OS and Data disk encryption of Azure IaaS Windows VMs
VM disk encryption is achieved using Bitlocker encryption of Windows VMs and DMcrypt in Linux VMs. It leverages Azure KeyVault services to store your encryption keys which is again an additional level of security. The process is quite straight forward and encryption can be done for new as well as existing VMs. In case of Windows IaaS VMs, we can encrypt both the OS and Data disk, while in case of Linux IaaS VMs the data disk can be encrypted.You will have to use the ARM deployment model to leverage this feature, since it does not work with the classic model. There are ARM templates readily available in GitHub that can readily help you with the encryption of existing and New VMs.
In this blog, I am going to focus on the end to end procedure for Windows VM OS and Data disk encryption using KeyVault by leveraging these templates
Prerequisites:
1) Create an Azure KeyVault
This can be now done from the ARM portal itself. KeyVault is available in the Azure Portal in preview mode. You can create a new keyVault by providing basic information like KeyVault Name , Resource group Name,Location etc. In addition to that , by default your user account will have access in the "Access Policies". You can edit the "Advanced Access Policy" and enable all the three options given there
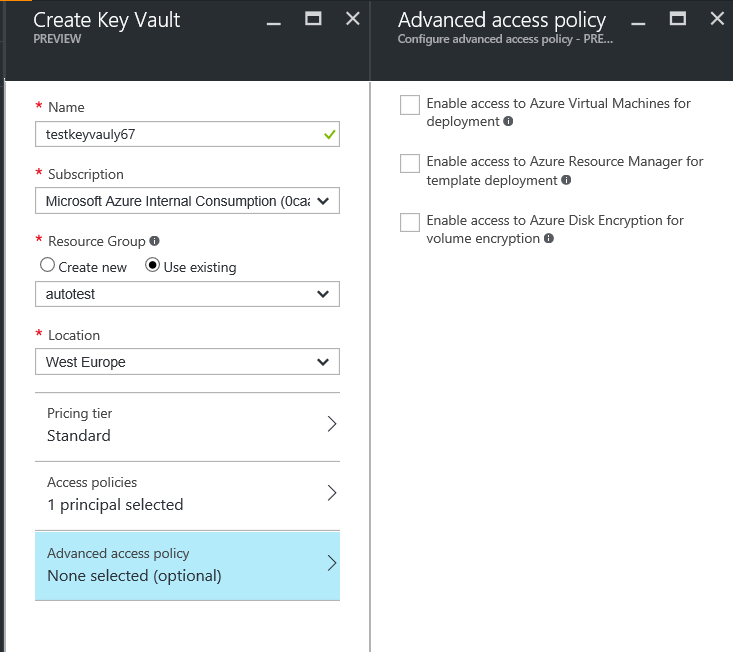
Alternately, you can also use the ARM template available at this location to create a KeyVault:
https://github.com/Azure/azure-quickstart-templates/tree/master/101-key-vault-create
This template will create a KeyVault for you with all the three advanced access policies including the Volume encryption policy that we need for Disk encryption
2) Create an application in Azure AD with permission to access KeyVault:
This is a very important step since you will be using this application id and key during VM encryption
- Select the organization's active directory from the classic portal and select the application tab
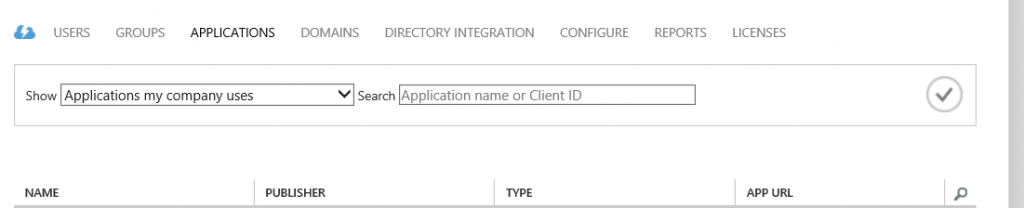
2.Click on add from the bottom menu to add a new application. Select the first option, ie add an application my organization is developing 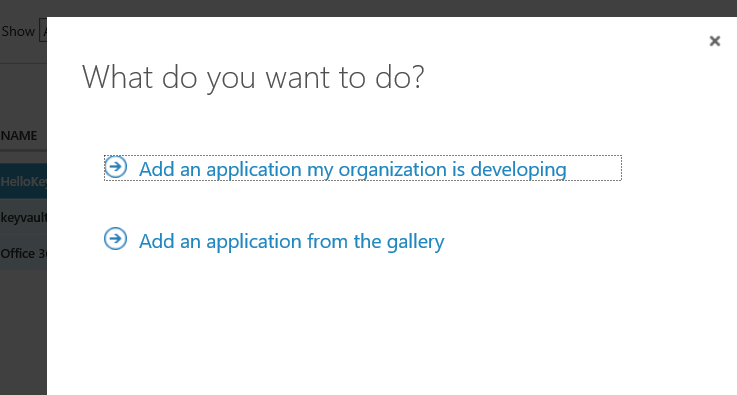
3. Provide name of the application in the next step 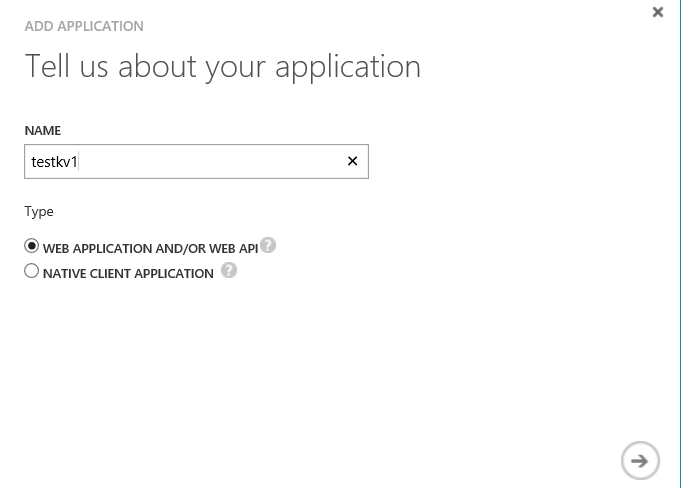
3. Add the Sign-on URL and App URI. You can enter any value here in URI format, it need not have to be an existing application. Only requirement is that it should be unique for an organization 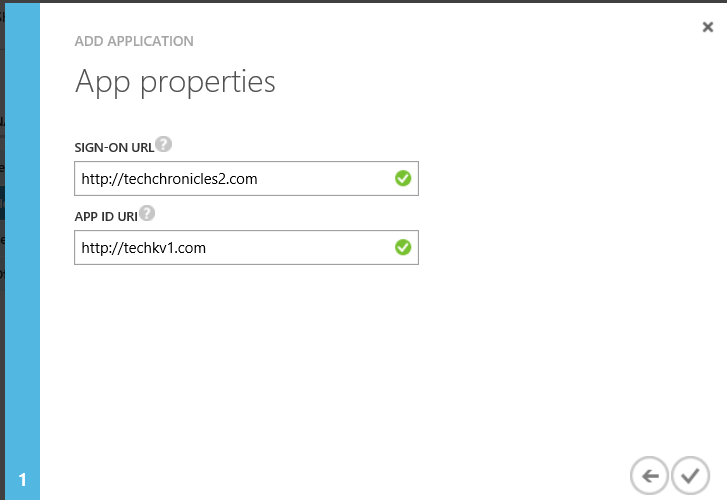
4.Now click on configure, and copy the client Id of the application 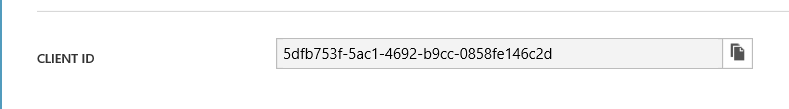
5.Next we need the application key. This can be generated from the portal from under the keys session. Select duration as 1 year from the drop down. Once you save the configuration, a key will be displayed which can be copied over 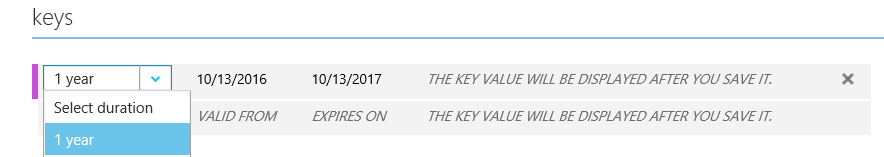
6. Next step is to provide this application access to keyvault. It can be done from an Azure PowerShell window using the following command
Set-AzureRmKeyVaultAccessPolicy -VaultName $keyVaultName -ServicePrincipalName $aadClientID -PermissionsToKeys 'WrapKey' -PermissionsToSecrets 'Set' -ResourceGroupName $rgname
You have to set the variables $keyVaultName,$aadClientID,$rgname to have values of your keyvault name, client id of the application that we got at Step 4 above and Resource group name
Now you have the client id and the key that you will need during the ARM template execution. Now lets proceed with the VM disk encryption
Create a new encrypted VM using ARM template and KeyVault
Deploy the following template available in GitHub to encrypt a new VM : https://github.com/Azure/azure-quickstart-templates/tree/master/201-encrypt-create-new-vm-gallery-image
Click on the "deploy to Azure" option in the page to deploy the ARM template directly in Azure 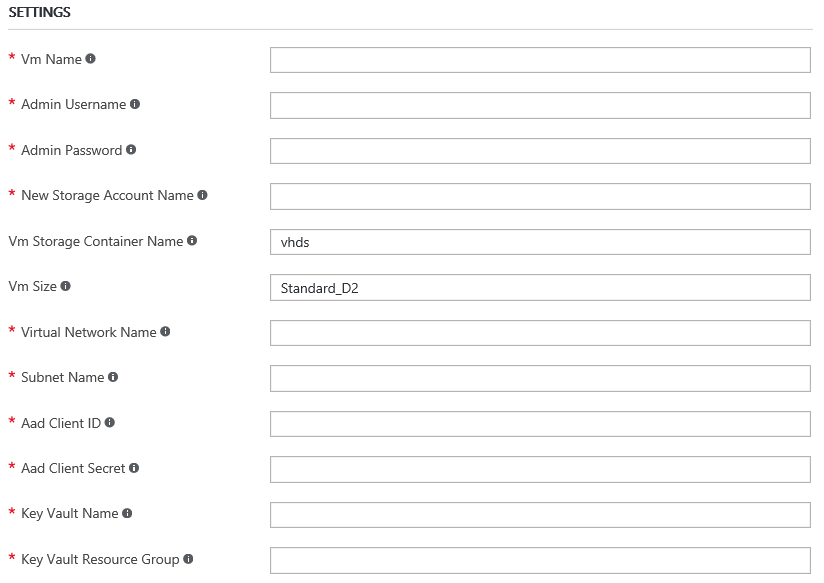
Provide the mandatory parameter values like VM name, admin username, password, Storage account name, Virtual network, subnet,keyvault name and keyvault resource group along with the client ID and Client Secret of the Azure AD application that we created earlier. Additionally there will be two options for Key Encryption key and URL.It is not mandatory and we are not using that in this example. You can then agree to the terms and conditions , click on purchase and the deployment of encrypted VM will start
Encrypt an existing VM using ARM template and keyvault
Deploy the following template available in GitHub to encrypt an existing VM : : https://github.com/Azure/azure-quickstart-templates/tree/master/201-encrypt-running-windows-vm
Deploy the template to Azure and provide details of the VM that you want to encrypt.'Volume type' can be OS,Data or All(default value) depending on which disk you want to encrypt 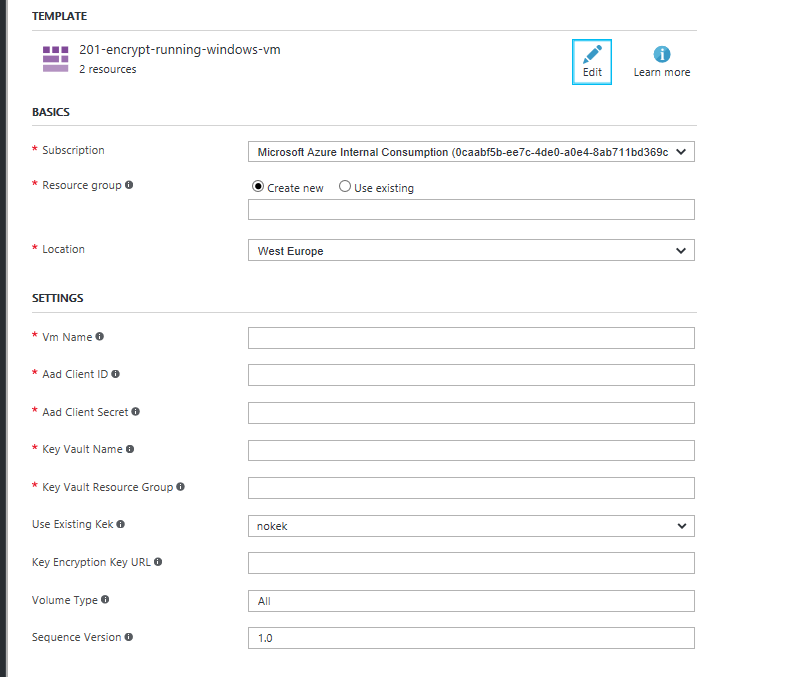
Check encryption status
Now that you have enabled the encryption you might want to verify the status. There are few ways to check this.
Easiest way is to check from the Azure portal. Navigate to the Disks information of the VM from the portal. It will show the OS disk status as Encrypted. 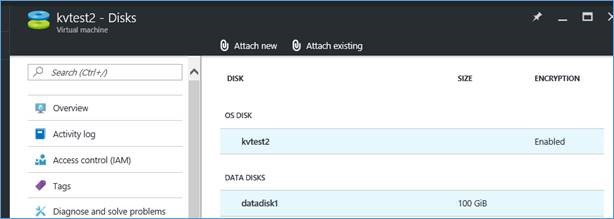
You can check the data disk encryption status by using Azure PowerShell command Get-AzureRmVmDiskEncryptionStatus and providing resource group name and Vmname as parameters
Get-AzureRmVmDiskEncryptionStatus -ResourceGroupName $rgname -VMName $Vmname
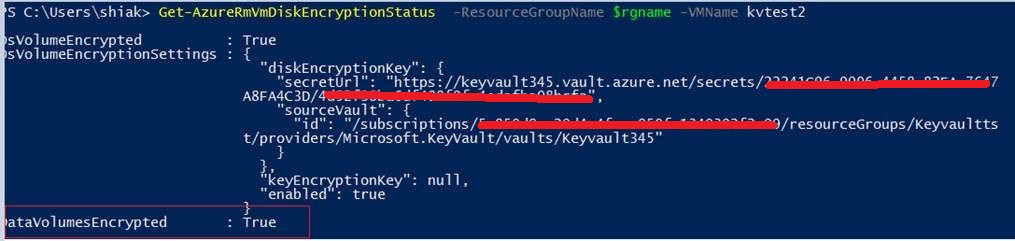
You will see OSVolumeEncrypted and DataVolumesEncrypted status as True if encryption is enabled
You can also check the status of disk encryption from within the VM using ‘manage-bde’ command and providing the drive letter as parameter. Sample output given below 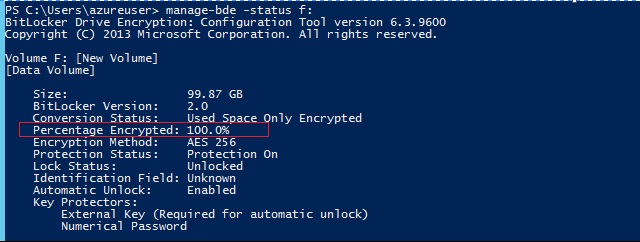
Also, it can been seen from the GUI of the server , the drives will have a lock signal associated
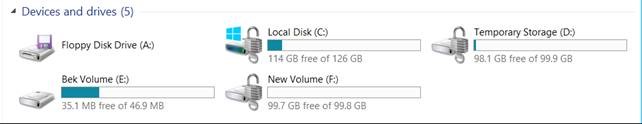
Now you know how to enable disk encryption for protection of data at rest in Azure!!!!
Ref: https://azure.microsoft.com/en-us/documentation/articles/best-practices-network-security/https://azure.microsoft.com/en-in/documentation/articles/azure-security-disk-encryption/