IT Infrastructure Threat Modeling Guide Released
The Solution Accelerators team is at it again, releasing the IT Infrastructure Threat Modeling Guide, which provides an easy-to-understand method for developing threat models that can help prioritize investments in IT infrastructure security. This guide describes and considers the extensive methodology that exists for Microsoft Security Development Lifecycle (SDL) threat modeling and uses it to establish a threat modeling process for IT infrastructure.
Included in the guide are the following:
Chapter 1: IT Infrastructure Components
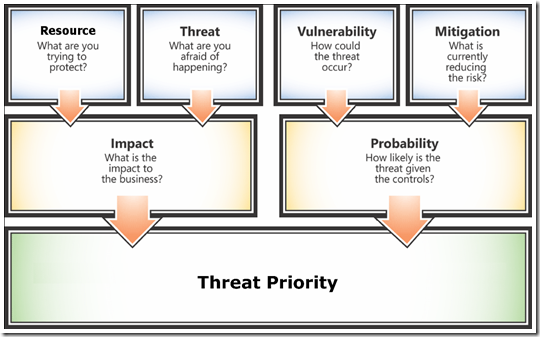
This chapter focuses on understanding the details of the components that the IT infrastructure threat modeling process will consider, including diagramming, identifying threats, mitigating threats, and validating all the information that is acquired during the process. The chapter discusses use scenarios, dependencies, implementation assumptions, entry points, and trust levels.
Chapter 2: The IT Infrastructure Threat Model Portfolio
This chapter describes how to populate the IT infrastructure threat model portfolio with relevant data about your components. The chapter includes information about prioritization and is essential for helping you mitigate threats with the greatest potential impact to your organization.
Chapter 3: Applied Example – The Threat Modeling Process
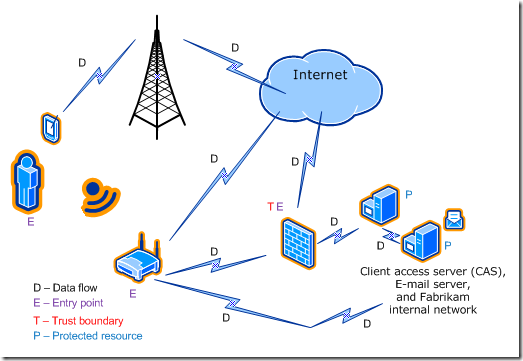
This chapter uses a fictitious organization's communications system as an example for the IT infrastructure threat modeling process. The rapid introduction of mobile devices into IT infrastructure could make such a system an ideal target for an attacker. You can use the SDL Threat Modeling Tool as described in this guide or another of your own choosing.
The threat modeling guide also discusses how you would use the Microsoft SDL Threat Modeling tool, and walks through some applied examples with our good friends at Fabrikam.
To download a copy of the IT Infrastructure Threat Modeling Guide, click here.
Related Resources
The following resources provide additional information about security topics and in-depth discussion of the concepts and security prescriptions in this guide:
- Security Risk Management Guide
- Microsoft Operations Framework
- Security Compliance Management Toolkit series
- Security Solution Accelerators
Comments
- Anonymous
January 10, 2012
The comment has been removed - Anonymous
June 18, 2013
The comment has been removed