Upgrade Readiness now helps assess Spectre and Meltdown protections
Update: This post was updated on February 26, 2018 to include a section on "How to use these new blades".
It’s important to protect your computers against the hardware security vulnerabilities known as Spectre and Meltdown. Microsoft has published guidance for IT Pros that outlines the steps Microsoft has taken as well as steps you can take to take advantage of all available protections.
As outlined in the guidance for IT Pros article, Microsoft recommends three steps to help protect against the Spectre and Meltdown vulnerabilities:
- Verify that you are running a supported antivirus application.
- Apply all available Windows operating system updates, including the January 2018 and later Windows security updates.
- Apply any applicable processor firmware (microcode) updates provided by your device manufacturer(s).
To help you keep track of all this, we’re rolling out an update to Upgrade Readiness that provides insight into the status of your devices across these three axes. Note that you may see a large number of blank, “unknown”, or “to be determined” statuses at first. Rest assured, we will be working on enhancing the data that you see in Upgrade Readiness as new information becomes available.
One action that you can take immediately is to ensure that your computers are able to reach the following endpoint:
https://adl.windows.com
This may involve adding this URL to your company’s whitelist which may require approval from your security group. This endpoint is used to communicate updates to Microsoft’s compatibility information with client computers. By ensuring your computers can reach this endpoint, you can help them get the most up-to-date information Microsoft has available about supported antivirus solutions and versions, security update statuses, etc.
How to use these new blades
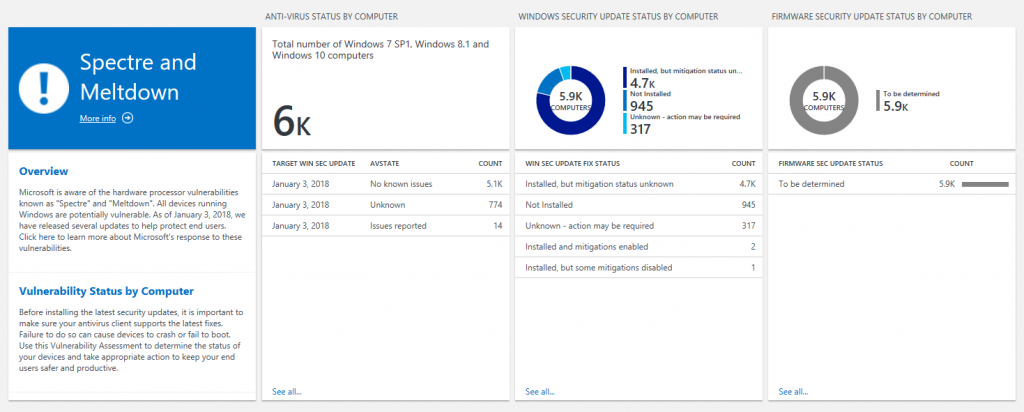
The first new blade, called "Anti-virus status by computer," is designed to help you determine if your devices' anti-virus solution is compatible with the latest Windows OS updates from Microsoft. You're able to see how many of your devices have an anti-virus solution with no known issues, issues reported, or an unknown status for a particular Windows security update. For example, in the image below, we can see that an anti-virus solution that has no known issues with the January 3, 2018 Windows OS update is installed on about 2,800 devices. We include the target Windows OS update in the blade because the same anti-virus solution may have different compatibility statuses across different security updates.
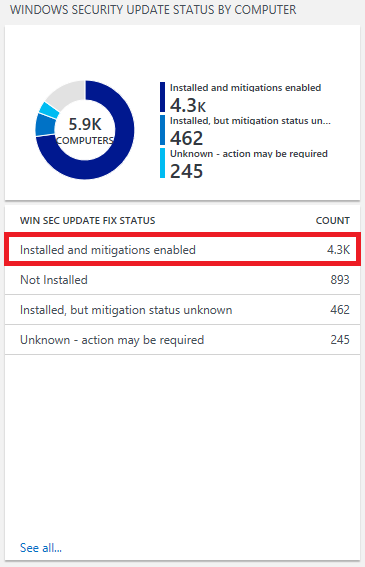
The second blade, called "Windows security update status by computer," indicates whether a Windows OS security update that includes Spectre/Meltdown related fixes (January 3, 2018 or later) has been installed, as well as whether specific fixes have been disabled. While protections are enabled by default on Windows clients, some IT admins may choose to disable specific protections. You can learn more about this on Microsoft's guidance for IT pros page. (Note that separate guidance applies to Windows Servers.) In the example below, we can see that about 4,300 devices have a Windows security update that includes Spectre/Meltdown protections installed, and those protections are enabled.
Important! If you are seeing computers with statuses of either “Unknown – action may be required” or “Installed, but mitigation status unknown,” it is likely that you need to whitelist the above endpoint.
The third blade -- "Firmware security update status by computer" -- will show how many of your devices have installed a firmware update that includes Spectre/Meltdown protections. As of the time this blog post was published, firmware status data is not yet available. Our goal is to provide this information once it becomes available from our CPU partners. No action will be required to start seeing this information once it is available.
We’ll be updating this blog post over the next several weeks as we continue to enhance this feature. In the meantime, please let us know if you have any questions or feedback. You can always reach us at uasupport@microsoft.com.
Comments
- Anonymous
February 13, 2018
Please add, that Upgrade Readiness is part of OMS, first i tried to find it in SCCM :) - Anonymous
February 19, 2018
Awesome Advice, Zach Dvorak of Microsoft. This blog piece is fantastic!!! This really helps me as a Windows Insider who tested Windows Vista for cyber-security issues as well as Windows 10 for general issues. BTW, our organization has a mix of Windows 7 Enterprise Computers as well as Windows 10 1703 Computers that are currently takening advantage of EMET which is set to expire on July 31, 2018. Can you give me further details for upgrading in June or July are Network bank of Windows 10 computers. We plan on keeping the Windows 7 Professional 64 bit machines until the end of Windows 7 Enterprise Service in January 2020.- Anonymous
April 09, 2018
Hey Dan,I'm not very familiar with EMET, but I would recommend looking into Windows Defender ATP as a possible replacement.Thanks,Zach
- Anonymous
- Anonymous
March 13, 2018
Hi, is there any logging on the machines that I can use to diagnose why I not getting all the data into the system?- Anonymous
April 09, 2018
The comment has been removed
- Anonymous