Disable SMB v1 in Managed Environments with Group Policy
The following is a brief summary recent SMB v1 vulnerabilities, ransomware and an enterprise approach to disabling SMB v1 via Group Policy.
Why SMB v1 Isn’t Safe (September 16, 2016)
Ned Pyle wrote a blog post in September of 2016 on why SMBv1 isn’t safe where he stated that if your clients use SMB1, then a man-in-the-middle can tell your client to ignore security settings like:
- Pre-authentication Integrity (SMB 3.1.1+). Protects against security downgrade attacks.
- Secure Dialect Negotiation (SMB 3.0, 3.02). Protects against security downgrade attacks.
- Encryption (SMB 3.0+). Prevents inspection of data on the wire, MiTM attacks. In SMB 3.1.1 encryption performance is even better than signing!
- Insecure guest auth blocking (SMB 3.0+ on Windows 10+) . Protects against MiTM attacks.
- Better message signing (SMB 2.02+). HMAC SHA-256 replaces MD5 as the hashing algorithm in SMB 2.02, SMB 2.1 and AES-CMAC replaces that in SMB 3.0+. Signing performance increases in SMB2 and 3.
“...If your clients use SMB1, then a man-in-the-middle can tell your client to ignore all the above” Please review Ned Pyle’s full blog article on Why SMB1 isn’t safe
TechNet Guidance on Enabling/Disabling SMBv1/2/3 (February 28, 2017)
Microsoft in February updated and published a TechNet article on how to enable or disable various versions of SMB using:
- The Registry Editor for LanmanServer
- PowerShell’s Set-SmbServerConfiguration for SMB server
- sc.exe with config options for lanmanworkstation
Caution! While these tools can work for quick configuration changes, this combination approach is not very manageable in large-scale managed enterprise environments where consistent configuration is required.
Microsoft Published Security Bulletin MS17-010 (March 14, 2017)
Microsoft released a critical Security Update for Microsoft Windows SMB Server security bulletin and updates under KB 4013389 along with a host of security updates for all supported versions of Windows under MS17-010.
Enter Global Ransomware Attack (May 12, 2017)
The WannaCrypt ransomware attack began exploiting the SMB v1 server vulnerability and began spreading globally on May 12.
U.S. CERT Advisory (May 12, 2017)
CERT issued an advisor for Indicators Associated With WannaCry Ransomware with the following recommendations:
Apply the patch (MS17-010). If the patch cannot be applied, consider:
- Disabling SMBv1 and
- blocking all versions of SMB at the network boundary by blocking TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139, for all boundary devices.
SMB Vulnerability Patch for Windows XP & Server 2003 (May 13, 2017)
Microsoft then released SMB security patches for Windows XP and Server 2003 on May 13, 2017.
Enterprise Approach to Disable SMB v1 using GPO
Certainly, it’s important to patch against the known SMB v1 vulnerabilities released in MS17-010 and subsequent KB 4013389 for Windows XP/2003. However because of numerous variants of WannaCrypt and these other known security issues with SMB v1 (e.g. man-in the middle); many organizations have issued mandates to completely disable SMBv1 as strategic security countermeasure against future threats.
An enterprise approach to disabling SMB v1 is to use Active Directory (AD) Group Policy preferences to configure and enforce the registry settings related to disabling SMBv1 client and server components for Windows Vista and Server 2008 and later.
Group Policy registry preference items allow you to create, update, replace, and delete keys and values in the Windows registry. The following are the registry keys that need to be created or updated to disable SMB v1.
Disable SMBv1 Server with Group Policy:
This will configure the following new item in the registry
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Registry entry: SMB1 REG_DWORD: 0 = Disabled
To configure this using Group Policy:
- Open the Group Policy Management Console. Right-click the Group Policy object (GPO) that should contain the new preference item, and then click Edit.
- In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
- Right-click the Registry node, point to New, and select Registry Item.
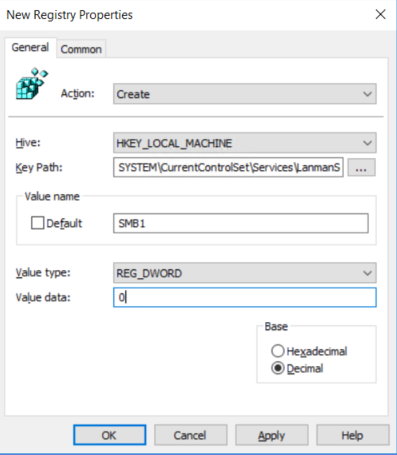
In the New Registry Properties dialog box, select the following:
- Action: Create
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
- Value name: SMB1
- Value type: REG_DWORD
- Value data: 0
This disables the SMBv1 Server components. This Group Policy needs to be applied to all necessary workstations, servers, and domain controllers in the domain.
Note: WMI filters can also be set to exclude unsupported operating systems or selected exclusions such as Windows XP.
Caution! Be careful when making these changes on domain controllers where legacy Windows XP or older Linux and 3rd party systems (that do not support SMBv2 or SMBv3) require access to SYSVOL or other file shares where SMB v1 is being disabled.
Disable SMBv1 Client with Group Policy:
To disable the SMBv1 client the services registry key needs to be updated to disable the start of MRxSMB10 and then the dependency on MRxSMB10 needs to be removed from the entry for LanmanWorkstation so that it can start normally without requiring MRxSMB10 to first start.
This will update and replace the default values in the following 2 items in the registry
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\mrxsmb10
Registry entry: Start REG_DWORD: 4 = Disabled
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanWorkstation
Registry entry: DependOnService REG_MULTI_SZ: “Bowser","MRxSmb20","NSI"
Note: The default included MRxSMB10 which is now removed as dependency
To configure this using Group Policy:
- Open the Group Policy Management Console. Right-click the Group Policy object (GPO) that should contain the new preference item, and then click Edit.
- In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
- Right-click the Registry node, point to New, and select Registry Item.
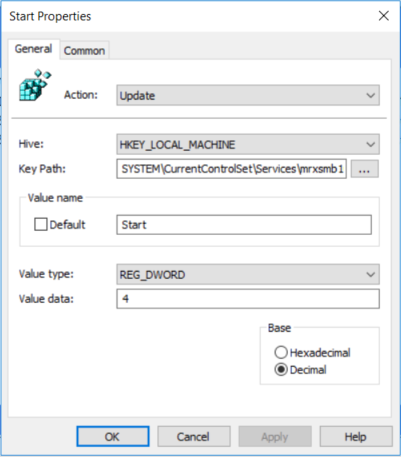
In the New Registry Properties dialog box, select the following:
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\services\mrxsmb10
- Value name: Start
- Value type: REG_DWORD
- Value data: 4
Then remove the dependency on the MRxSMB10 that was just disabled
In the New Registry Properties dialog box, select the following:
- Action: Replace
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\LanmanWorkstation
- Value name: DependOnService
- Value type REG_MULTI_SZ
- Value data:
- Bowser
- MRxSmb20
- NSI
Note: These 3 strings will not have bullets (see below) 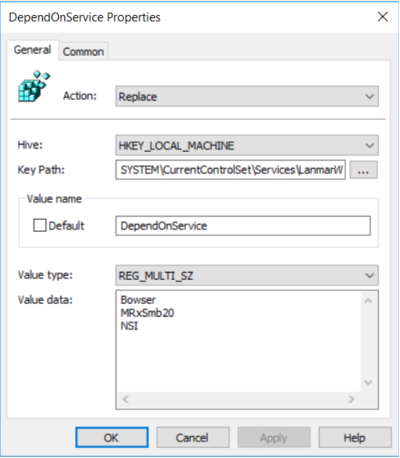
The default value includes MRxSMB10 in many versions of Windows, so by replacing them with this multi-value string, it is in effect removing MRxSMB10 as a dependency for LanmanServer and going from four default values down to just these three values above.
Note: When using Group Policy Management Console, there is no need to use quotation marks or commas. Just type the each entry on individual lines as shown above:
Reboot Required
After the policy has applied and the registry settings are in place, the targeted systems must be rebooted before SMB v1 is disabled.
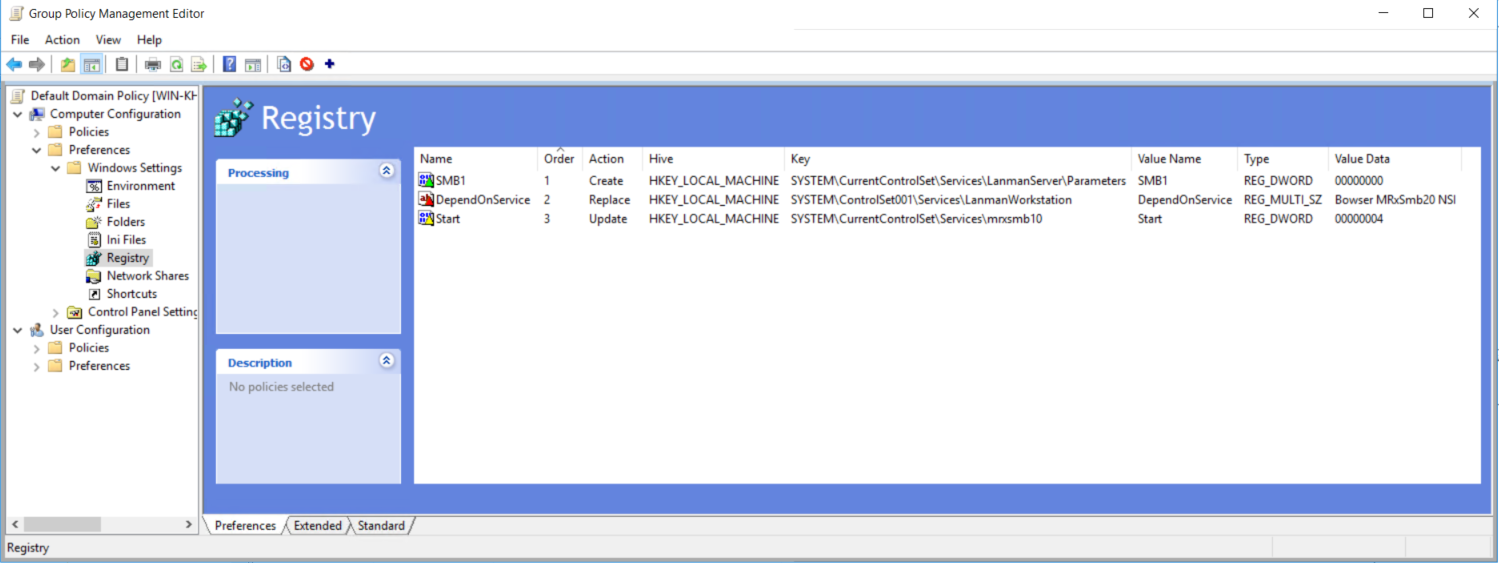
Summary
If all the settings are in the same Group Policy Object (GPO), Group Policy Management will show the settings below.
Testing and Validation
Once these are configured, then allow the policy to replicate and update. As necessary for testing, run gpupdate /force from a CMD.EXE prompt and then review the target machines to ensure the registry settings are getting applied correctly. Make sure SMB v2 and SMB v3 is functioning for all other systems in the environment.
Caution! Don't forget to reboot the targeted systems.
Additional SMB v1 Resources
- https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1/
- https://www.us-cert.gov/ncas/current-activity/2017/01/16/SMB-Security-Best-Practices
- https://support.microsoft.com/en-us/help/204279/direct-hosting-of-smb-over-tcp-ip
Comments
- Anonymous
May 17, 2017
The comment has been removed- Anonymous
May 17, 2017
Thanks, I corrected this typo
- Anonymous
- Anonymous
May 17, 2017
"Bowser"?- Anonymous
May 17, 2017
Yes. Notice the Support Article which also references "bowser" when using SC.EXE to remove the dependencysc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsisc.exe config mrxsmb10 start= disabled- Anonymous
May 17, 2017
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
May 17, 2017
Many thanks Troy, great article.Is this GPO going to disable SMBv1 for all Windows client and server versions?- Anonymous
May 17, 2017
The comment has been removed
- Anonymous
- Anonymous
May 17, 2017
Just want to confirm that in the "DependOnService" you create value data with the name of "bowser" is it a typo, shouldn't it be browser ?- Anonymous
May 17, 2017
"Bowser" without an "r" is the name of the registry entry in HKLM\SYSTEM\CurrentControlSet\Services\
- Anonymous
- Anonymous
May 17, 2017
Won't this need a reboot to effect these changes - or at least a restart of the services mentioned - and stopping of MRxSMB10? Checking the registry entries are present will not remove the vulnerability until the services are restarted.- Anonymous
May 17, 2017
Yes, this will require a reboot
- Anonymous
- Anonymous
May 17, 2017
The comment has been removed- Anonymous
May 17, 2017
I removed the quotes on the strings and put them on 3 separate lines with a note for clarification to look at the image.Thanks
- Anonymous
- Anonymous
May 17, 2017
Thanks. The option is ticked and (installed) but greyed out on my 2012r2 dcs? - Anonymous
May 17, 2017
Your Summary screenshot shows the "DependOnService" registry setting is under SYSTEM\ControlSet001\Services....But, the information before that has the Registry setting SYSTEM\CurrentControlSet\Services...- Anonymous
May 17, 2017
Yes, thanks for finding this...I have corrected the image.
- Anonymous
- Anonymous
May 17, 2017
Does anyone have a registry edit for server 2012 r12 - Anonymous
May 17, 2017
In case of server active direct AD disable smb gives problem? - Anonymous
May 17, 2017
The comment has been removed- Anonymous
May 21, 2017
Please vote up my Script Center request for a comprehensive PowerShell script to "Disable SMBv1 client and server protocols across ALL supported Windows OSes", which should uninstall the FS-SMB1 Windows feature in new OSes and complete the multiple steps to disable client and server v1 protocol on older OSes. https://gallery.technet.microsoft.com/scriptcenter/site/requests/Disable-SMBv1-client-and-server-protocols-across-ALL-supported-Windows-OSes-80d26f6f
- Anonymous
- Anonymous
May 17, 2017
Excellent GPO step by step. - Anonymous
May 17, 2017
Yesterday, I rolled out these configurations and users are reporting today that they are not able to scan documents from printers in to the folders. any idea ?- Anonymous
May 18, 2017
Any help, as users are not able to scan to folders via printer, also users are not able to access shared folders created on Linux samba server. I have deleted GPO, reboot the workstations, GPO is not showing when I ran "GPresult /R" but configurations are still showing in registry, urgent help to revert it back will be highly appreciated. Regards,- Anonymous
May 18, 2017
Can anybody tell me how to revert these GPO settings, which are not applied on all machines ?- Anonymous
May 18, 2017
Change the settings back to Start=2 and SMB1=1. For the DependOnService value, add Mrxsmb10 back into the list as a fourth value for LanmanWorkstation. Then reboot again.
- Anonymous
- Anonymous
- Anonymous
- Anonymous
May 18, 2017
Thanks for this useful information.One thing I noticed - after implementing the changes, and checking a W10 domain client has the registry changes then rebooting, the "SMB 1.0/CIFS File Sharing Support" still remains ticked in Windows Features.- Anonymous
May 18, 2017
On Windows 10 and Server 2012 R2 and later the SMB1 feature will still be installed on the system. You can uninstall them using Programs and Features.- Anonymous
May 18, 2017
Thanks.So it's safely disabled but just left installed, and uninstallation via programs and features should not be necessary, is this correct?
- Anonymous
- Anonymous
- Anonymous
May 18, 2017
Very helpful post. Detailed but to the point. - Anonymous
May 18, 2017
Does the order of the changes matter? (1 Create, 2 Replace, and 3 Update)?- Anonymous
May 18, 2017
As long as you make all changes to GPO/registry first and then reboot it will not matter as the changes will not take place until after the reboot. Remember the 2 client settings are independent of the SMB server settings.
- Anonymous