Cloud security - a multi faced approach : Part 2
Dear Readers,
We discussed about "Cloud security with IaaS deployments in Azure" in the earlier post, in this post, I'll dig deep into security aspects one should be aware about when it comes to Data layer in the Cloud.
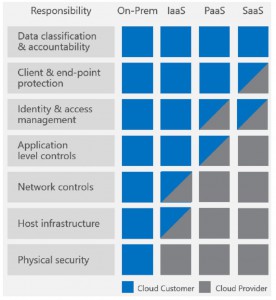
I’ll emphasize again the shared responsibility of customers along with the Cloud provider, when it comes to security. Below is a great diagram to understand –
Technological safeguards in Azure, such as Encrypted communications and operational processes, help keep your data secure. You also have the flexibility to implement additional encryption and manage your own keys.
In VMs, encryption can be looked at various layers :
- Data in transit : Azure uses industry-standard secure transport protocols such as SSL/TLS between user devices and Microsoft datacenters. You can enable encryption for traffic between your own virtual machines (VMs) and your users. With Azure Virtual Networks, you can use the industry-standard IPsec protocol to encrypt traffic between your corporate VPN gateway and Azure as well as between the VMs located on your Virtual Network. Refer SSL/TLS and IPsec if you are new to this.
- Data at rest. Azure offers a number of encryption options, such as support for AES-256, giving you the flexibility to choose the data storage scenario that best meets your needs.
Azure Disk Encryption lets you encrypt your Windows and Linux IaaS VM disks. Azure Disk Encryption leverages the industry standard BitLocker feature of Windows and the DM-Crypt feature of Linux to provide OS and data disk encryption to help protect and safeguard your data. It also can help you meet organizational security and compliance commitments. The solution is integrated with Azure Key Vault to help you control and manage the disk encryption keys and secrets in your key vault subscription, while ensuring that all data in the virtual machine disks are encrypted at rest in your Azure storage.
For Azure SQL database service too you can protect your data by encrypting your data when it is "at rest," or stored in database files and backups, using Transparent Data Encryption. There are other ways to encrypt your data secrets, you can consider:
- Cell-level encryptionto encrypt specific columns or even cells of data with different encryption keys.
- If you need a Hardware Security Module or central management of your encryption key hierarchy, consider using Azure Key Vault with SQL Server in an Azure VM.
- Very new capability in this space is called Always Encrypted (in preview) that makes encryption transparent to applications and allows clients to encrypt sensitive data inside client applications without sharing the encryption keys with SQL Database.
In a nutshell, there is enough & plenty of mechanism to protect & secure your data. Some of the configurations are done by default, while for others it’s a choice yours.
Take the first step to secure your data, encrypt where needed and have control of your cloud assets.
Hope this helps you start !
Cheers,
Pracheta