Certificate Request from Standalone CA Certificate Authority for Operations Manager, SCOM 2012/R2
Note:
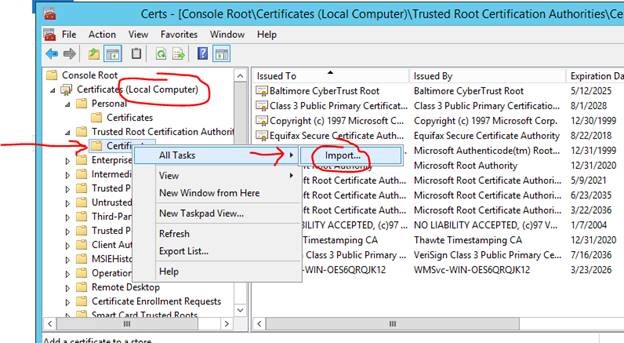
Every management server (except if it is the standalone CA) and every untrusted agent or untrusted gateway server will require installation of the ROOT CA certificate. This certificate will need to be imported into the Local Computer -> Trusted Root Certification Authorities store by using the MMC with the Certificates snap-in. Instructions below.
Every untrusted (or non-domain) agent/machine will require installation of a client certificate issued by the ROOT CA. This certificate will need to be imported into the Local Computer ->Personal store by using MOMCertImport.exe. Instructions below.
To request a certificate from a stand-alone CA
1. Log on to the computer where you want to install a certificate (for example, the gateway server or management server).
2. Start Internet Explorer, and then connect to the computer hosting Certificate Services (for example, https://<servername>/certsrv).
3. On the Microsoft Certificate Services Welcome page, click Request a certificate.
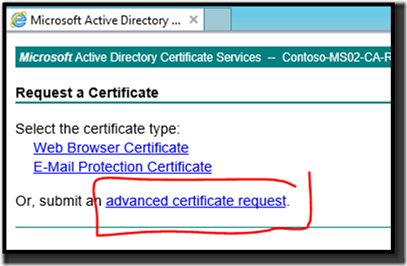
4. On the Request a Certificate page, click Or, submit an advanced certificate request.
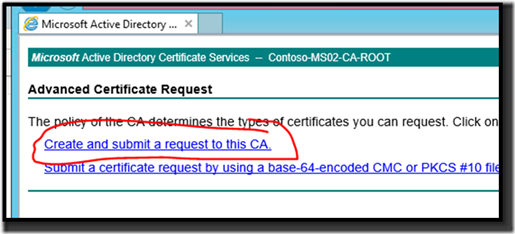
5. On the Advanced Certificate Request page, click Create and submit a request to this CA.
6. On the Advanced Certificate Request page, do the following:
7. Under Identifying Information, in the Name field, enter a unique name, for example, the fully qualified domain name (FQDN) of the computer you are requesting the certificate for. For the remaining fields, enter the appropriate information.
| Event ID 20052 of type Error is generated if the FQDN entered into the Name field does not match the computer name. |
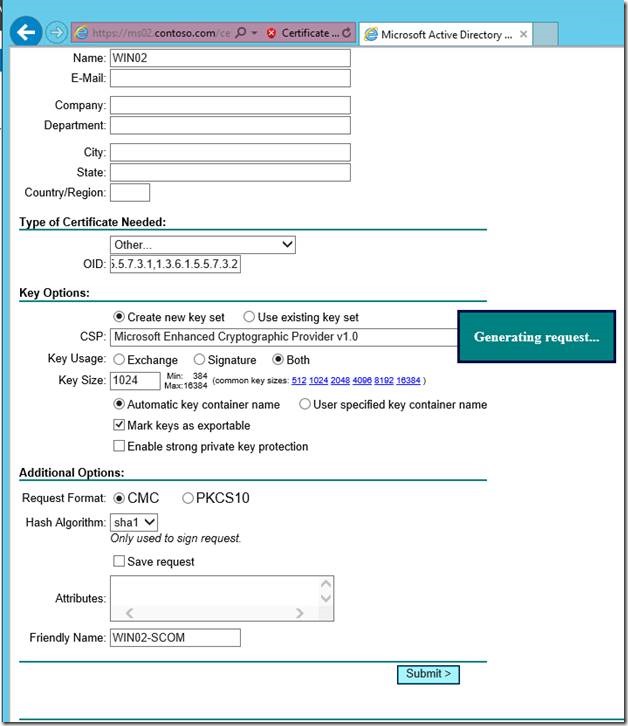
8. Under Type of Certificate Needed:
Click the list, and then select Other.
In the OID field, enter 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2
9. Under Key Options, make the following selections:
Click Create a new key set
In the CSP field, select Microsoft Enhanced Cryptographic Provider v1.0
Under Key Usage, select Both
Under Key Size, select 1024
Select Automatic key container name
Select Mark keys as exportable
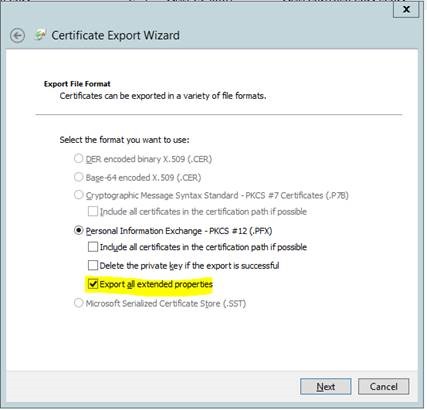
Clear Export keys to file (not required for Windows Server 2008 AD CS)
Clear Enable strong private key protection
Click Store certificate in the local computer certificate store.
10. Under Additional Options:
Under Request Format, select CMC
In the Hash Algorithm list, select SHA-1
Clear Save request to a file
In the Friendly Name field, enter the FQDN of the computer that you are requesting the certificate for.
11. Click Submit.
12. If a Potential Security Violation dialog box is displayed, click Yes.
13. If you have configured the auto-approve option on the CA, then the cert should be instantly available.
If not, you will have to manually approve on the CA then return to the web enrollment home page to “View the status of a pending certificate request”.
Navigate to your CA web enrollment page: Https://FQDN.OF.YOURSERVER/certsrv/ 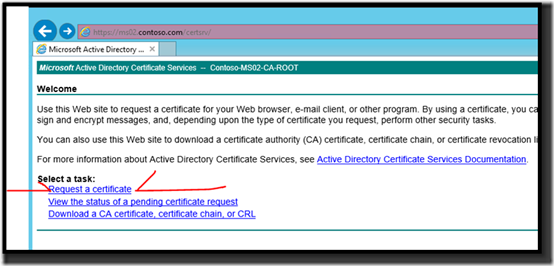
For Name: use the full computer name of the target server for which you are requesting the certificate.
To request a certificate from a stand-alone CA
1. Log on to the computer where you want to install a certificate (for example, the gateway server or management server).
2. Start Internet Explorer, and then connect to the computer hosting Certificate Services (for example, https://<servername>/certsrv).
3. On the Microsoft Certificate Services Welcome page, click Request a certificate.
4. On the Request a Certificate page, click Or, submit an advanced certificate request.
5. On the Advanced Certificate Request page, click Create and submit a request to this CA.
6. On the Advanced Certificate Request page, do the following:
7. Under Identifying Information, in the Name field, enter a unique name, for example, the fully qualified domain name (FQDN) of the computer you are requesting the certificate for. For the remaining fields, enter the appropriate information.
Event ID 20052 of type Error is generated if the FQDN entered into the Name field does not match the computer name. |
8. Under Type of Certificate Needed:
Click the list, and then select Other.
In the OID field, enter 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2
9. Under Key Options, make the following selections:
Click Create a new key set
In the CSP field, select Microsoft Enhanced Cryptographic Provider v1.0
Under Key Usage, select Both
Under Key Size, select 1024
Select Automatic key container name
Select Mark keys as exportable
Clear Export keys to file (not required for Windows Server 2008 AD CS)
Clear Enable strong private key protection Click Store certificate in the local computer certificate store.
10. Under Additional Options:
Under Request Format, select CMC
In the Hash Algorithm list, select SHA-1
Clear Save request to a file
In the Friendly Name field, enter the FQDN of the computer that you are requesting the certificate for.
11. Click Submit.
12. If a Potential Security Violation dialog box is displayed, click Yes.
13. If you have configured the auto-approve option on the CA, then the cert should be instantly available.
If not, you will have to manually approve on the CA then return to the web enrollment home page to “View the status of a pending certificate request”.
To approve the pending certificate request
1. Log on to the computer hosting Certificate Services as a certification authority administrator.
2. On the Windows desktop, click Start, point to Programs, point to Administrative Tools, and then click Certification Authority.
3. In Certification Authority, expand the node for your certification authority name, and then click Pending Requests.
4. In the results pane, right-click the pending request from the previous procedure, point to All Tasks, and then click Issue.
5. Click Issued Certificates, and confirm the certificate you just issued is listed.
6. Close Certification Authority.
To retrieve the certificate
1. Log on to the computer where you want to install a certificate (for example, the gateway server or management server).
2. Start Internet Explorer, and connect to the computer hosting Certificate Services (for example, https://<servername>/certsrv).
3. On the Microsoft Certificate Services Welcome page, click View the status of a pending certificate request.
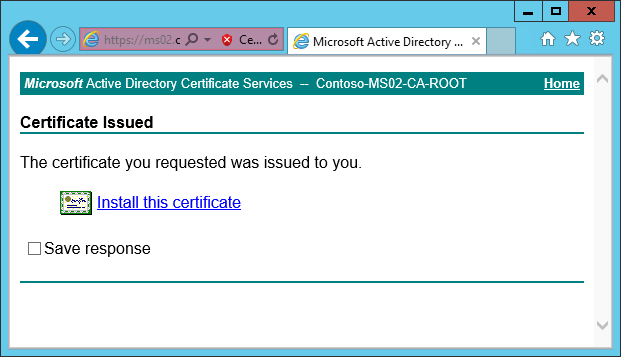
4. On the View the Status of a Pending Certificate Request page, click the certificate you requested.
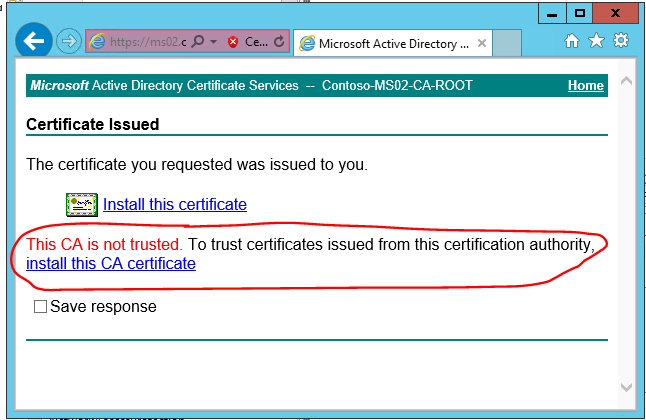
5. On the Certificate Issued page, click Install this certificate.
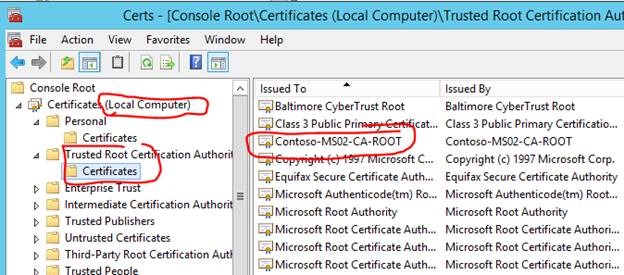
*You will also have to install the ROOT CA certificate into the Local Computer -> Trusted Root Certification Authorities store on ALL management servers (except the CA) and ALL untrusted agent machines. See screenshots below.
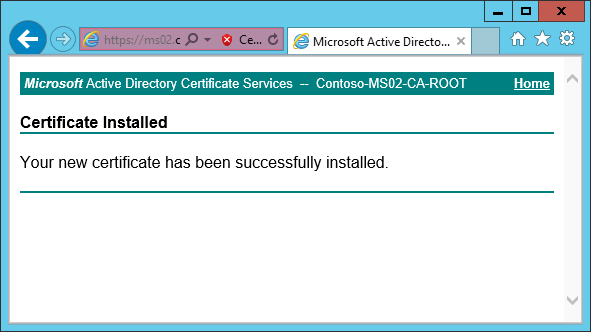
6. In the Potential Scripting Violation dialog box, click Yes.
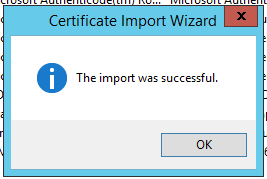
7. On the Certificate Installed page, after you see the message that Your new certificate has been successfully installed to the Current User -> Personal store.
Now you must export it and use the MOMCertImport.exe tool to import the cert into the correct Local Computer -> Personal store.
Import the ROOT CA certificate.
Shortly after you submit the request (< 60 seconds) you should see the page shown below.
If you attempt to install the cert without first having/installing the ROOT CA cert, you will see an option appear to install the ROOT CA cert as shown below.
Install the ROOT CA cert as shown below.
Save the cert.
Import it into the correct store: Local Computer -> Trusted Root Certification Authorities
Certificates Console: https://technet.microsoft.com/en-us/library/cc962086.aspx
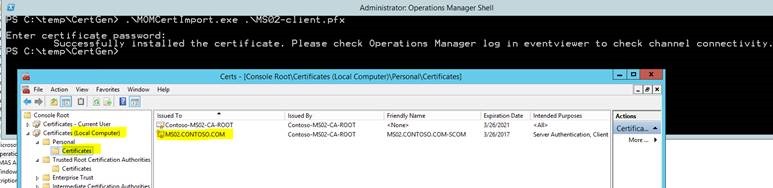
Root CA certificate is successfully imported to the Local Computer -> Personal store.
Install the Client Certificate
Click the link
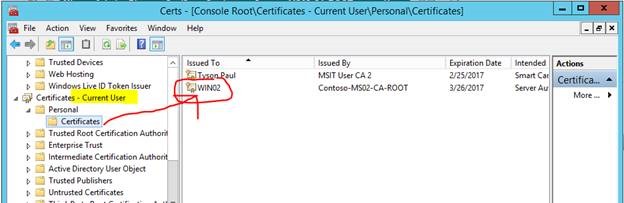
Certificate is imported to the Current User store but this needs to be in the Local Computer store
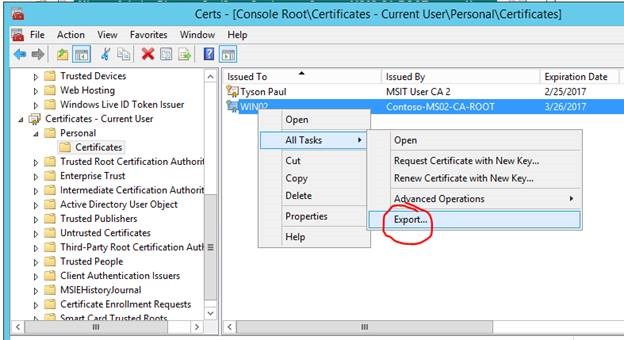
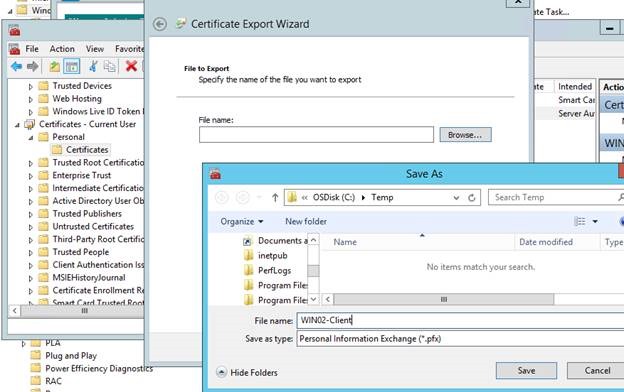
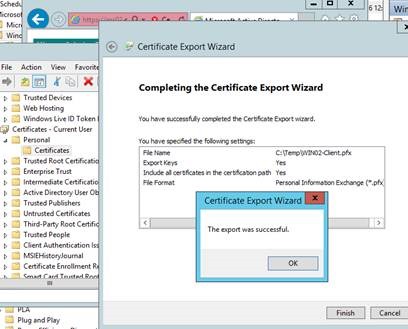
Export the certificate from the Current User store as shown below.
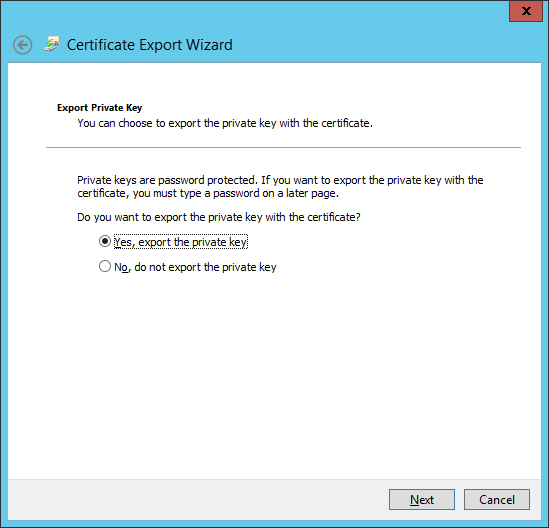
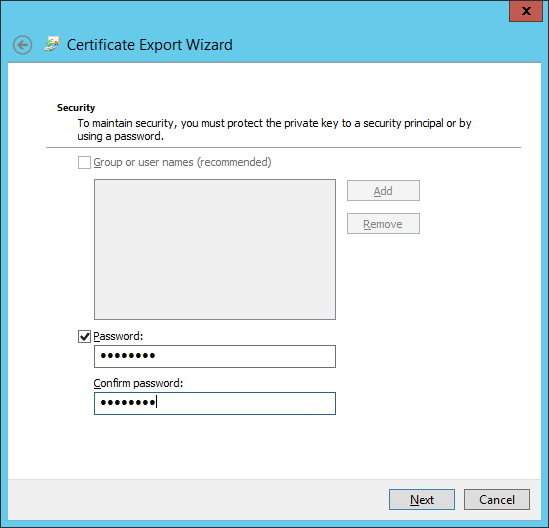
Provide a password :
Save the certificate to an easy location like C:\Temp
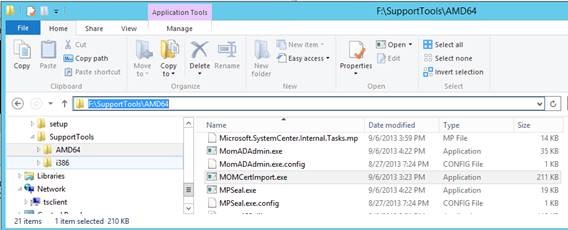
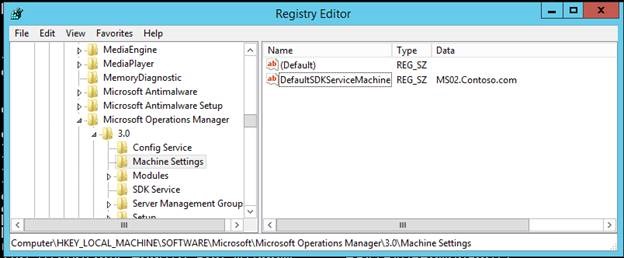
Once the client certificate is exported, use MomCertImport.exe to import the client certificate into the correct location. This also sets the serial number in the registry. This tool is located in the Support Tools folder on the SCOM installation media.
Locate the MomCertImport.exe tool. Copy it to C:\Temp , where your client cert should also be located.
Example with Powershell:
.\MOMCertImport.exe .\MS02-client.pfx
After import, the client cert will appear in the correct store.
Registry before import:
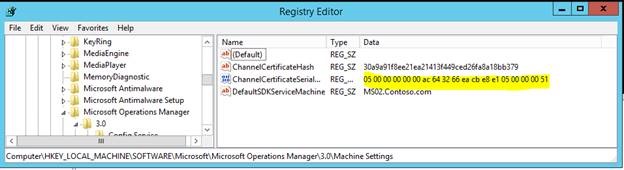
After Import:
(Notice that the thumbprint appears backwards from how it is displayed in the certificate properties. This is normal.)
Troubleshooting:
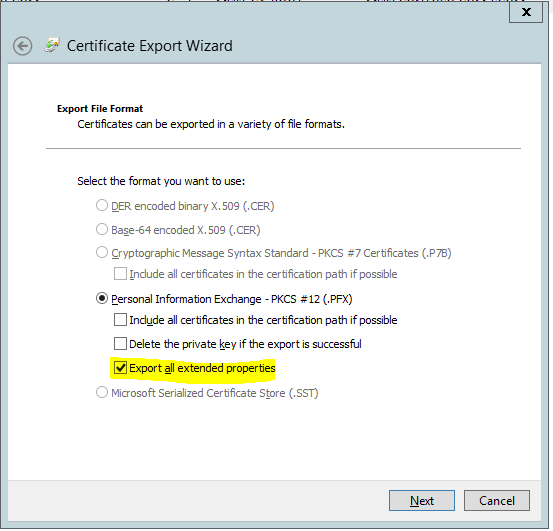
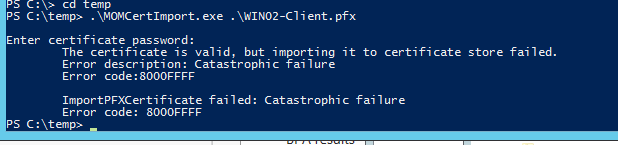
If you see this message it probably means that you exported the certificate chain. Go back, export it again according to the export wizard screenshot below.
Instructions to set up a Windows Server 2012 R2 Standalone CA here…
Comments
- Anonymous
February 23, 2017
Do these steps still hold good for SCOM 2016?- Anonymous
February 23, 2017
@ Hare Krishna Agrawal: Yes. This works on SCOM2016.
- Anonymous
- Anonymous
March 19, 2017
The comment has been removed- Anonymous
March 21, 2017
@JC, This is expected behavior. Thanks for your suggestion. I'll add a note to the screenshot of the registry.
- Anonymous
![clip_image002[8] clip_image002[8]](https://msdntnarchive.z22.web.core.windows.net/media/2016/05/clip_image0028_thumb.png)
![clip_image004[8] clip_image004[8]](https://msdntnarchive.z22.web.core.windows.net/media/2016/05/clip_image0048_thumb.png)
![clip_image008[8] clip_image008[8]](https://msdntnarchive.z22.web.core.windows.net/media/2016/05/clip_image0088_thumb.jpg)