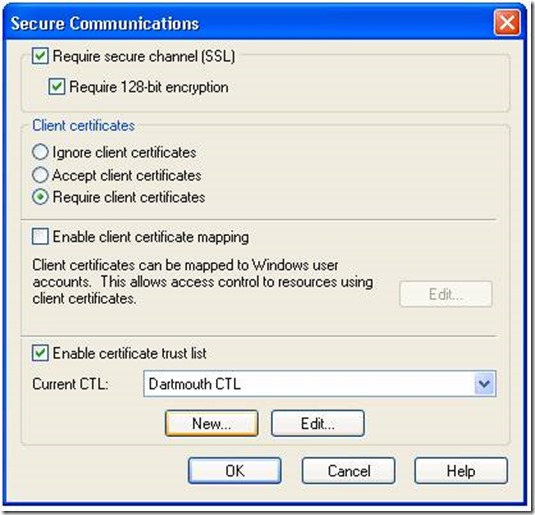
How to create custom Certificate Trust List in Windows Server 2K8 R2
In windows server 2003 server we can create our own custom certificate trust list using the UI in IIS to bind the CTL to the SSL certificate.
To check how we can add the custom CTL in IIS6 please follow the following link
However, the same UI is not provided in IIS7.5. To add the custom CTL in IIS7.5 we need to perform following steps
Create Custom CTL
We need to create a custom CTL. We can do it using MakeCTL.exe. However, MakeCTL.exe doesn’t work in Windows Server 2008 R2. So, we need a Windows Server 2003 or Windows Server 2008 (non R2) server to do it.
Step 1: Install MakeCTL.exe.
To install MakeCTL.exe you need to install Windows server 2003 SDK (https://www.microsoft.com/en-us/download/details.aspx?id=15656) or .net framework 1.1 SDK.
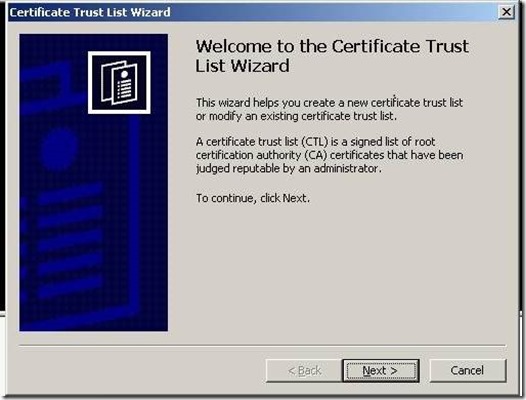
Step 2: Run MakeCTL.exe as an administrator
Step 3: Click Next on the “Welcome to the Certificate Trust List Wizard”
Step 4: In Certificate Trust List Purpose screen, provide a Prefix for this CTL. This will work as the friendly name for the CTL. Provide a simpler name for this as whenever you want to attach the CTL to the certificate you need to provide this name. I have given the name as CTLTest.
Step 5: Click on the Add purpose.
Step 6: In the User Defined Purpose box, add the following in the Object ID field and click OK: 1.3.6.1.4.1.311.10.1. Make sure you don’t add any space before or after this value.
Why we need to provide 1.3.6.1.4.1.311.10.1.
As per the article https://support.microsoft.com/kb/287547 1.3.6.1.4.1.311.10.1 object Id belongs to Certificate Trust List (CTL).
Step 7: Check whether 1.3.6.1.4.1.311.10.1 has been added to the list of purposes and has a checkmark on it. If yes, click next.
Step 8: Select the “Add from Store” button on the Certificates in the CTL window.
Step 9: In the Select Certificate window, select the certificate of the Trusted Root CAs that you need to configure your CTL for.
Step 10: In the Certificate Trust List Storage window, select File and click the Browse button.
Step 11: Save the File as .stl format.
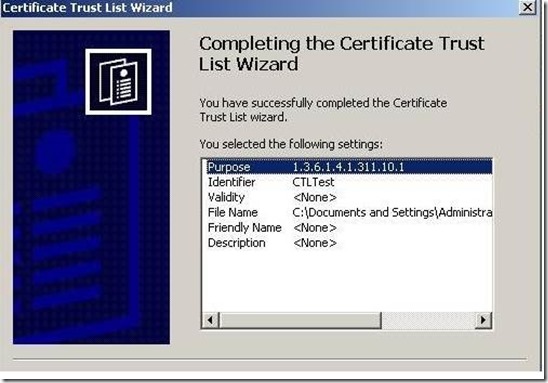
Step 12: Click the Next button and see the CTL information in the window to verify
Step 13. Click on Finish and it will show a message as “The Certificate Trust List wizard was succeeded”.
Step 14: Copy this STL file manually to the Windows Server 2008 R2 server.
Import the CTL in certificate mmc
Step 1: Click on Intermediate Certification Authorities and Click on Import
Step 2: Click on Next in the Certificate Import Wizard.
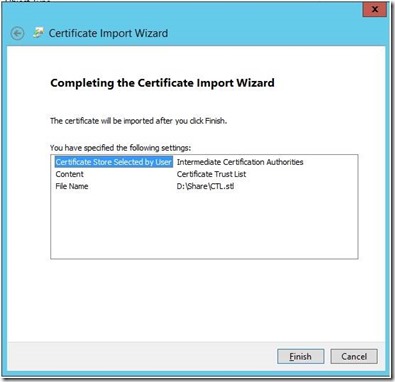
Step 3: Click on Browse and select the stl file.
Step 4: Keep “Place all certificates in the following store” as “Intermediate Certificate authorities”. Click on Next.
Step 5: Check the information before the finish. If everything is correct click on finish.
Step 6: You will get the message as “The import was successful”.
Add CTL to the certificate
Step 1: Launch a command prompt in Administrator mode.
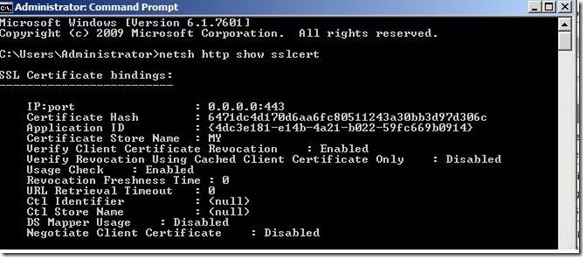
Step 2: Type the command as netsh http show sslcert.
This will show all the ssl bindings you have on your server. You should recognize which IP and Port combination you need to use. For example I am using IP:Port as 0.0.0.0:443.
IP:port : 0.0.0.0:443
Certificate Hash : 6471dc4d170d6aa6fc80511243a30bb3d97d306c
Application ID : {4dc3e181-e14b-4a21-b022-59fc669b0914}
Certificate Store Name: MY
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time: 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Please note down the Certhash value and the appId. We need to use them later.
Note: CTL Identifier and CTL Store Name are both null. We need to change it to begin using the CTL.
But to change it we have to delete this binding and add it again with the specified information.
Step 3: Type the command as netsh http delete sslcert ipport=0.0.0.0:443. You will receive the command as “SSL Certificate successfully deleted”
Step 4: Now add the certificate with the CTL information. Type the command as
netsh http add sslcert ipport=0.0.0.0:443 certhash=15e3063e10e3d50127d323d8b6827ddd7ae33936 appid={4dc3e181-e14b-4a21-b022-59fc669b0914} sslctlidentifier=TestCTLs sslctlstorename=CA
Note: You need to change the Ip:Port ,Certhash,appId and sslCtlidentifier as per your settings. Refer the values you note down in Step 2. Your sslctlidentifier value is going to be the friendly name of your CTL. Remember, that the friendly name must be spelled perfectly and with case sensitivity. Sslctlstorename simply needs to be CA.
If you get the message as
“SSL Certificate add failed, Error: 1312 A specified logon session does not exist. It may already have been terminated”
First thing you need to check if you are putting the correct name in the sslctlidentifier.
If everything is right then you may need to install following hotfix (If you don’t have Windows Server 2008 R2 SP1).
https://support.microsoft.com/default.aspx?scid=kb;EN-US;981506
After installing the hotfix the certificate will be added.
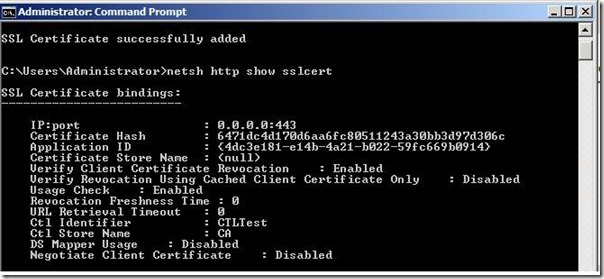
Step 5: You can now check certificate again using the command netsh http show sslcert. It will be shown as below.
IP:port : 0.0.0.0:443
Certificate Hash : 6471dc4d170d6aa6fc80511243a30bb3d97d306c
Application ID : {4dc3e181-e14b-4a21-b022-59fc669b0914}
Certificate Store Name : (null)
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time: 0
URL Retrieval Timeout : 0
Ctl Identifier : CTLTest
Ctl Store Name : CA
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
CTL is not honored in initial SSL handshake
One would assume that Certificate Trust List (CTL) will limit the list of Trusted Certificate Authorities (CA's) being sent to the client during the initial SSL handshake. However, IIS 6.0/7.0 using CTL's you cannot limit the list of CA's sent back to the client during the SSL/TLS handshake. That means you can't use CTL's to limit the list of certificates that Internet Explorer is showing. IE will show all the certificates irrespective of whether the issuing CA is a part of the CTL or not. For more information follow the following link
Though if you select a certificate whose CA is not a part of the CTL then you will get the error as 403.16: Client Certificate is untrusted or invalid.
Hope this blog helps you.
Comments
Anonymous
July 08, 2013
Currently at the point where I need to designate a CA for UAG endpoint authentication certificates. MS Technet article still points to IIS 6.0 Instructions. I found a few sites with bits and pieces, but this blog post seems to put it all together. I will give this a shot tomorrow and post results. Thanks in advance.Anonymous
July 11, 2013
The comment has been removedAnonymous
July 15, 2013
Thanks for notifying DesertIT. I will correct itAnonymous
March 16, 2015
Is there some way to make a self-signed client certificate using the makecert.exe tool to validate that the CTL is actually functioning correctly? I attempted to generate a certificate but when accessing the page, the certificate I generated was not shown as a connecting option even after installing it in my user "private" store and verifying it was listed in IE as a certificate. I initially believed the certificate was not displaying due to not matching a CA in the CTL but your last section would suggest the opposite behavior (cert is listed but then 403.16 displayed when selected). I looked at separate webserver which did not have a CTL and the certificate appeared as an option when connecting to that server. Both servers are IIS 7.5.Anonymous
February 18, 2016
As both Server 2003 and 2008 are past EOL, is there any chance of getting updated directions?



![clip_image009[1] clip_image009[1]](https://msdntnarchive.z22.web.core.windows.net/media/MSDNBlogsFS/prod.evol.blogs.msdn.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/01/59/14/metablogapi/8446.clip_image0091_thumb_6970C9CB.jpg)