vice versa. I checked and my site to site is connected. I had also checked the onprem firewall as well as the azure server firewall, I had tried with and without NSG with RDP enabled but nothing seem to work. Do you have any clue what else I might be missing or I had misconfigured?Regards.- Anonymous
August 31, 2016
Can you ping 192.167.0.0?- Anonymous
August 31, 2016
Yes I can, It seems that now I can ping from Azure to onprem but not the other way around.- Anonymous
August 31, 2016
If you can ping one direction then packets are flowing. It sounds like it is either a routing issue or firewall issue. Try setting your RRAS server as the GW server on another onprem server.- Anonymous
September 12, 2016
I have attempted all the checks listed in the responses and am still unable to get any pings to work to any resources either on premise or Azure based. Also, any reason as to why to even get ping to work to 192.167.0.0 a Static IP needs to be assigned to the Network Interface Azure S2S?Any help would be appreciated - thanks! - Anonymous
September 13, 2016
Pinging 192.167.0.0 is just to show connectivity has been established between on prem and Azure. The Azure S2S interface in RRAS is where you put the public IP address in your Azure Virtual Network Gateway, this is just telling RRAS the properties of the Azure Virtual Network Gateway's public IP and how to connect to it.Are you doing this from your home or from an office? If in the office, check to ensure network devices are allowing traffic. - Anonymous
September 13, 2016
The comment has been removed - Anonymous
September 16, 2016
Remember that if you want to ping from Azure to on prem that your on prem system’s gateway must be set to the RRAS server’s internal network adapter’s ip address. The address space on the local gateway can be set to the on prem network space. It might help with some so I’ll make note of it in the blog.The dial on demand should have always been set to DHCP. Setting that up is the last thing that is done and it doesn’t say anything about setting a static IP. Some others have set it but mine is set to DHCP and everything is working without any issue.
- Anonymous
- Anonymous
- Anonymous
- Anonymous
December 22, 2016
Please look at this blog for port forwarding information that is needed in order to make this work. https://blogs.technet.microsoft.com/rrasblog/2006/06/14/which-ports-to-unblock-for-vpn-traffic-to-pass-through/
- Anonymous
- Anonymous
September 06, 2016
When you say to create a local network gateway and use the Public IP of the network the RRAS server is on, your example shows a Private IP address and the GatewaySubnet (192.168.1.0/24) is not part of the virtual network's address space (192.167.0.0/16).What kind of black magic is this?- Anonymous
September 07, 2016
The local network gateway is where you tell Azure about your on prem network. The IP address I use in the example (10.10.10.10) is a representation of the your on prem public ip address. The 192.168.1.0/24 is the on prem network address space that your on prem servers are on. The 192.167.0.0/16 is a network space in Azure that your Azure VMs will be a part of.
- Anonymous
- Anonymous
November 10, 2016
Hi JLetsch, can I use Windows Server 2012R2 RRAS at HA scenario?- Anonymous
November 14, 2016
Do you mean run RRAS on a 2012 R2 cluster? If you are, check out this link https://technet.microsoft.com/en-us/library/jj134175%28v=ws.11%29.aspx
- Anonymous
- Anonymous
December 20, 2016
Please look at this blog for port forwarding information that is needed in order to make this work. https://blogs.technet.microsoft.com/rrasblog/2006/06/14/which-ports-to-unblock-for-vpn-traffic-to-pass-through/ - Anonymous
December 28, 2016
The last sentence saved me:). I had to reset my router, and forgot that I had added a route in their previously. Took me until this article to remember, thanks for writing that point down!- Anonymous
April 21, 2017
You're welcome. Glad it helped.
- Anonymous
- Anonymous
February 15, 2017
Hello everyone,I've set up everything and it shows it is connected on both ends on RRAS and and Azure but I cannot ping anything form azure to on prem and from on local to azure!! Do you have nay idea my LAN is behind Juniper SRX firewall do I need to setup a rule for core firewall?- Anonymous
February 16, 2017
I would start with reviewing the Juniper SRX firewall logs and rules to see if it is blocking traffic. The link at the top of the page has the firewall port information needed for the connection.
- Anonymous
- Anonymous
May 24, 2017
Hi all, The vm on azure able to print onprem RRAS.However the RRAS unable to ping Azure vm.I have removed NSG, firewall, iptables.static route has also been assigned on the RRAS and also assign an azure ip on the vpn interface.What is next ?- Anonymous
May 24, 2017
It sounds like the issue is with the Azure. It could either be the Azure VM is not responding to ping because of firewall (but you said you removed that), or the gateway in Azure doesn't know the route back to your RRAS server. Try doing a trace route on both sides and see where the packets drop. Also you could gather Wireshark data on both side too and see if the Azure VM is responding but the packets are being lost at your gateway.- Anonymous
May 24, 2017
Thank you for your information.Will the azure gateway drop the ping( which is response back) package, even the Azure vm can ping the onpremise ?How can we control the routing issue on the azure vpn gateway?Thanks so much
- Anonymous
- Anonymous
- Anonymous
May 30, 2017
192.167.0.0 is a public network id right? You need to buy that range right?- Anonymous
May 30, 2017
You are correct that it is part of a public IP space. I used it for an example purpose here so that there would be a visible distinction between Azure and Onprem. You can set it to be that IP space without any issues other than if you are trying to access a public resource within that same IP range. Thanks for pointing that out, I will update it to reflect another designated private IP space.
- Anonymous
- Anonymous
September 11, 2017
Hi,Thanks for your step by step guide & I have completed this successfully. But one problem is that my hyperV vm's are unable to ping azure vm's. Can you help me on this- Anonymous
September 12, 2017
Can your hyper-v vms ping the .0 of the azure network? Did you try a tracert to see where the drop is?
- Anonymous
- Anonymous
February 05, 2019
Create The guide as a code, with Terraform - https://github.com/vizel014/Terraform-Azure-Vpn-RRAS.git - Anonymous
April 14, 2019
It Works! Great Share! Thanks!