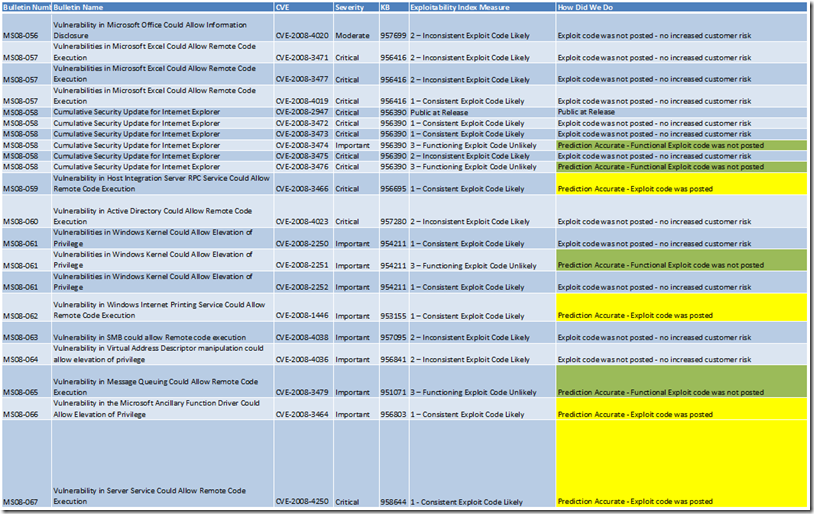
One Month Analysis: Exploitability Index

Handle:
Silver Surfer
IRL:
Mike Reavey
Rank:
Director, MSRC
Likes:
Warm weather, Battlestar Galactica, and responsibly reported vulnerabilities
Dislikes:
Rain, Rain without end, Clouds with potential for rain, reality TV, and unpatched vulns
Hey folks –
We’ve just released the November Security Bulletins and that also marks the one-month point after the release of the initial Exploitability Index in October. As a result, we’ve had a several questions from customers on “how’s it working?” Well, so far, based off the results from October, and feedback from Microsoft Active Protections Program (MAPP) partners who help check our work before release – it seems to be going pretty well.
October was a large release, with 12 Security Bulletins resolving 21 vulnerabilities, one of those being an out-of-band release.
First – our main measure for success is to make sure we avoid rating something in the index “lower” than it actually should be once under full public review. This is our main concern because it means that customers would be at an increased level of risk than we communicated by the index. The good news is, one month after release, we’ve not had any issues that fall into this category. This also means, that for the four vulnerabilities we gave our lowest ratings, we haven’t seen functioning exploit code in the first 30 days. These include:
- MS08-058 - CVE-2008-3474 - Cumulative Security Update for Internet Explorer
- MS08-058 - CVE-2008-3476 - Cumulative Security Update for Internet Explorer
- MS08-061 - CVE-2008-2251 - Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege
- MS08-065 - CVE-2008-3479 - Vulnerability in Message Queuing Could Allow Remote Code Execution
There were also four security vulnerabilities where we anticipated consistent and functioning exploit code would be released publicly (excluding CVE-2008-2947, which was public at bulletin release), and for which this prediction came true. These include:
- MS08-059 – CVE-2008-3466 – Vulnerability in Host Integration Server RPC Service Could Allow Remote Code Execution
- MS08-062 – CVE-2008-1446 – Vulnerability in Windows Internet Printing Service Could Allow Remote Code Execution
- MS08-066 – CVE-2008-3464 – Vulnerability in the Microsoft Ancillary Function Driver Could Allow Elevation of Privilege
- MS08-067 – CVE-2008-4250 – Vulnerability in Server Service Could Allow Remote Code Execution (this was the out-of-band-release)
For each of the aforementioned issues, functioning exploit code was released publicly within the first two weeks. Customers using the index to help make deployment decisions would have been able to anticipate this, prioritize these updates over others, and roll them out within their environment. Before we had the Exploitability Index and providing this additional layer of analysis, these security bulletins would have had no special indication that attacks were likely.
This is probably the most significant impact the index can have, as we’ve always said it’ll never be 100% accurate, but that the goal is to give valuable information to help customers make prioritization decisions.
For the remaining five issues that were rated “1 – Consistent Exploit Code Likely,” we’ve not seen functioning exploit code posted publicly. While this may seem like we’re wrong in the prediction, we actually feel pretty good about this.
Let me explain: Some customers express concern that when we released the Exploitability Index, by observing the environment, we’d be changing it. Basically, they were worried that we’d raise the amount of exploit code present in the ecosystem by highlighting the issues most likely to have exploit code developed.
So even though we think it’s likely that functioning exploit code could be released for the remaining seven, the fact it hasn’t means that we’ve not significantly changed the threat environment in a negative way. And we haven’t told customers to worry less about a given vulnerability when in fact, they should have. In fact, it may even be that the increased attention led to faster deployments to protect against these vulnerabilities and that in turn made these less attractive.
A full list of all the vulnerabilities, Bulletin Severity Ratings, and Exploitability Index ratings, along with “how we’ve done” is listed below. As always, you can find the Exploitability Index on the Security Bulletin Summary page each month. You can even find additional supplemental information by referencing our Frequently Asked Questions and How to Use the Exploitability Index on several Microsoft Web sites.
We’ll continue to watch how we’re doing in providing this information, make an effort to engage more with the community to help us check our work.
However, one month in, based on the data and feedback from customers, it looks like the Exploitability Index is panning out to be a very helpful tool for customers.
- Mike Reavey
| Share this post : |  |
*Postings are provided "AS IS" with no warranties, and confers no rights.*