Operations Manager 101: How do I create a rule to be alerted on a scenario such as a user been added to domain admins?
Note this is part of a System Center 2016 – Operations Manager and Operations Management Suite (OMS) 101 Series: https://aka.ms/101
NOTE: The event we are watching out for is this one in the security event log. Note that when you view the 'Event Data' in the Details of the Event Properties, you will see a list of parameters which can be used as criteria in SCOM in the same numerical order in which they appear in the event
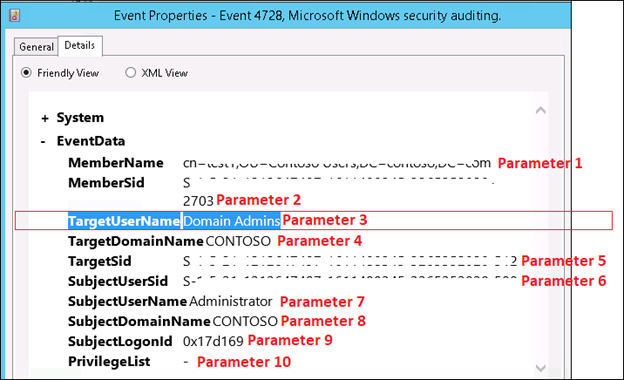
When you get to this dialog when creating a rule or monitor based on a Windows Event, you will be able to specify one of these numbered parameters:
ADDITIONAL NOTES FOR CREATING RULES BASED ON SECURITY EVENTS:
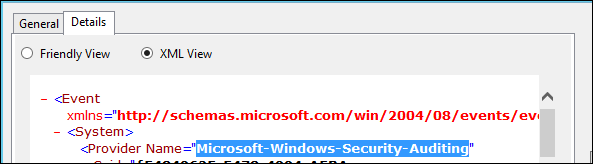
- If you're using Source as Criteria in the rule, you need to specify 'Microsoft-Windows-Security-Auditing' (with the hypens but without the surrounding quote marks, as specified as the Provider Name in the XML view of the event properties:
- When you're picking a target, if you're monitoring for an event only created on DCs, a good target would be windows domain controller or domain controller 20xx depending on the version of your DCs.
- When you pick the event log, it doesn't matter if you do it on the local computer or navigate to a different computer in order to select the 'Security' event log. The only thing we take away from the selection made within that dialog is the event log name – not the computer you picked the log from. We took care of where the rule will become active by picking the target in the earlier dialog.
- If you want to target a single machine / subset, best practice is to target it to something common to the machines you will want to target (such as windows computer / or even better windows 2012 computer / operating system) disable it by default when you create it, and then override enable for the individual instances or a group of instances.
- Bear in mind Event IDs, sources, parameters etc. can differ between version, so you may need to create multiple rules with different parameters for different versions, targeted to the appropriate OS instance.
- You can create either an event collection or an alert generating rule – an event collection rule will just collect the event and then event views need to be created in order to see them. An alert-generating rule will create an alert from which an email notification can be configured.
- The following links list Security Event Details for Events that occur when a given Security Scenario occurs. This is useful for creating Security auditing style event-collection or alert-generating rules (or both): /en-us/windows-server/identity/ad-ds/plan/appendix-l--events-to-monitor
- Some of the most popular collected / monitored Event IDs from this list are as follows:
| Event ID | Event Summary |
| 4625 | An account failed to log on |
| 4720 | A user account was created |
| 4722 | A user account was enabled |
| 4723 | An attempt was made to reset an account's password |
| 4728 | A member was added to a security-enabled global group |
| 4740 | A user account was locked out |
| 4756 | A member wwas added to a security-enabled universal group |
| 4767 | A user account was unlocked |
Steps to create the Alert generating Rule:
1) Launch the Operations Console

2) Click the 'Authoring' space on the bottom left hand side.
3) Right-click Management Pack Objects>Rules (you might need to left-click to expand management pack objects first) and choose 'Create a new rule'
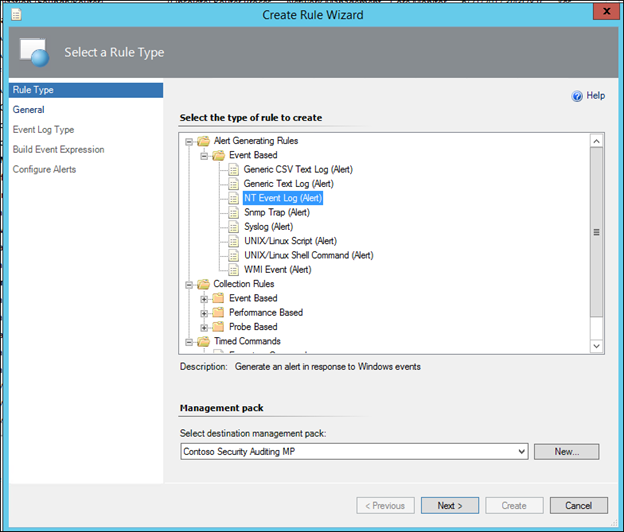
4) In the dialog, expand Alert Generating Rules>Event based
5) Click NT Event Log (Alert)
NOTE: A Golden rule of Operations Manager is to NOT store anything in the Default Management Pack. See this post for additional explanation and guidelines on MP best practice - https://blogs.technet.microsoft.com/antoni/2013/10/09/system-center-service-manager-operations-manager-management-pack-and-naming-convention-best-practices/
6) Change the Management Pack from <Select Management Pack> to an appropriate Management Pack. If there is an MP where all the company's custom rules and monitors are stored (or even better an MP where the organization's AD or Auditing Rules / Monitors are stored) , then select it from the dropdown. If not Create a new Management Pack by clicking the New button, give it a name, hit Next and Create)
7) With Alert Generating Rules>Event Based>NT Event Log(Alert) and the appropriate Management Pack selected, click Next:
8) Give the rule a name (For Example: 'Contoso Alert generating Rule for User Added to Domain Admins 4728 Event')
NOTE: It is best practice to use some form of prefix or three-letter acronym as a naming convention, to identify all of an organization's custom rules and monitors. This makes it much easier to find custom rules in the console when necessary. In this example, I am using 'Contoso'
9) Click the 'Select' button next to the Rule target box and choose an appropriate target such as 'Active Directory Domain Controller Server 2008 Computer Role' or 'Windows Domain Controller' and click OK.
NOTE: Prior to creating the rule, you may wish to navigate to discovered inventory and change the target type to the class you plan on targeting, to verify that instances of that class exist, and are what you wish to target:
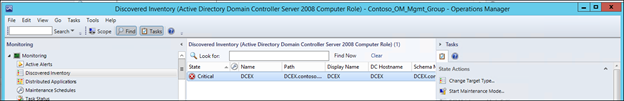
NOTE: Because the 4728 event will only occur on domain controllers, it is appropriate to target the rule to the Active Directory domain controller Server 2008 Computer Role object. If the event could occur on any windows 2008 computer, use 'Windows Server 2008 Operating System' as your target. If it could occur on domain controllers of multiple versions (2008 and 2012), you could choose Windows Domain Controller. Best practice is to be as specific as possible, and to never target a group.
NOTE: Start typing the name of the object desired in the 'Look For' box to narrow the list down, and If the object cannot be found, click the 'View all targets' radio button.
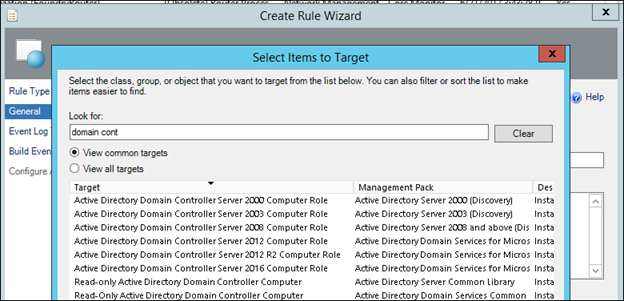
NOTE: If you don't see the 'Active Directory' classes listed above, you probably do not have the Active Directory Management Pack imported, and therefore need to import it, in order for these classes to become available. Alternatively, the class 'Windows Domain Controller' is available out of the box and you could use that class. Just be aware that every windows domain controller will be monitored with this rule if it is enabled against that class.
10) Leave the default of 'Alert' as the Category, but uncheck 'Rule is enabled' and then click Next:
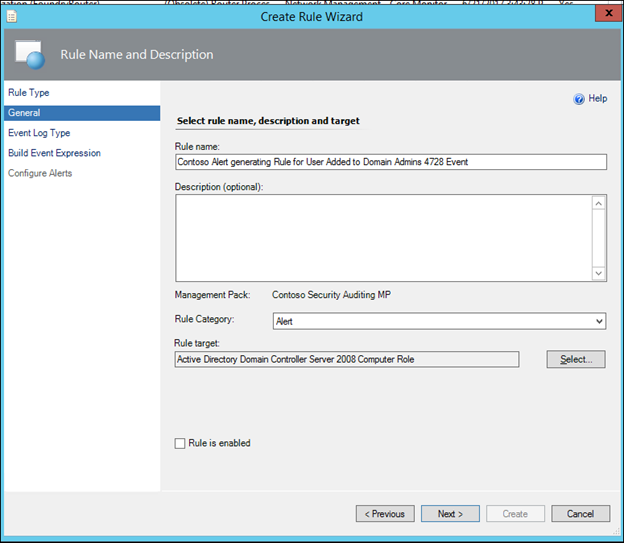
NOTE: It is my preference to ALWAYS disable a custom rule / monitor by default and then enable it with an override (rather than using the checkbox in the General page shown above) as once we enable it with an override, this will ensure the custom rule / monitor is visible in my Authoring>Overrides view along with all my other rule / monitor / discovery (in Sealed and or Unsealed MPs) configuration changes.
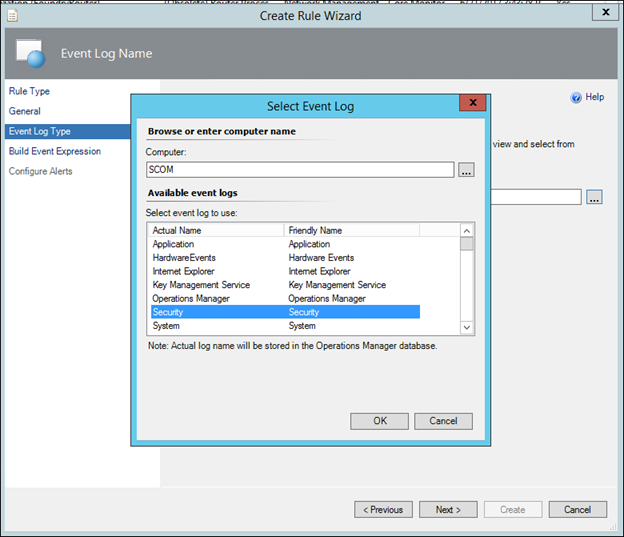
11) In the Event Log Name, type the word Security, or alternatively, click the 3 dots and select the Security Event Log, and click Next.
NOTE: This is nothing to do with the targeting. This is purely to make sure you get the name of the event log correct with no typos. The Rule will look in the selected event log on every object found for the class you selected to target (e.g. every windows computer or domain controller) that has the selected event log.
12) In the Value box to the right of Equals on the Event ID line, type 4728

NOTE: If you wish to monitor for a separate Event, simply specify the alternative Event ID here.
13) Click the grey cell next to Event Source (the second line) and click the Delete button in the UI
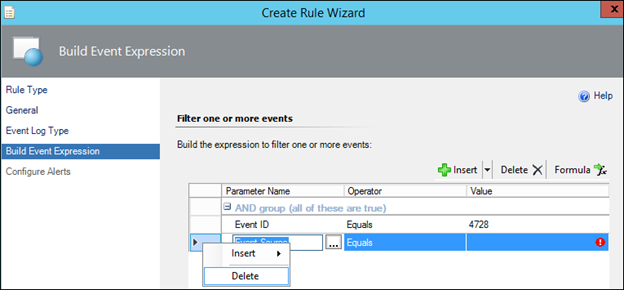
14) Click the Insert button (the main button not the drop-down section of it) and then click the 3 dots on the new line that appears

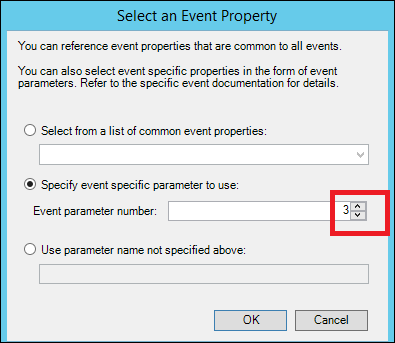
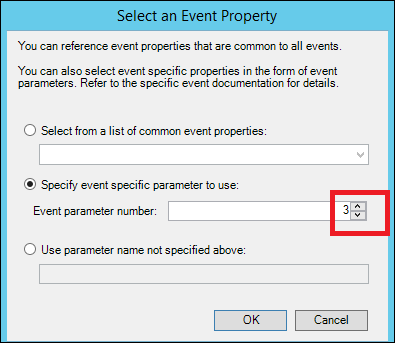
15) In the 'Select an Event Property' dialog' chose 'Specify event specific parameter to use' and change the value from 1 to 3 and click ok:
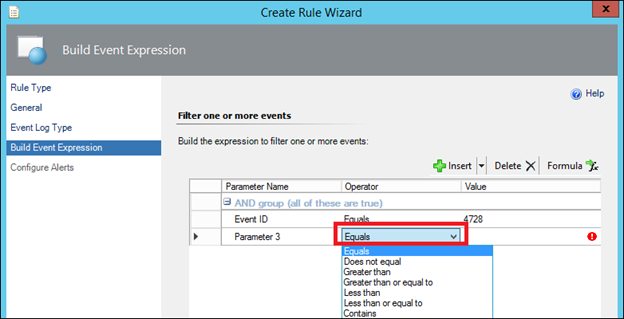
16) In the operator field on the second line choose Equals
17) In the value field on the 'Parameter 3' Line, type Domain Admins (Case-sensitive):
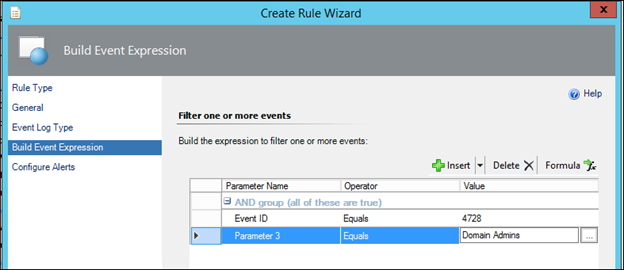
NOTE: For monitoring users added to a group other than Domain Admins, simply type the Alternative Group name in place of Domain Admins. As well as Equals, other operators such as 'contains substring' or 'Matches Regular Expression' are available. Using a regular Expression, you could type a list separated by pipe symbols for example Domain Admins|Enterprise Admins|Really Secure Admin Group
18) Click next.
19) In Alert name either leave the rule name as the default (the rule name), or change this to a more meaningful string such as 'Contoso - User Added to Domain Admins'
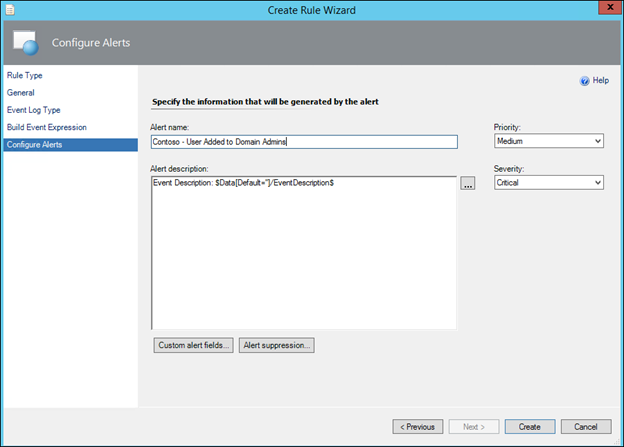
NOTE: the next 2 steps are optional. By default, only the contents of the event description will be displayed. Carrying out the optional step below will deliver a more meaningful phrase at the top of the alert description:
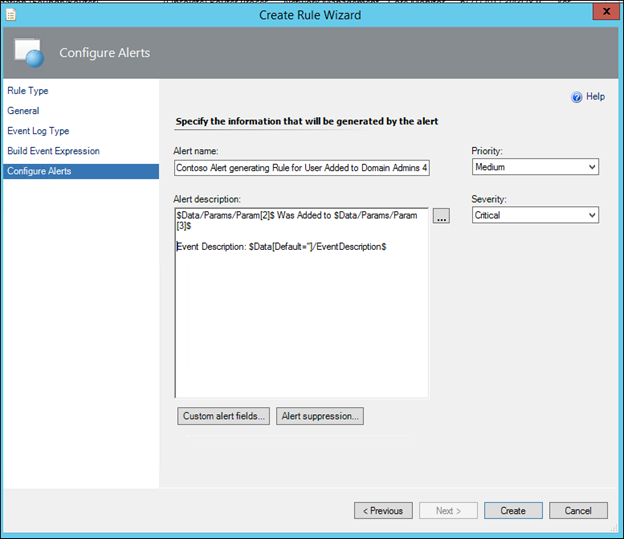
Optional Step) In Alert description, click at the start of the box (before Event description) and type $Data/Params/Param[2]$ Was Added to $Data/Params/Param[3]$
and the result should look like this:
$Data/Params/Param[2]$ Was Added to $Data/Params/Param[3]$
Event Description: $Data/EventDescription$
Optional Step 2) Click the Custom Alert Fields button and add a 'tag' such as Contoso Security Auditing and click Ok
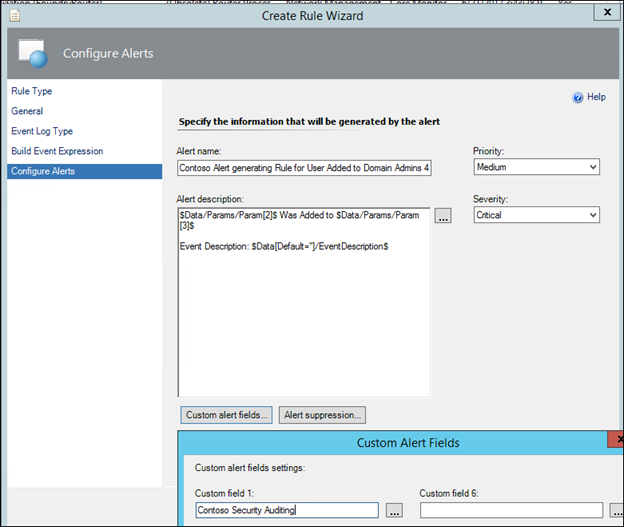
NOTE: If you had a series of security auditing rules you were creating, set them all up this way with the same custom field and then we can refer to this collection of rules easily for inclusion in a view and / or subscription, using this custom alert field as criteria.
20) Change the Priority and Severity if desired and click Create.
21 In the Authoring>Rules pane, find your rule using the 'look for' box:
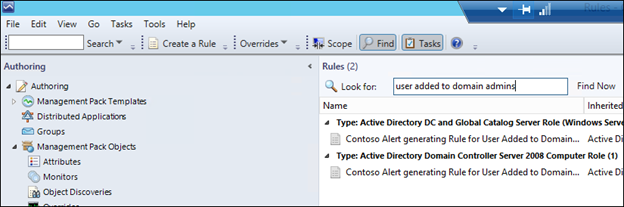
22) Right click the rule as it appears under the class you targeted and choose to override for all objects of the class:
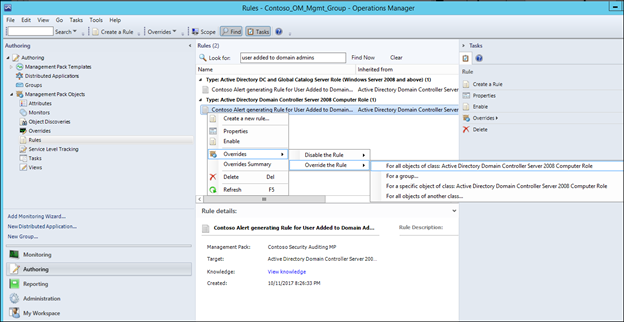
NOTE: It is the same rule showing twice, because Active Directory DC and Global Catalog Server Role (Windows Server 2008 and above) is a type of 'Active Directory Domain Controller Server 2008 Computer Role (inherited from that) so also inherits the rule.
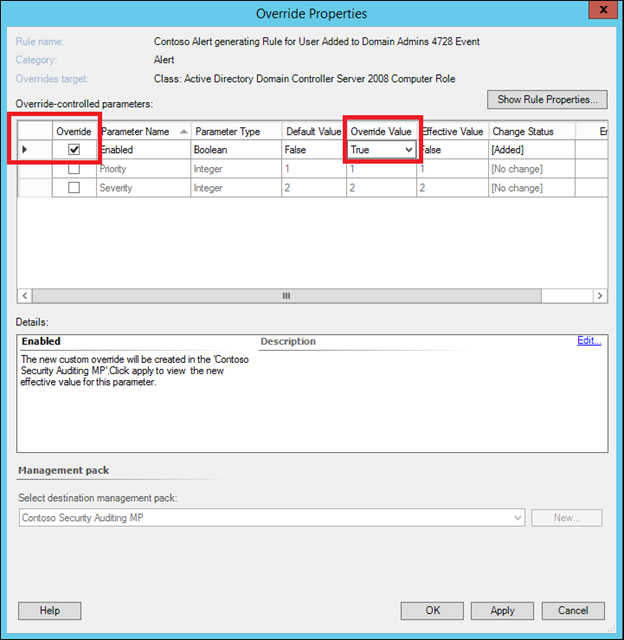
23) Check the checkbox in the 'Enabled' row, change the Override Value from False to true and click OK:
NOTE: Before testing the rule by adding a user to Domain Admins, ensure that the series of 1200, 1201 and 1210 events is observed in the operations manager event log on the Windows Domain Controller that you are monitoring.
NOTE: If you have followed these steps of creating the rule and then creating the override, you should see two series of 1200, 1201, 1210 events, one series for when a new version of the management pack containing the new rule (disabled by default) is received, and a second series for when it receives a newer version of the management pack containing the override that enables it.
Note: the 1204s will appear if there was an existing previous version of the MP, that gets flushed prior to the import of this current version.
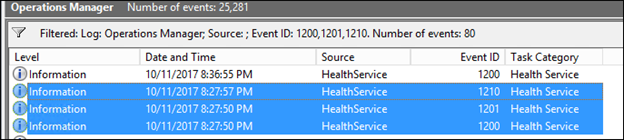
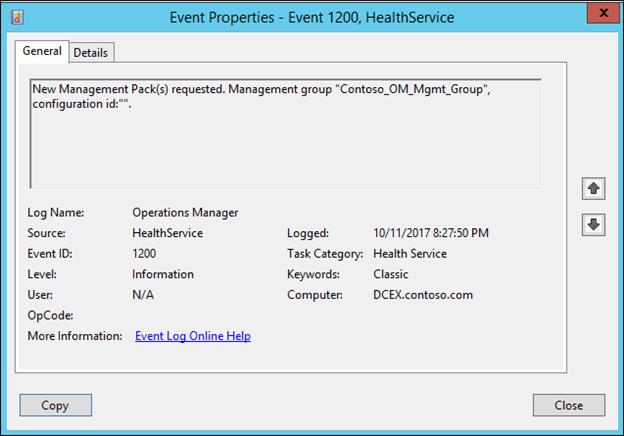
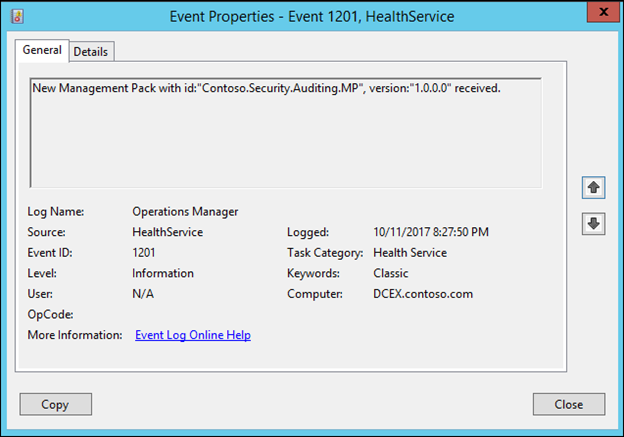
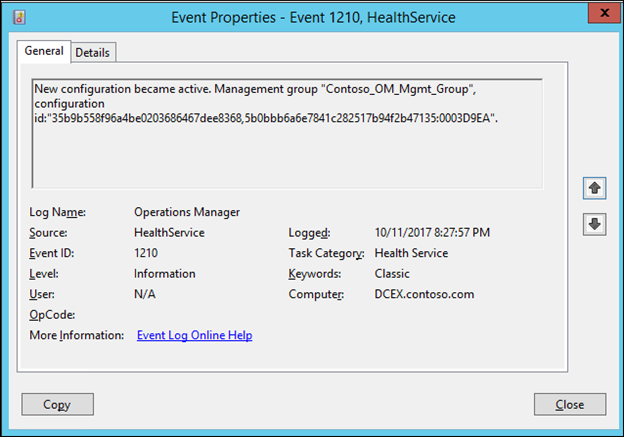
Now, test the rule by adding a user to domain admins on the DC, and you should see a new alert appear in the Monitoring>Active Alerts view of the Operator's console:
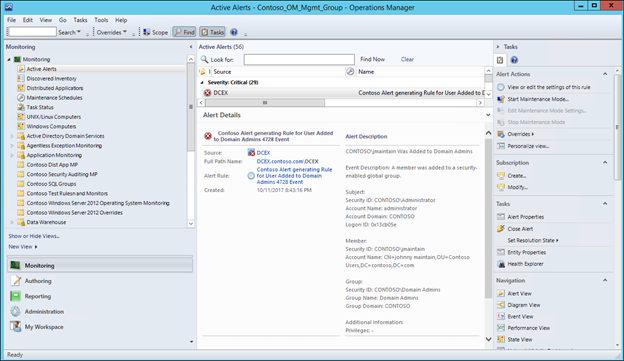
NOTE: Unless any matching subscriptions have been previously created that match the new alert, a notification email will not be sent out. In order to be notified by email when this happens, use the following steps in the section: https://aka.ms/scom101subscription
NOTE: Any comments and feedback greatly appreciated if you found this post helpful or have any corrections / suggestions. Cheers, Antoni