Azure confidential ledger で証明書ベースのユーザーを管理する
証明書ベースのユーザーの場合、ユーザー ID は PEM 証明書のフィンガープリントです。 管理者特権を持つユーザーは、confidential ledger のユーザーを管理できます。 使用可能なロールは、閲覧者 (読み取り専用)、共同作成者 (読み取りと書き込み)、管理者 (読み取り、書き込み、および管理ユーザー) です。
ユーザーを管理するには、次のクライアント ライブラリを使うことができます:
Azure へのサインイン
Azure CLI az login コマンドまたは Azure PowerShell Connect-AzAccount コマンドレットを使用して Azure にサインインします。
az login
CLI または PowerShell で既定のブラウザーを開くことができる場合、ブラウザが開き、Azure サインイン ページが読み込まれます。 そうでない場合は、https://aka.ms/devicelogin を開き、ターミナルに表示されている認証コードを入力します。
メッセージが表示されたら、ブラウザーでアカウントの資格情報を使用してサインインします。
Azure portal から confidential ledger の名前と ID サービス URI を取得します。これには、ユーザーを管理するためのクライアントの作成が必要になります。 この図は、Azure portal の適切なプロパティを示しています。
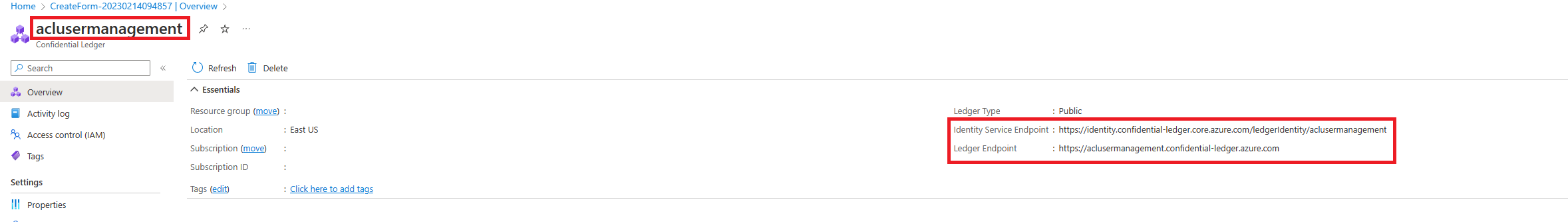
次のコード スニペットの contoso と https://contoso.confidential-ledger.azure.com のインスタンスを、Azure portal のそれぞれの値に置き換えます。
Python クライアント ライブラリ
パッケージのインストール
pip install azure-identity azure-confidentialledger
Confidential ledger クライアントを作成してユーザーを管理する
from azure.identity import DefaultAzureCredential
from azure.confidentialledger import ConfidentialLedgerClient
from azure.confidentialledger.identity_service import ConfidentialLedgerIdentityServiceClient
from azure.confidentialledger import LedgerUserRole
identity_client = ConfidentialLedgerCertificateClient()
network_identity = identity_client.get_ledger_identity(
ledger_id="contoso"
)
ledger_tls_cert_file_name = "ledger_certificate.pem"
with open(ledger_tls_cert_file_name, "w") as cert_file:
cert_file.write(network_identity["ledgerTlsCertificate"])
credential = DefaultAzureCredential()
ledger_client = ConfidentialLedgerClient(
endpoint="https://contoso.confidential-ledger.azure.com",
credential=credential,
ledger_certificate_path=ledger_tls_cert_file_name
)
# Add a user with the contributor role
# Other possible roles are Contributor and Administrator
user_id = "PEM certficate fingerprint"
user = ledger_client.create_or_update_user(
user_id, {"assignedRole": "Contributor"}
)
# Get the user and check their properties
user = ledger_client.get_user(user_id)
assert user["userId"] == user_id
assert user["assignedRole"] == "Contributor"
# Delete the user
ledger_client.delete_user(user_id)
.NET クライアント ライブラリ
パッケージのインストール
dotnet add package Azure.Security.ConfidentialLedger
dotnet add package Azure.Identity
dotnet add Azure.Security
クライアントを作成してユーザーを管理する
using Azure.Core;
using Azure.Identity;
using Azure.Security.ConfidentialLedger;
internal class ACLUserManagement
{
static void Main(string[] args)
{
// The DefaultAzureCredential will use the current Azure context to authenticate to Azure
var ledgerClient = new ConfidentialLedgerClient(new Uri("https://contoso.confidential-ledger.azure.com"), new DefaultAzureCredential());
// User id is the fingerprint of the PEM certificate
string userId = "PEM certficate fingerprint";
// Add the user with the Reader role
// Other supported roles are Contributor and Administrator
ledgerClient.CreateOrUpdateUser(
userId,
RequestContent.Create(new { assignedRole = "Reader" }));
// Get the user and print their properties
Azure.Response response = ledgerClient.GetUser(userId);
var aclUser = System.Text.Json.JsonDocument.Parse(response.Content.ToString());
Console.WriteLine($"Assigned Role is = {aclUser.RootElement.GetProperty("assignedRole").ToString()}");
Console.WriteLine($"User id is = {aclUser.RootElement.GetProperty("userId").ToString()}");
// Delete the user
ledgerClient.DeleteUser(userId);
}
}
Java クライアント ライブラリ
パッケージのインストール
<!-- https://mvnrepository.com/artifact/com.azure/azure-security-confidentialledger -->
<dependency>
<groupId>com.azure</groupId>
<artifactId>azure-security-confidentialledger</artifactId>
<version>1.0.6</version>
</dependency>
<!-- https://mvnrepository.com/artifact/com.azure/azure-identity -->
<dependency>
<groupId>com.azure</groupId>
<artifactId>azure-identity</artifactId>
<version>1.8.0</version>
</dependency>
<!-- https://mvnrepository.com/artifact/com.azure/azure-core -->
<dependency>
<groupId>com.azure</groupId>
<artifactId>azure-core</artifactId>
<version>1.36.0</version>
</dependency>
クライアントを作成してユーザーを管理する
import java.io.IOException;
import com.azure.core.http.HttpClient;
import java.io.ByteArrayInputStream;
import java.nio.charset.StandardCharsets;
import com.azure.security.confidentialledger.*;
import com.azure.core.http.rest.RequestOptions;
import com.azure.core.http.netty.NettyAsyncHttpClientBuilder;
import com.azure.core.http.rest.Response;
import com.azure.core.util.BinaryData;
import com.azure.identity.DefaultAzureCredentialBuilder;
import com.fasterxml.jackson.databind.JsonNode;
import com.fasterxml.jackson.databind.ObjectMapper;
import com.azure.security.confidentialledger.certificate.ConfidentialLedgerCertificateClient;
import com.azure.security.confidentialledger.certificate.ConfidentialLedgerCertificateClientBuilder;
import io.netty.handler.ssl.SslContext;
import io.netty.handler.ssl.SslContextBuilder;
public class CreateOrUpdateUserSample {
public static void main(String[] args) {
try {
// Download the service identity certificate of the ledger from the well-known identity service endpoint.
// Do not change the identity endpoint.
ConfidentialLedgerCertificateClientBuilder confidentialLedgerCertificateClientbuilder = new ConfidentialLedgerCertificateClientBuilder()
.certificateEndpoint("https://identity.confidential-ledger.core.azure.com")
.credential(new DefaultAzureCredentialBuilder().build()).httpClient(HttpClient.createDefault());
ConfidentialLedgerCertificateClient confidentialLedgerCertificateClient = confidentialLedgerCertificateClientbuilder
.buildClient();
String ledgerId = "contoso";
Response<BinaryData> ledgerCertificateWithResponse = confidentialLedgerCertificateClient
.getLedgerIdentityWithResponse(ledgerId, null);
BinaryData certificateResponse = ledgerCertificateWithResponse.getValue();
ObjectMapper mapper = new ObjectMapper();
JsonNode jsonNode = mapper.readTree(certificateResponse.toBytes());
String ledgerTlsCertificate = jsonNode.get("ledgerTlsCertificate").asText();
SslContext sslContext = SslContextBuilder.forClient()
.trustManager(new ByteArrayInputStream(ledgerTlsCertificate.getBytes(StandardCharsets.UTF_8)))
.build();
reactor.netty.http.client.HttpClient reactorClient = reactor.netty.http.client.HttpClient.create()
.secure(sslContextSpec -> sslContextSpec.sslContext(sslContext));
HttpClient httpClient = new NettyAsyncHttpClientBuilder(reactorClient).wiretap(true).build();
// The DefaultAzureCredentialBuilder will use the current Azure context to authenticate to Azure.
ConfidentialLedgerClient confidentialLedgerClient = new ConfidentialLedgerClientBuilder()
.credential(new DefaultAzureCredentialBuilder().build()).httpClient(httpClient)
.ledgerEndpoint("https://contoso.confidential-ledger.azure.com").buildClient();
// Add a user using their certificate fingerprint as the user id
// Other supported roles are Contributor and Administrator
BinaryData userDetails = BinaryData.fromString("{\"assignedRole\":\"Reader\"}");
RequestOptions requestOptions = new RequestOptions();
String userId = "PEM certificate fingerprint";
Response<BinaryData> response = confidentialLedgerClient.createOrUpdateUserWithResponse(userId,
userDetails, requestOptions);
BinaryData parsedResponse = response.getValue();
ObjectMapper objectMapper = new ObjectMapper();
JsonNode responseBodyJson = null;
try {
responseBodyJson = objectMapper.readTree(parsedResponse.toBytes());
} catch (IOException e) {
e.printStackTrace();
}
System.out.println("Assigned role for user is " + responseBodyJson.get("assignedRole"));
// Get the user and print the details
response = confidentialLedgerClient.getUserWithResponse(userId, requestOptions);
parsedResponse = response.getValue();
try {
responseBodyJson = objectMapper.readTree(parsedResponse.toBytes());
} catch (IOException e) {
e.printStackTrace();
}
System.out.println("Assigned role for user is " + responseBodyJson.get("assignedRole"));
// Delete the user
confidentialLedgerClient.deleteUserWithResponse(userId, requestOptions);
} catch (Exception ex) {
System.out.println("Caught exception" + ex);
}
}
}
TypeScript クライアント ライブラリ
パッケージのインストール
"dependencies": {
"@azure-rest/confidential-ledger": "^1.0.0",
"@azure/identity": "^3.1.3",
"typescript": "^4.9.5"
}
クライアントを作成してユーザーを管理する
import ConfidentialLedger, { getLedgerIdentity } from "@azure-rest/confidential-ledger";
import { DefaultAzureCredential } from "@azure/identity";
export async function main() {
// Get the signing certificate from the confidential ledger Identity Service
const ledgerIdentity = await getLedgerIdentity("contoso");
// Create the confidential ledger Client
const confidentialLedger = ConfidentialLedger(
"https://contoso.confidential-ledger.azure.com",
ledgerIdentity.ledgerIdentityCertificate,
new DefaultAzureCredential()
);
// User id is the PEM certificate fingerprint
const userId = "PEM certificate fingerprint"
// Other supported roles are Reader and Contributor
const createUserParams: CreateOrUpdateUserParameters = {
contentType: "application/merge-patch+json",
body: {
assignedRole: "Contributor",
userId: `${userId}`
}
}
// Add the user
var response = await confidentialLedger.path("/app/users/{userId}", userId).patch(createUserParams)
// Check for a non-success response
if (response.status !== "200") {
throw response.body.error;
}
// Print the response
console.log(response.body);
// Get the user
response = await confidentialLedger.path("/app/users/{userId}", userId).get()
// Check for a non-success response
if (response.status !== "200") {
throw response.body.error;
}
// Print the response
console.log(response.body);
// Set the user role to Reader
const updateUserParams: CreateOrUpdateUserParameters = {
contentType: "application/merge-patch+json",
body: {
assignedRole: "Reader",
userId: `${userId}`
}
}
// Update the user
response = await confidentialLedger.path("/app/users/{userId}", userId).patch(updateUserParams)
// Check for a non-success response
if (response.status !== "200") {
throw response.body.error;
}
// Print the response
console.log(response.body);
// Delete the user
await confidentialLedger.path("/app/users/{userId}", userId).delete()
// Get the user to make sure it is deleted
response = await confidentialLedger.path("/app/users/{userId}", userId).get()
// Check for a non-success response
if (response.status !== "200") {
throw response.body.error;
}
}
main().catch((err) => {
console.error(err);
});