Simplifying creation of Office Web App 2013 Farm Certificates
Hi All
I wrote a blog a while back on deploying an Office Web App Farm for Lync Server 2013. It has got quite a few hits over the past 12 months and so is obviously a topic that a lot are interested in.
I'll be honest, I did a lousy job with the certificate generation steps, so I figured I should improve my doco around simplifying the steps for generating an Office Web App Farm certificate. So here goes…..:)
What Subject Alternate Names do I need on the certificate?
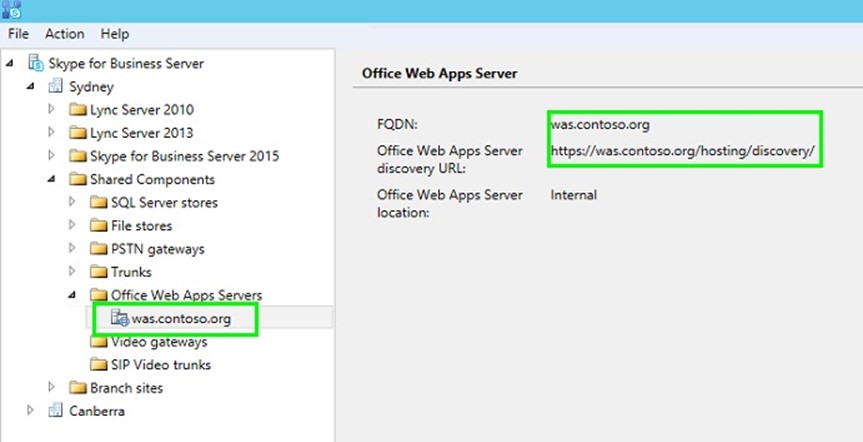
When we setup Office Web App 2013 (OWA) for Lync Server 2013 or Skype for Business 2015, the common name and subject alternate name that needs to be on the certificate is the name of the Office Web App Farm added in the Skype Topology Builder. In my lab, I have called my Office Web App Farm was.contoso.org. So the key name on need to have on my Office Web App Certificate is was.contoso.org, as that will be the URL clients are passed by my Skype/Lync Servers went attempting access the Office Web App service.
Now while the key name on the certificate is was.contoso.org, I plan to deploy Office Web App on 2 or more OWA servers load balanced behind a Hardware Load Balancer. When testing Office Web App Servers are working correctly I normally use the https://serverfqdn.contoso.com/hosting/discovery URL, and so in order to avoid any certificate errors being raised by this testing HTTPS request I generally add the FQDN's of the servers that will be members of the Office Web App Farm. So in my case I will have two servers was01.contoso.org and was02.contoso.org on my certificate as Subject Alternate Names. Please note though, I believe while useful to have the Server FQDNs on the certificate these SANs are not strictly required.
Private Key Exportable
As I plan to use the same certificate, with the same Friendly Name on both of my OWA servers, I will configure my OWA certificate with the private key exportable option. This will mean I can request the certificate on one server, export it on that server, and then import it on my second and subsequent OWA servers.
Certificate Friendly Name
When you setup an Office Web App Farm, you are required to provide the certificate that will be used by the farm's Friendly Name. This is yet another reason to use the same certificate across the two OWA servers. Make sure you create the certificate with an appropriate Friendly Name :).
Requesting a Certificate
The simplest way I have found of requesting a certificate for OWA, is to use the certreq utility. The certreq utility takes a .inf file as input. The .inf file includes all of the key configuration requirements for the certificate. To generate an offline request file (.req), use the following syntax with certreq. The certreq.inf is the input file, and the resulting .req file is created on the OWA server which can then be used to generate the certificate with an appropriate Certificate Authority.
certreq -new -machine c:\bin\was.inf c:\bin\was.req
Below is an example of a certreq.inf file, with the appropriate settings for my Lab environment.
[NewRequest]
Subject="CN=was.contoso.org,OU=IT,O=Contoso,L=Canberra,S=ACT,C=AU"
Exportable=TRUE
KeyLength=2048
MachineKeySet=TRUE
FriendlyName="Contoso Office Web App Cert"
KeySpec=1
[EnhancedKeyUsageExtension]
OID=1.3.6.1.5.5.7.3.1
[Extensions]
2.5.29.17 = "{text}"
_continue_ = "dns=was.contoso.org&"
_continue_ = "dns=was01.contoso.org&"
_continue_ = "dns=was02.contoso.org&"
[RequestAttributes]
CertificateTemplate=WebServer
Once you have created the .req file, you can then submit the .req file to your certificate authority. There is a pretty simple way of doing this, and doesn't involve going to the https://YourCA-FQDN/certsrv URL. You can request the certificate with certreq as well. The syntax for certreq to create the certificate file is as follows.
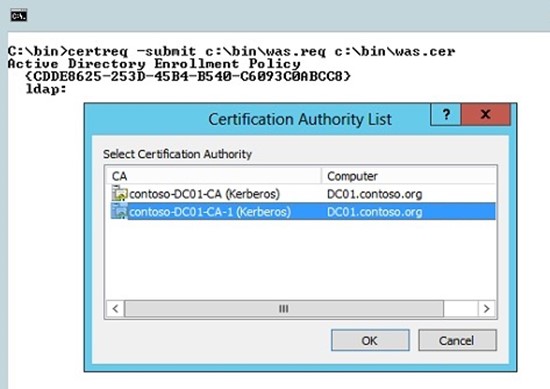
certreq -submit c:\bin\was.req c:\bin\was.cer
When you use certreq to submit the .req file to a Certificate Authority in your environment, you are prompted by CertReq (with a Popup dialog – see below) to select the appropriate Certifcate Authority with which to submit the request. In my environment I have two CA's, one from a DC I rebuilt and recreated the CA on (so the old CA is no longer, I just haven't cleaned up AD to remove the old CA references). The second CA listed in the gui provided by CertReq is my active Certificate Authority and the CA I wish to use to generate the certificate file. So you select your CA and click the ok button.
Once the .req has been processed by your CA a .cer is created in the path provided to the certreq utility. So I am now able to import the certificate onto my first OWA server in the soon to be created OWA farm. Well the good news is I don't need to fire up Certificate Manager (which you can get to with certlm.msc in 2012 and Windows8+ – pretty neat I reckon) to do an import, you can do the import with the certreq utility (golf clap
to certreq  ). The syntax for importing the newly created .cer file is as follows:
). The syntax for importing the newly created .cer file is as follows:
certreq -accept -machine was.cer
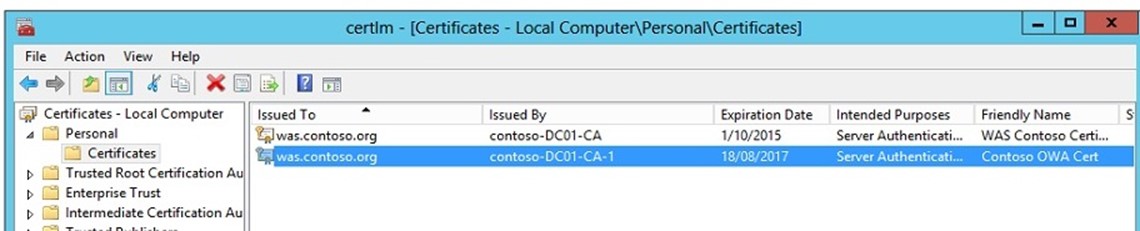
The certificate has now been added to the Machine certificate store with a private key that is exportable and the selected Friendly Name. To dot the "i's" and cross the "t's" go and check in the certificate store that all is good. You can do that by running certlm.msc which will fire up Certificate Manager for the computer store.
voila, I now have a new certificate ready to be used in creating the Office Web App Farm.
So to conclude to create your new OWA cert do:
– Create the .inf with the appropriate settings in it.
– Run certreq to create the request file
certreq -new -machine c:\bin\was.inf c:\bin\was.req
– Run certreq to create the .cer using your internal CA
certreq -submit c:\bin\was.req c:\bin\was.cer
– Run certreq to import the .cer into the machine certificate store
certreq -accept -machine was.cer
I hope that helps others wishing to setup certs for a OWA farm.
Happy Skype'ing.
Steve