Always Encrypted with Secure Enclaves - Try It Now in SQL Server 2019 Preview!
Last year, we revealed our efforts to bring confidential computing capabilities of Always Encrypted to the next level, by leveraging secure enclave technologies. Over the last twelve months, the SQL team, alongside Microsoft Research, Windows and Developer Tools groups, have worked together to make the SQL Server platform the first commercial RDBMS that can protect sensitive data in use while preserving the ability of the database to support rich operations on the protected data.
Today, we are super excited to announce that you can now try and evaluate Always Encrypted with secure enclaves in the preview of SQL Server 2019.
Always Encrypted with secure enclaves in SQL Server 2019 preview uses an enclave technology called Virtualization Based Security (VBS) memory enclaves in the upcoming version of Windows (Windows Server 2019 and Windows 10, version 1809), which is currently also in preview. A VBS enclave is an isolated region of memory within the address space of a user-mode process. The isolation of VBS enclaves is provided by the Windows hypervisor, which makes VBS enclaves appear as black boxes, not only to the processes containing them, but also all other processes and the Windows OS on the machine. Even machine administrators are not able to see the memory of the enclave. The below screenshot shows what an admin would get to see when browsing the enclave memory using a debugger (note the question marks, as opposed to the actual memory content).
[caption id="attachment_3305" align="aligncenter" width="425"]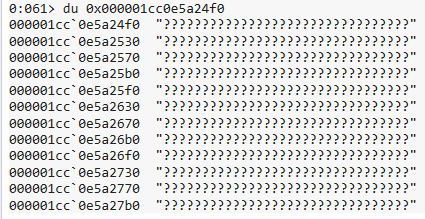 Browsing a VBS enclave with WinDbg[/caption]
Browsing a VBS enclave with WinDbg[/caption]
An instance of SQL Server 2019 preview can be configured to contain a VBS enclave for Always Encrypted, which adds the following new capabilities:
- In-place encryption. You can now encrypt your column, rotate a column encryption key, or change an encryption type of a column, without moving your data out of the database – the data can be encrypted, re-encrypted or decrypted locally on the server side, inside the secure enclave. And, you can trigger such cryptographic transformations using
ALTER TABLE ALTER COLUMNTransact-SQL statements, without client-side tools, such as Always Encrypted wizard in SSMS or PowerShell. - Rich computations. The SQL Server Engine can now delegate some operations on encrypted database columns to the enclave, which can decrypt the sensitive data and execute the operations requested in the query on plaintext values. This dramatically expands the types of queries supported on sensitive data, and therefore opens Always Encrypted to new scenarios and new applications. The new operations supported in SQL Server 2019 preview are pattern matching (
LIKE) and equality comparisons on columns using randomized encryption (which is stronger than the alternative deterministic encryption).
Note: Rich computations are pending several performance optimizations and include limited functionality (e.g., you cannot create indexes to support rich computations). Therefore, they are disabled by default. See the online docs on how to enable them.
Our next goals include:
- Enabling indexing to accelerate rich computations (
LIKE, range queries) on encrypted columns. - Adding support for Intel SGX enclaves, which are now available in Azure. This will enable us to bring Always Encrypted with secure enclaves to Azure SQL Database customers.
You can find comprehensive documentation on the new capabilities and on how to get started with Always Encrypted with secure enclaves at https://aka.ms/AlwaysEncryptedwithSecureEnclaves. We will also continue discussing this fascinating technology on this blog. And, if you are at Ignite in Orlando this week, make sure you join our session: BRK3157 - Confidential computing with SQL secure enclaves, or you can also watch its recording.
We are looking forward to hearing your feedback and partnering with you on your Proof of Concept projects exploring the new functionality of Always Encrypted. You can contact us directly at AEwithEnclaves@microsoft.com.