Understanding workstation analysis and security policy
Workstation analysis and security policy are the key features proposed by UAG to provide security at the application layer. Whereas firewall will operate at the network layer (filter by IP or TCP Port range), the application layer will look at “what” the user is trying to do and will correlate a lot more information in order to say ALLOW or BLOCK. This is definitely more powerful in terms of security especially when you expose application and “data” (documents, web page, …) that are very valuable for you, and so for criminal organization.
As a security architect, the methodology we propose with UAG is the following (based on risk analysis) :
1) Understand the assets of a specific application that we want to expose: during this phase, you will identify the data (documents, web pages containing data, …) for each published application and identify the “value” of each. If this data is valuable (a document with fusion acquisition information, finance, new research formula, ..) then the risk of having “someone” (a hacker) trying to steal this document is very high. IP and TCP filtering will not help you a lot.
2) Once you understand where and what is the risk, you identify the potential ways to reduce this particular risk. For example, documents marked “security level CONFIDENTIAL” can be downloaded (read) only from “Corporate machines, with OS up-to-date, with bit locker activated”.
3) Once you understand what to do, you translate this security policy in an “UAG security policy” via the administration console, and link that policy to that particular application, for that particular action (see type of security policies below).
Note: with UAG you can define security policies “per application”. The reason is that the way you will secure application A is not the same as the one you will secure application B. These 2 applications could require totally different security policies. With UAG you can adjust precisely the security policy, on a per application basis.
The UAG security policy will define the list of “checks” that you want perform for a specific application and for a specific action. For example download a file from ‘Sharepoint Research and Development’ site, where file is located in the ‘/Confidential directory’ is seen as user action by UAG. Once it detects that “action”, it will first verify if the security team has set a “security policy” for that action. If there is one, it will then check if the machine is in a “state of security” that allows this access.
To determine this “state of security”, UAG will use the result of the workstation analysis (called endpoint check) done even before the user authenticated (this process is almost invisible, take less than a second, and by default will perform more than > 200 checks).
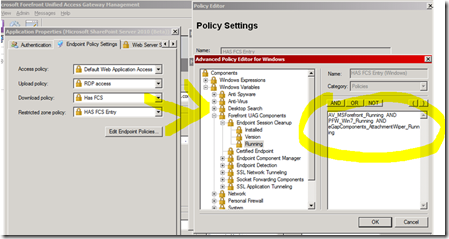
As an example of this, below you can see that for an application named “Microsoft Sharepoint Server 2010”, we have set a security policy named “HAS FCS”. This security policy will be evaluated by UAG when user tries to “DOWNLOAD” a file. This security says that “Forefront AV has to be running, that Windows 7 firewall has to be running, and that UAG Attachment wiper component has also to be running. At the left of the “Advanced Policy Editor” you can find the + 200 variables gathered by UAG, and just need to drag and drop the relevant one to create your own policy.
With UAG you can intercept 5 different levels of security policies, one at “portal” level, and 4 at application level.
The first security policy you can set is in fact the one that authorize the user to see the login banner. If you decide for example to create a Portal only for employees, and decide that “only corporate machines” have the right to connect this portal, then you can set a policy named “Session Access Policy” (Advanced Trunk configuration, Endpoint Access Settings TAB).
The 4 other ones are at application level, and can be different for each application published in the portal.
Here is the list (Open an application, EndPoint Policy Settings TAB) :
· “Access” : the ability, if not compliant, to display the application in the UAG portal, but this application is grayed out (don’t hide it, otherwise users will call support center ;-). A “details” option appears where you can put any kind of text, picture or even video, where you explain user “why” this is grayed out and “how” to fix the problem themselves.
· “Upload” and “Download” : these 2 actions are very explicit, but notice that for “OWA” (or other web mail) this notion is the ability to send or receive an attachment.
· “Restricted zones” : this one is very interesting. You can define “parts” of a web site (in our example, the “/CONFIDENTIAL” directory) as “restricted zones” and put an extra security policy. For example, all employees can access the “Research and development” Sharepoint site, but in order to access that particular directory (valuable document) you must be compliant with a stronger security policy ( corporate machine + up-to-date + bitlocker..). This way, even if someone steals your laptop, data is protected by bitlocker. This provides a very granular access where you always put the “best” security policy possible for an action.
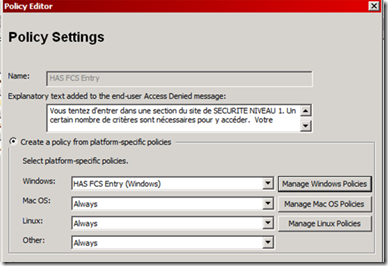
It is important to notice that UAG tries to cover a large range of scenarios, which means the ability to handle all kind of user Operating Systems such as Windows, Macintosh and Linux (Mobile do not propose today abilities to analyze endpoint unfortunately). This means that an “ UAG Security policy” contains in fact “sub security policies” for each kind of OS, just because security products are not the same for each of them (Popular Linux Firewall are not the same as the one in Macintosh and Windows world) :
By default UAG will perform > 200 checks, but the “number of checks” is not in fact professional criteria in terms of security. What we want is to find “The appropriate checks that will make the application secured”. If among this long list of checks proposed by UAG one is missing for your particular scenario, you can easily add your own checks by simple Visual Basic Script.
Check my blog for examples of this, this is very easy, and EXTREMLY EFFICIENT in terms of security.