Adding groups to an Azure Active Directory domain
I wrote about creating a user in an Azure Active Directory domain or adding users to the Azure Active Directory domain here, but now I want to add some groups. Both of these articles are in preparation for an ASP.NET application I will write as an example for how to implement role based security into an ASP.NET application using Azure Active Directory. An important point to realize is that you, as a developer must code that control into your application, the Azure Active Directory feature only provides authentication based on provided credentials and authorization based on group membership. You, the developer need to wrap features and data within your application with code that prevent unauthorized or unauthenticated clients from accessing your application.
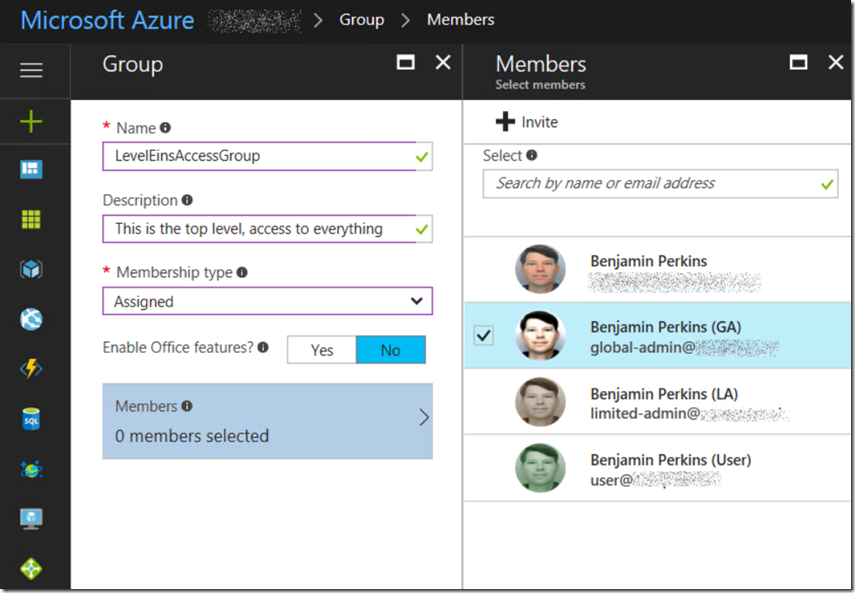
Anyway, adding a few groups is simple, just like adding some users to the Azure Active Directory. Make sure you are in the correct Azure Active Directory domain you want to add the groups to and select the Add a group link which will open the Group blade as seen in Figure 1.
Figure 1, add a group to an Azure Active Directory domain
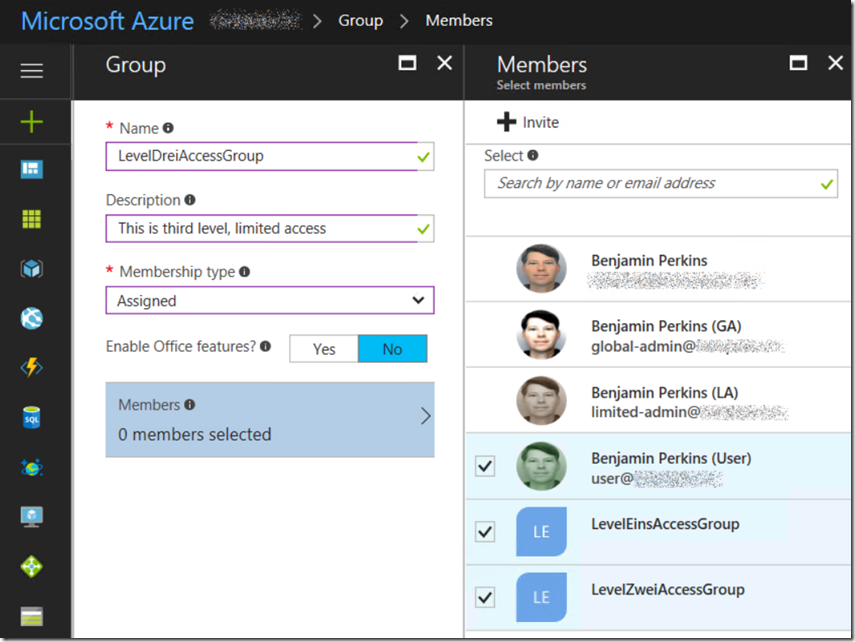
While I was at it, I added my global-admin user I created in the article to the LevelEinsAccessGroup. I added 2 more groups and added at least 1 user to that group. To make it interesting, as I went from level eins (1) to level drei (3) I added each of the higher level groups to the lower level groups, as seen in Figure 2.
Figure 2, add a group to an Azure Active Directory domain, add groups to groups
This is better than adding individuals to each of the group, it means that a user added to group LevelEinsAccessGroup also has access to all the features granted to group LevelDreiAccessGroup. From an administration perspective, then if I need to remove a users access from the application where I have implemented this security model, I would only need to remove the user from 1 group and not need to look through all 3 groups to see if that individual has access.
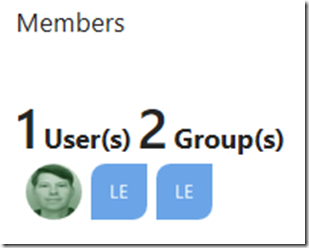
Now I have created 4 users which are assigned to both Azure Roles and 3 or more custom security groups. Figure 3 shows that LevelDreiAccessGroup contains 1 user and 2 groups.
Figure 3, how to view users and groups contained within an Azure Active Directory group
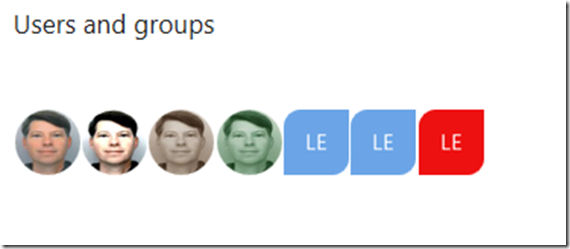
And Figure 4 shows that I have 4 users and 3 groups. Cool stuff, but I might want to consider adding some picture to the group or name them more different so it is more intuitive which group is which…for later days
Figure 4, how to view users and groups contained within an Azure Active Directory group
Now let’s go write some code!
Comments
- Anonymous
May 08, 2019
Hi,If the user is within subgroup, does authorize[maingroup] in asp.net core would check for user within subgroup?Thanks,