3.4.7.3 Transition to Main Mode Initiator First Exchange Done
When the main mode initiator enters Main Mode Initiator First Exchange Done state, it MUST proceed to Quick Mode Initiator First Packet Sent state after sending a packet formatted as specified in the following diagram.
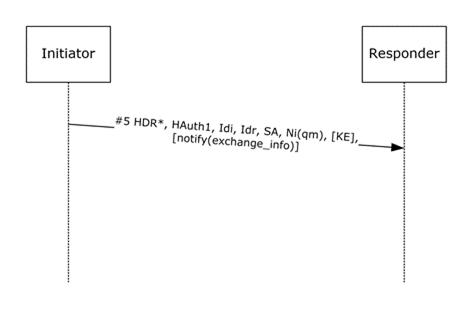
Figure 13: Quick Mode First Exchange packet
The Authenticated Internet Protocol supports two types of quick mode exchanges:
Normal (two exchanges)
Fast (one exchange)
The initiator can use fast quick mode if its SPD lookup returns a single quick mode proposal and if quick mode perfect forward secrecy is not required by the SPD. Fast quick mode is optional and implementation-specific.
The first quick mode exchange (normal or fast) MUST be performed within the MM exchange, that is, using the MM exchange type instead of the quick mode exchange type.
The message MUST be constructed as follows:
HDR: The ISAKMP header MUST be identical to the first IKE phase 2 initiator packet, as specified in [RFC2409] section 5.5, with this exception: the exchange type MUST be 243 (MM exchange type) for the first quick mode exchange under this main mode or 244 (quick mode exchange type) for any subsequent quick mode exchange. The Encrypted flag MUST be set.
The following payloads MUST be encapsulated in an encrypted Crypto payload. The Crypto payload MUST be constructed in the following way:
The seqNUM field MUST be set to the current value of the main mode security association database (MMSAD) sequence number for the current exchange type, as specified in section 3.1.4.
The Initialization_Vector and Encrypted payload fields MUST be computed as specified in [RFC4303] section 2.3.
The Padding field MUST be computed as specified in [RFC4303] section 2.4.
The Integrity Checksum Data field MUST be computed as specified in [RFC4303] section 2.8, and MUST cover the ISAKMP header to the beginning of the Integrity Checksum Data. It MUST be computed using the HMAC of the hash algorithm that is negotiated in main mode. The default mechanism specified in [RFC4303] MUST be used to generate the pad contents.
H: The ISAKMP Hash payload that contains Auth1. Auth1 MUST be computed as defined in section 3.1.7.4.
IDi, IDr, SA, Ni(qm), KE: These payloads MUST be identical to the corresponding IKE payloads, as specified in [RFC2408] sections 3.8, 3.4 and 3.13. The SA, IDi, and IDr payloads MUST be constructed by looking up the PAD Entry IDs (see [RFC4301] section 4.4.3.1). The key exchange (KE) payload MUST be sent if quick mode perfect forward secrecy is required according to the policy stored in the SPD.
Notify(exchange_info): The EXCHANGE_INFO Notify payload MUST be included if the SPD indicates either that guaranteed encryption is active, or the sender uses negotiation discovery (based on SPD lookup). A precondition for sending this notify is that the MM SA MUST have the PeerIsNegotiationDiscoveryCapable bit set in the MMSAD (see section 3.2.5.1). These two policy options MUST be implemented as specified in [MS-IKEE] section 3.7.4.
SkWt: If the node indicates that it will dictate keys (that is, LocalEndWantsToDictateKey is set), then it can optionally construct the Key Dictation Weight payload using the per QM SA state KeyDictationWtLocal field to negotiate Key Dictation with the peer.