Blocking Explicit Bing with ISA Server
Mike from Bing posted on some SafeSearch updates to Bing, particularly around image search and video preview.
So, with the new explicit domain name (explicit.bing.net), a block is easy enough to implement with ISA Server and nothing extra.
If you’ve already got a site blocking rule enabled, all you need to do is add:
*.explicit.bing.net/*
To your blocked sites URL Set, and/or
*.explicit.bing.net
To your blocked sites Domain Name Set, if you’re using one.
If you haven’t yet configured a blocking rule for explicit Bing traffic, here’s how I just did it.
First, create a new Access Rule.
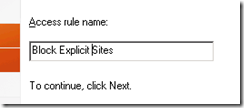
I’m calling mine “Block Explicit Sites”
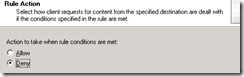
Next – we want to Deny access to these locations.
Protocol selection: I’ve selected HTTP and HTTPS (not sure if HTTPS is ever used, but it’s coverage, innit?)
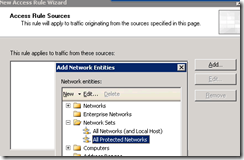
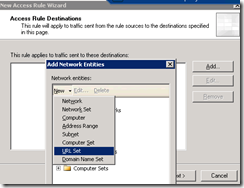
I’m picking All Protected Networks as the source, which covers every non-External ISA network (click Add… to see the list, then Add and Close the All Protected Networks Network Set).
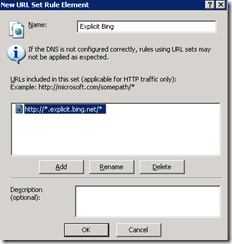
For the target, we want to create a new URL set, which is probably enough to stop accidental browsing of the target domains for Web Proxy clients that aren’t doing their own name resolution, and won’t have a huge amount of DNS traffic associated with it.
I’ll call it Explicit Bing, and set the path to https://*.explicit.bing.net/*
This should apply to all subdomains, so if we end up with more specific categorization within the explicit domain at some point, it’ll automatically cover it.
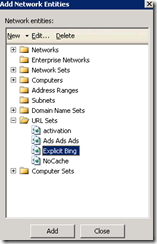
Once that’s there, click OK, then add the Explicit Bing URL Set to the rule (find it under URL sets, click Add and then Close).
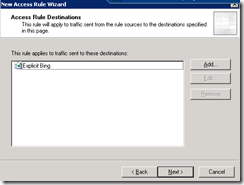
The Wizard should look like this:
From here, it’s just Next to apply to All Users (so it’s an anonymous blocking rule – doesn’t require authentication first in order to block someone) until the Wizard finishes.
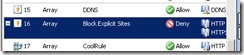
There’s my rule:
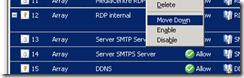
My rule ended up at #16 in my list, so a little trick with reordering: Shift-select all 15 rules above it, and then right-click any of the selected rules, and choose Move Down.
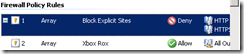
And now, my new block rule is at #1. I do want it to be first as far as anonymous web traffic rules go, but I might, for example, want to position the Xbox rule or other rules ahead of it, depending on my traffic policy.
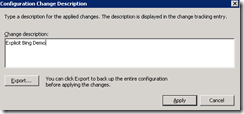
Enter the Change Tracking reason for later auditing…
And now it’s test time…
Right, well I can’t exactly show you the full search terms or the test results, but the images served from the explicit Bing domains were certainly blocked.
As a note – test from a client computer. The ISA Server itself may well have an “Allow CRL Downloads from any network using HTTP” System Policy rule in place which will run before any block lists. Disabling the System Policy rules and creating equivalent Access Rules that run after block lists will fix this.