How to enable Bitlocker and escrow the keys to Azure AD when using AutoPilot for standard users
Welcome to our first blog post! This will be the first of many which we hope you find useful and informative when it comes to anything Windows client and Microsoft 365 Powered Device.
Our mission at Microsoft has been focused on accelerating digital transformation while empowering every person and every organization on the planet to achieve more. To reflect onto this statement, we have been designing solutions to simplify device complexity, harness the power of the cloud, enabling new and easy ways to collaborate while enhancing the security platform. In this post, we will focus on the modern deployment and management of a device when it comes to protecting data at rest. We will show you how to enable BitLocker Disk Encryption and automate the process for an AutoPilot device that is provisioned for a standard user using the Windows 10 Fall Creators Update version 1709.
A bit of history…
On June 30th 2017, Microsoft Intune received an update to allow BitLocker configuration where you are able to configure disk encryption settings (article here) under the “Endpoint Protection” profile as shown below:
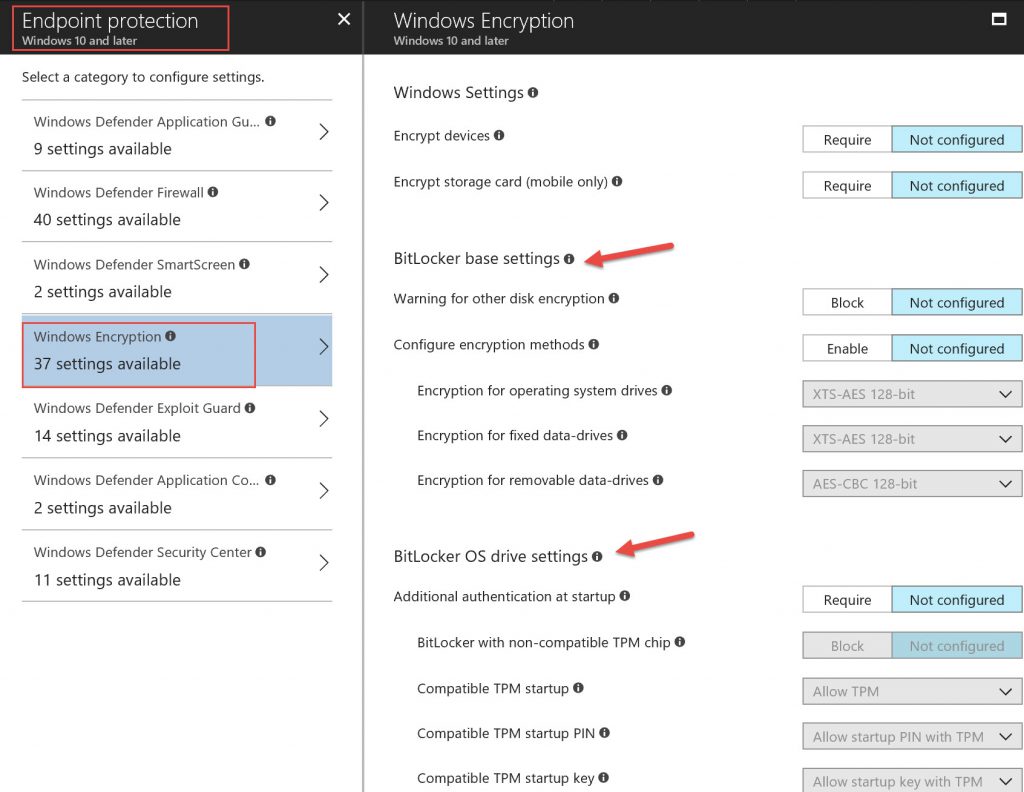
After the device sync to Azure AD and gets the new settings thru Intune, it will prompt end user in the system tray for further actions:
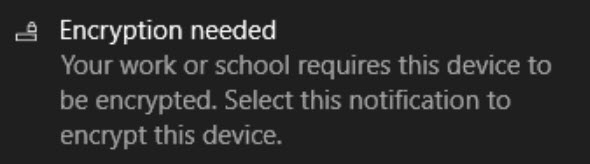
Once you click on the notification, you will be presented with this dialog box:
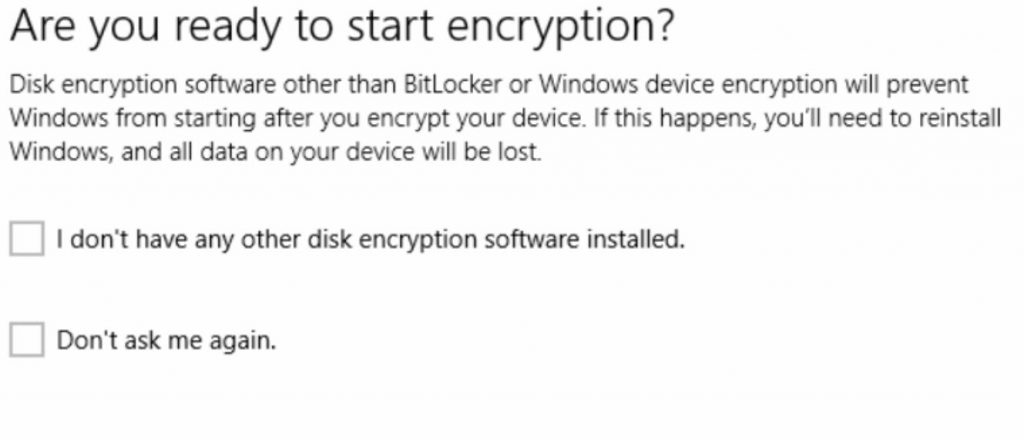
And then encryption starts.
You are able to retrieve your BitLocker key by visiting https://myapps.microsoft.com and logging in with your AAD credentials and selecting your profile. You will see a list of all of your devices and a link to ‘Get BitLocker Keys’
The above method works great as long as you are local admin on the device and as you can see it requires user intervention which is not ideal in modern deployment where simplification is a concern for every organization. For most corporate IT organizations this is a far less than optimal solution.
Pieter Wilgeven wrote a great blog here on BitLocker Encryption using AAD/MDM and it documents the process involved on how to automate BitLocker Disk Encryption regardless of hardware capabilities. In his blog, you are able to download 2 Zip files (TriggerBitlocker and TriggerBitlockerUser) which are basically scripts wrapped into an MSI in order to be deployed thru Intune to any groups of users. As seen below under the Intune service in Azure, select Mobile Apps --> Apps --> click on the “+” next to Add and select “Line of Business app” from the dropdown menu, and then select the MSI file you downloaded from Pieter’s blog.
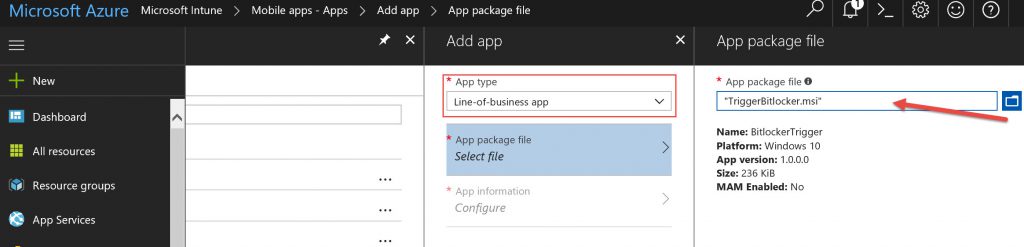
Finalize the configuration per your need and then assign this app to your user group. As long as the user logged in is an admin, the TriggerBitLocker.msi installs itself on the targeted user device and extract onto c:\Programs Files (x86)\BitLockerTrigger where you will find 3 files(Enable_BitLocker.ps1, Enable_BitLocker.vbs, and Enable_BitLocker.xml). The vbs kicks off the powershell script and the xml file which is used to create task scheduler to run around 2pm.
With TriggerBitLockerUser.msi, it didn’t work for standard user logged in and UAC is prompted for users and hence we made some improvement to get the result we are looking for.
Intune enhancements in Windows 10 1709 aka Fall Creators Update/RS3
As of now, you must be admin to access BL protectors like the recovery key, and we do not enable protection until you back up the recovery key. Recently we have added the ability to upload PowerShell scripts into the Intune Management extensions to run on Windows 10 1607 or later and that is joined to Azure AD. 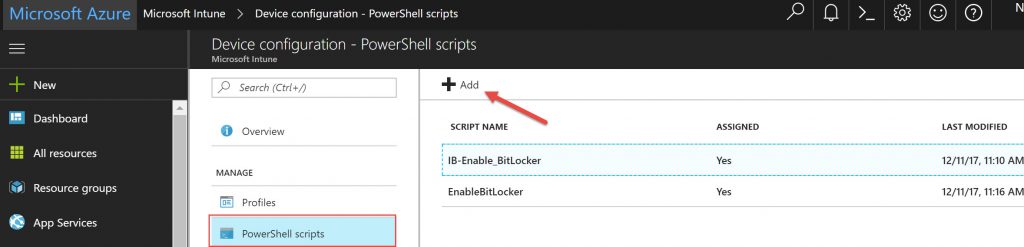
With this new capability, we are able to deploy PowerShell script running under system context to target standard users and get successful results. We have taken the Enable_BitLocker script from Pieter’s blog and made it smarter and with detailed logging for troubleshooting purpose. Running as SYSTEM, BitLocker may not implicitly load the BitLocker PowerShell module and running as SYSTEM the env variable is not set, so we explicitly had to load it using “Import-Module -Name C:\Windows\SysWOW64\WindowsPowerShell\v1.0\Modules\BitLocker” and then did multiple checks/validations to query for OS Volume Status in order to take the appropriate action plan and add required protector.
Below you will find zip file link to download which contains the powershell script that you need to upload it to your Azure tenant -->Microsoft Intune -->Device configuration--> PowerShell scripts (as seen above) and assign it to your user group to encrypt the OS drive and escrow the key to their AAD tenant. This will not only work for admins logged on to their device but also for standard users that are provisioned thru AutoPilot. As you may or may not be aware, Windows AutoPilot allows you to make the first user to login to a Windows device from the Out-Of-Box (OOBE) experience a standard user on the machine – in fact, it is the only way to come out of OOBE as a Standard user on the machine. Using AutoPilot to deploy/provision a device and automatically bring it under Intune (MDM) management also provides the ability to have additional administrators added to the machine the same way we do with a traditional AD joined device today. Watch for future posts on how AutoPilot deployed, modern managed devices can help you meet enterprise goals and significantly reduce costs while also providing an exceptional user experience.
Future Intune enhancements coming to Windows 10 1803 / RS4
As announced at Microsoft Ignite, we are working on a feature to enable automatic BitLocker (formerly: device encryption) for AAD standard users in the AutoPilot scenario in RS4 (Windows release in the spring of 2018) by having the system do this backup on behalf of the user and without the requirements of the PowerShell script mentioned above. In the meantime, this method will help you in your modern deployment/management scenarios today and you will be using AutoPilot and enabling disk encryption for Admins/Standard Users with a seamless transition to the built-in version once it ships. You can also begin testing the new version immediately by becoming a member of the Windows Insider Preview Program https://insider.windows.com.
Happy Deployment and Encryption!
Download:
Credit:
Sean McLaren and Imad Balute are experienced Technology Professionals for Modern Desktop. We are dedicated to enabling and helping enterprise customers with their digital transformation journey focusing on Modern IT around deployment, management, and security.