Operations Manager 101: Create an Event Collection Rule for Monitoring Server Restarts
Note this is part of a System Center 2016 – Operations Manager and Operations Management Suite (OMS) 101 Series: https://aka.ms/101
In this scenario we will create an event collection rule for Monitoring Server Restarts. Depending on how frequently this happens in your environment, it is possible you do not want an alert generated every time this happens, hence it may be more appropriate just to have an event collection rule, so these events can be viewed in an event view.
NOTE: An Event Collection Rule will only store the events in the Operations Manger database, making them accessible via event views. It will not generate an alert when an event occurs – for the purpose of generating an alert (from which email notification can be configured) use an Alert-generating rule.
Go to the Authoring space
1) Launch the Operations Console
2) Click the 'Authoring' space on the bottom left hand side.
3) Right-click Management Pack Objects>Rules and choose 'Create a new rule'
4) In the dialog, expand Collection Rules>Event based
5) Click 'NT Event Log'
NOTE: A Golden rule of Operations Manager is to NOT store anything in the Default Management Pack. See this post for more additional guidance on Management Packs best practice: https://blogs.technet.microsoft.com/antoni/2013/10/09/system-center-service-manager-operations-manager-management-pack-and-naming-convention-best-practices/
6) Change the Management Pack to an appropriate Management Pack. For example, a management pack containing custom rules and monitors, then select it from the dropdown. If necessary, create a new Management Pack by clicking the New button, give it a name, hit Next and Create)
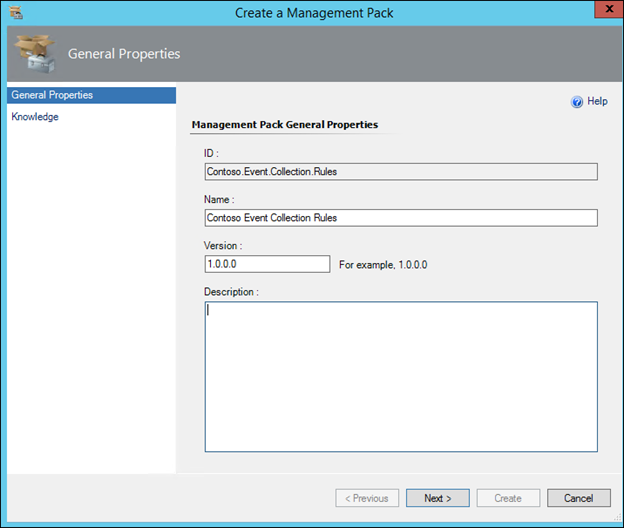
7) With NT Event Log and the appropriate Management Pack selected, click Next:
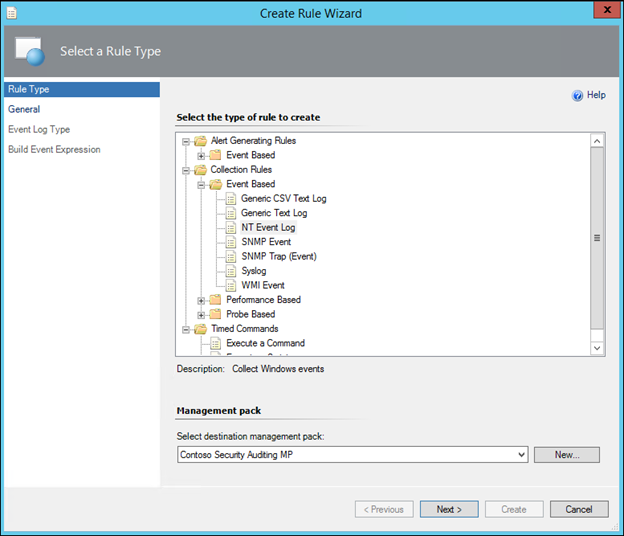
8) Give the rule a name (For Example: 'Contoso Event Collection Rule for 6005 Events in System Log - Agent Restarts')
NOTE: It is best practice to use some form of prefix or three-letter acronym as a naming convention, to identify all of an organization's custom rules and monitors (I am using Contoso as my prefix in all these examples). This makes it much easier to find custom rules in the console when necessary.
9) Click the 'Select' button next to the Rule target box and choose an appropriate target such as 'Windows Computer', uncheck the 'Rule is Enabled' and click OK.
NOTE: Start typing the name of the object desired in the 'Look For' box to narrow the list down, and If the object desired is not displayed, click the 'View all targets' radio button.
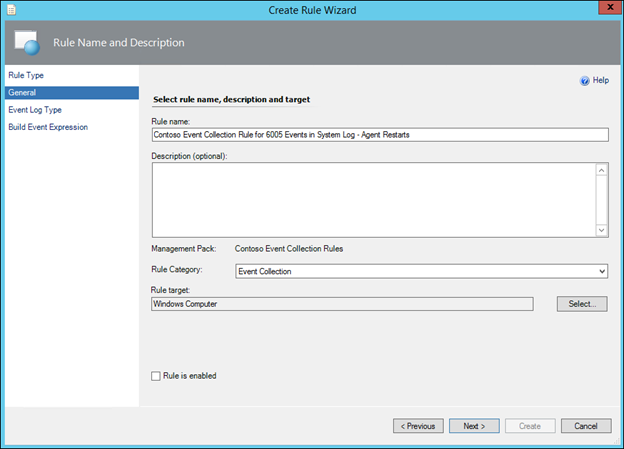
11) In the Event Log Name, type the word System, or alternatively click the 3 dots and select the System Event Log, and click Next:
NOTE: This is nothing to do with the targeting. This is purely to make sure you get the name of the event log correct with no typos. The Rule will look in the selected event log on every object targeted (e.g. every windows computer or domain controller) that has the selected event log.
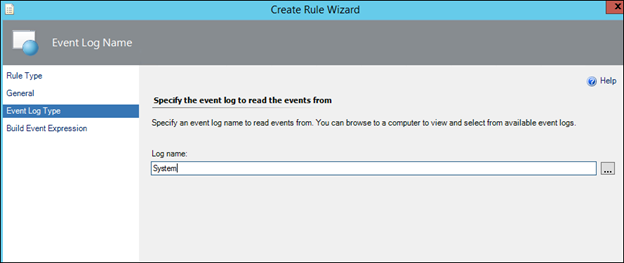
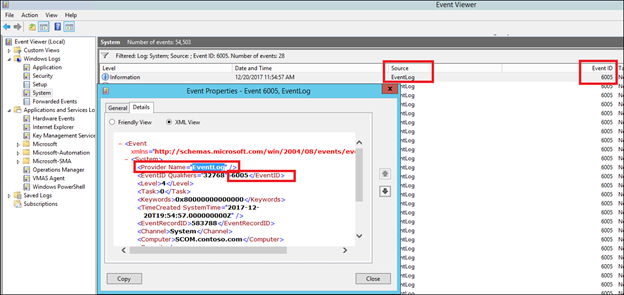
12) In the Value box on the Event ID line, type 6005 and in Event Source type EventLog:
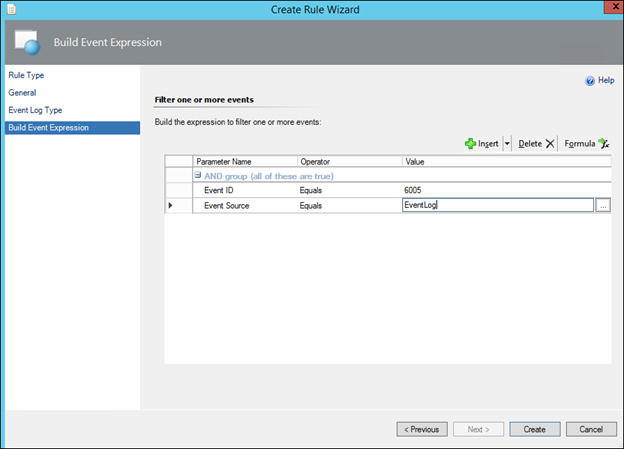
NOTE: If you wish to collect a different Event, simply specify the alternative Event ID here.
NOTE. In the case of the 6005 event, the Event Source is EventLog
14) Click Create.
15) Find the Event Collection Rule using the Look For box:
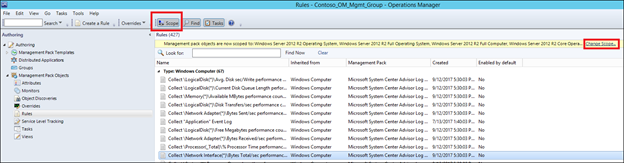
16) In Authoring>Rules, if the yellow bar is shown click the 'Change Scope' hyperlink. If the yellow bar is not shown, click the Scope button in the taskbar :
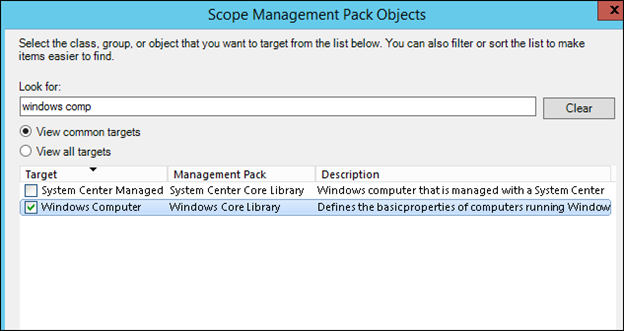
17) Choose Windows Computer and click ok:
18) Use the 'Look for' box to find the rule that you just created:
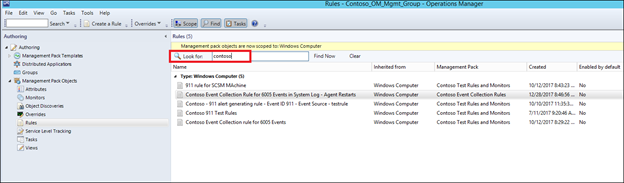
19) Override the Rule for all objects of class, for a group, for a specific object depending on your scenario (which of these you wish to turn the event collection rule on for):
:
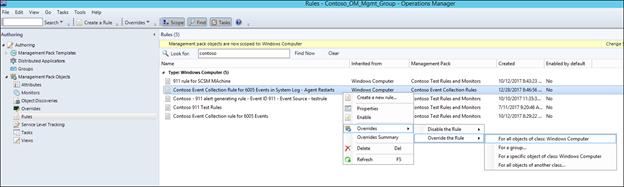
20) Place a check mark next to 'Enabled' and then change the override value from False to True, and then click OK to save the override:
Task 2 (Optional) – Create an Event View in Operations Manager for viewing the collected Events.
NOTE: If you create the view under 'my workspace;' this is associated with your user profile and the view will only be visible to you. If you create it under a folder in the main Monitoring folder structure, then it will be available to others (depending on configured security / user roles etc)
1) In the Operator's console, right click either the desired folder in the main monitoring structure, or the top level in My workspace,
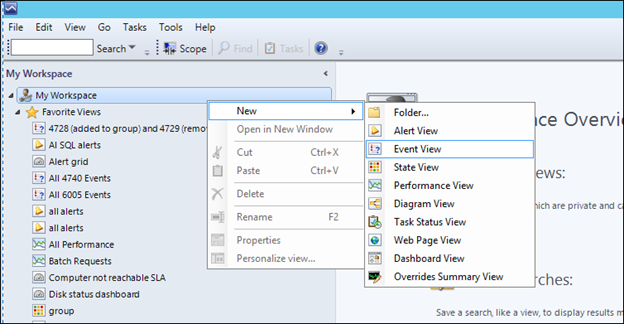
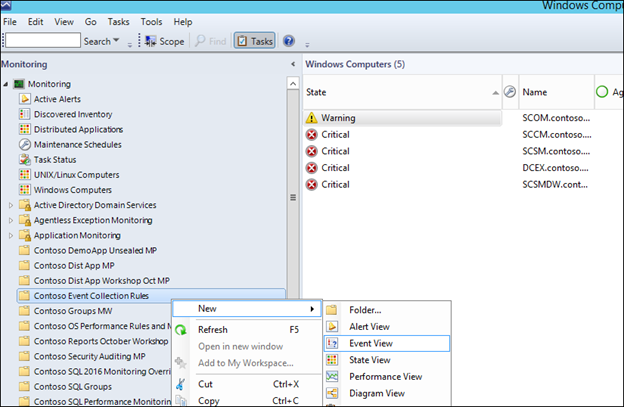
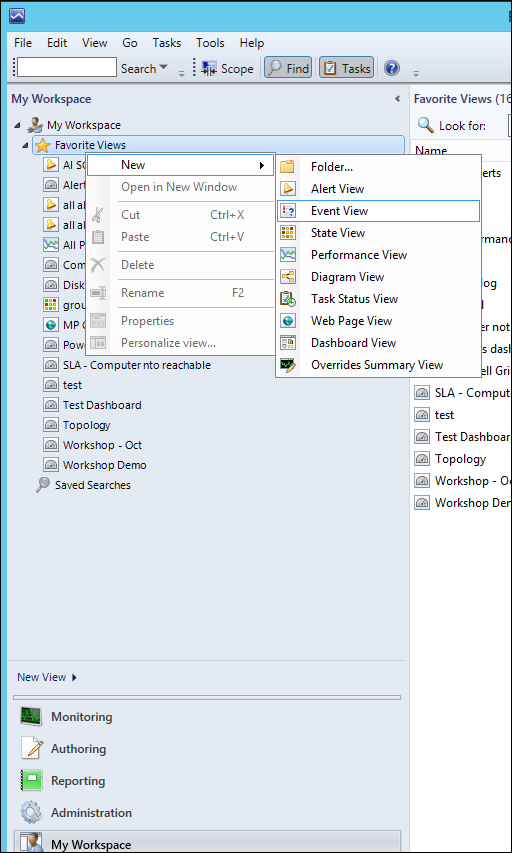
3) Give the view a name. In our case, a name like 'Agent Restarts - 6005 events' is relevant.
4) Place a check in the 'with a specific event number' criteria
5) Click the 'specific' hyperlink that appears in the criteria description box.
6) Type the event ID that you want to display (in our case 632) and click OK:
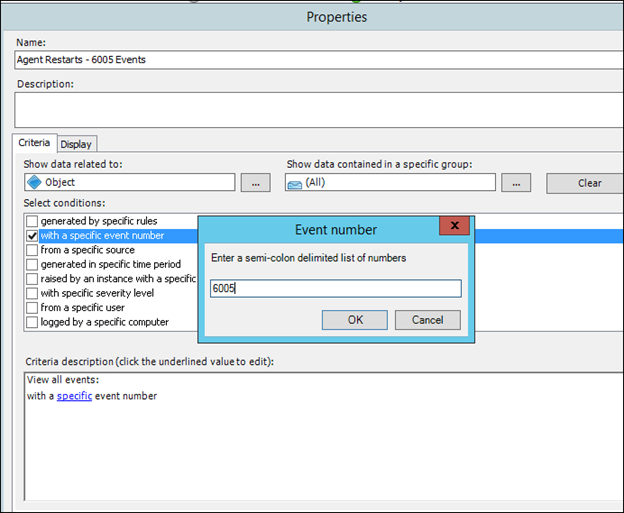
7) Click OK in the Properties dialog
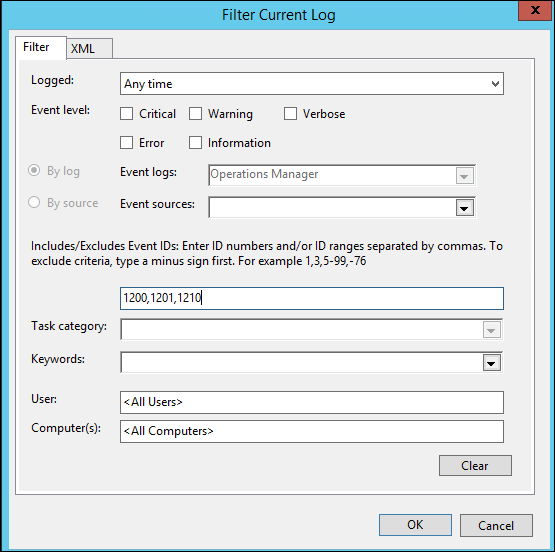
8) Verify that the new rule makes it down to the computer on which you intend the event to be collected from by looking for a series of 1200, 1201 and 1210 events In the Operations Manager event log (The 1201 event should show the name of the management pack that you created the rule in):

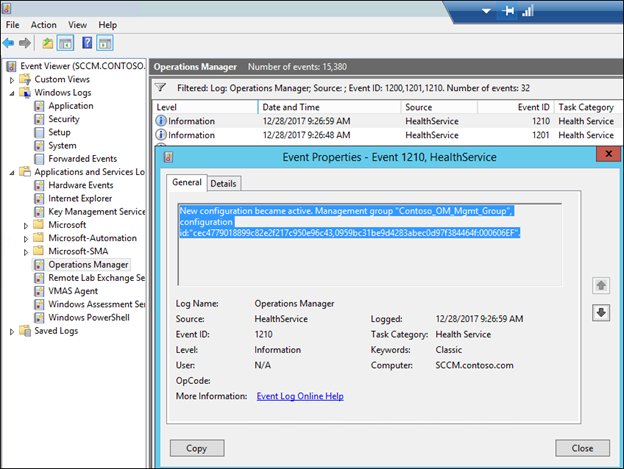
9) Repro the scenario so that an event is generated on the computer and collected in operations Manager. In this example I rebooted SCCM
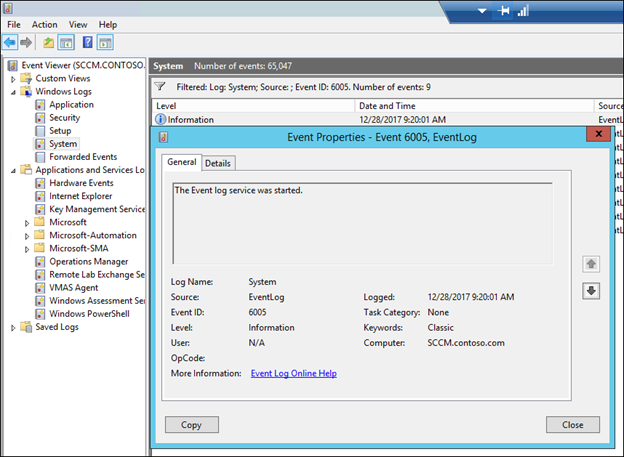
Note, if you wanted to create an email alert, you would need to re-create this as an alert generating rule as described at https://aka.ms/scom101subscription
NOTE: Any comments and feedback greatly appreciated if you found this post helpful or have any corrections / suggestions. Cheers, Antoni