How to change certificate on SSTP server - in Windows server 2008 R2
Hi Folks,
Very soon Windows 7 and Windows Server 2008 R2 will be released and it is very exciting that beta version of these new operating system is available for public download. So, go ahead and start using it and provide your valuable feedback to us.
In this blog I will talk about a new feature in RRAS for SSTP tunnel. In WS08, we added SSTP tunnel as a new VPN tunneling mechanism which allow enterprises to have the VPN available even though the user [remote access client] is behind the firewall or NAT device. This eases lot of deployment and support calls wherein the users were not able to connect to the enterprise due to firewall\NAT related issues.
Currently, SSTP by default picks up a certificate available in the cert store and do the SSL binding of the same and cache that information to do the crypto biding for inbound connection. This certificate selection by SSTP is not very intuitive for administrators, as administrator does not know which certificate is currently used by SSTP as there is no display available, also it does not provide a mechanism to the RRAS administrator to select specific certificate for the SSL binding by the SSTP. In case of mismatch between SSL binding and Crypto hash, SSTP will not function properly.
To enhance the deployment ease, we have provided UI and net shell interface to handle the certificate selection to the user, here is the new scenario\behavior.
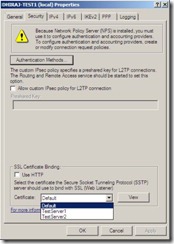
To be able to see the certificate selection UI, please do the following steps: Open the rrasmgmt.msc, select the targeted server and right click. Click on the properties option, this will open a tab based dialog box, select the Security Tab. In the Security tab, you will see the SSL certificate binding option at the bottom of the page as illustrated in pic 1. Administrator selects one of the provisioned certificates for SSL binding here on this page, Refer to the UI below. RRAS UI picks up and displays the valid certificates in the Certificate drop-down menu from Local M\c personal cert store. User can check currently provisioned certificate using certificate snap-in the WS08 R2. Once user selects\configures a certificate, UI will prompt for restarting the Remote access service (including SSTP service). SSL (SSTP service) binds to selected certificate once remote service is restarted. If remote access service is not running then binding will take place whenever remote access (SSTP service in particular) comes up.
Pic. 1 Certificate Selection UI
Note 1: In case of default certificate selection in the drop down menu, SSTP service will pick a certificate from the local computer personal store and do the binding.
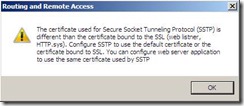
Note 2: In case if the currently SSL is bound to some certificate and that binding is done by some other application, UI will throw an error as illustrated in Pic 2. Administrator needs to correct this anomaly manually. Please see the netsh commands to see\delete\add the SSL binding in the netsh section below. There are 3 ways to fix it.
a) Let the other application also use the same certificate as used by SSTP
b) Choose the same certificate as used by the other application.
c) Choose default option in the drop down menu.
Pic 2: Error Dialog in case of certificate mismatch
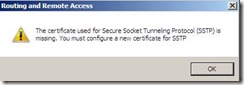
Note 3: In case when the selected certificate is deleted after the SSTP is configured by admin, when admin open the security tab, an error will be thrown stating that the certificate is missing as shown in Pic 3.
Pic 3: Error Dialog in case of certificate is deleted after configuring SSTP
With this UI, we also support configuration for SSTP in reverse proxy scenario. This can be done by having the check box “Use Http” checked. This configures SSTP to receive the plain HTTP packet as SSL is offloaded to proxy. In this case, user needs to manually configure the Certificate Hash in the registry manually, as done in Windows Server 2008
RAS administrator can also use net shell command to do the same thing (selecting the certificate). Behavior is same as described above.
· Each time remote access service is started SSL will bind to certificate configured (in RAS) if any. If certificate configured is not present in cert store then RRAS will cleanup the SSL cert binding. An ERROR event (Shown below) will also be logged in this case.
· SSTP service would continue to bind the certificate for both IPV4 & IPV6. This behaviour is same as LH. It is irrespective of whether administrator has selected the certificate or the certificate is chosen based on existing logic (SSTP logic of selecting certificate from store) or choosing the same certificate as current SSL binding (If SSL is already bound by some other web server applications).
While Configuring the certificate for SSL binding if the SSL binding already exist with some other cert by some application, UI\Netsh will inform the user about the mismatch so that user can select some other cert or remove the incorrect existing binding using the netsh command
Netsh Command to configure the cert for SSTP:
Netsh ras set sstp-ssl-cert name=<Cert Name>
OR
Netsh ras set sstp-ssl-cert hash=<Cert SHA-1 hash>
Netsh Command to see the current configured cert for SSTP:
netsh ras show sstp-ssl-cert
Netsh command to see and delete the current SSL binding:
netsh http show sslcert
netsh http delete sslcert ipport=<v4\v6 Address>:443
With Regards,
Dhiraj Gupta
Software Design Engineer
Windows Networking Group
Comments
Anonymous
January 01, 2003
Hello Friends, In my previous posting related to VPN tunnel selection , I discussed various scenariosAnonymous
March 10, 2009
Great article, thank you! Q: does SSTP support nultiple certificates (one per external hostname/IP address?