SPO Tidbit - Securing the Site Collection
Hello All,
I will assume that you have set the permissions on your Site Collections correctly, but if that still leaves the security team uncomfortable we can always look to perform several other steps using Conditional Access and SharePoint admin.
The Microsoft team approaches this by classifying 3 types of sites Baseline, Sensitive, and Highly regulated each one escalating from the previous (Well actually there is a 4th which is public with minimal security). Here are those levels
| Protection level | Policies | More information |
|---|---|---|
| Baseline | Require MFA when sign-in risk is medium or high | Include SharePoint Online in the assignments of cloud apps. |
| Block clients that don't support modern authentication | Include SharePoint Online in the assignments of cloud apps. | |
| Define app protection policies | Be sure all recommended apps are included in the list of apps. Be sure to update the policy for each platform (iOS, Android, Windows). | |
| Require compliant PCs | Include SharePoint Online in list of cloud apps. | |
| Use app enforced restrictions in SharePoint Online | Add this new policy. This tells Azure AD to use the settings specified in SharePoint Online. This rule applies to all users but only affects access to sites included in SharePoint Online access policies. | |
| Sensitive | Require MFA when sign-in risk is low, medium or high | Include SharePoint Online in the assignments of cloud apps. |
| Require compliant PCs and mobile devices | Include SharePoint Online in the list of cloud apps. | |
| SharePoint Online access control policy: Allow browser-only access to specific SharePoint sites from unmanaged devices | This prevents edit and download of files. User PowerShell to specify sites. | |
| Highly regulated | Always requrie MFA | Include SharePoint Online in the assignments of cloud apps. |
| SharePoint Online access control policy: Block access to specific SharePoint sites from unmanaged devices | Use PowerShell to specify sites. |
And of course you need to setup the Site-Scoped limited access policies for SharePoint Online and OneDrive for Business. These policies utilize the device-based policies for SharePoint and OneDrive (Released Mar 2017) to help administrators ensure data on corporate resources is not leaked onto unmanaged devices such as non-domain joined or non-compliant devices. This is done by limiting access to content to the browser, preventing files from being taken offline or synchronized with OneDrive on unmanaged devices.
There are two things you need to do to configure these Site level policies
1. Tenant-level device-based policy must be configured to Full Access
2. Run the following script for each Site Collection you want to enforce the policy on
Connect-SPOService -Url
$Site = Get-SPOSite -Identity
Set-SPOSite -Identity $Site.Url -ConditionalAccessPolicy AllowLimitedAccess
You can also use the following values for the parameter 'ConditionalAccessPolicy': AllowFullAccess, AllowLimitedAccess, BlockAccess
While it might seem counterintuitive to allow external sharing, this approach provides more control over file sharing compared to sending files in email. SharePoint Online and Outlook work together to provide secure collaboration on files.
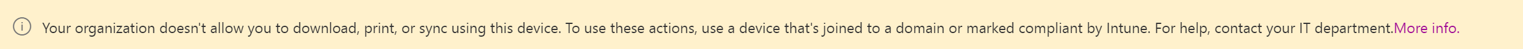
Now if a user connects to a Site Collection via an unmanaged/non-compliant device they will see a banner like this:
Note:
If access is limited or blocked to unmanaged devices, this impacts external users too, though you can can exempt them from this policy by running the following cmdlet:
Set-SPOTenant -ApplyAppEnforcedRestrictionsToAdHocRecipients $false
If you cannot see the Device Security Tab you need to enable MDM (See above for what this means) follow this article to enable and go thru settings
Pax