MS16-072 - Known Issue - Use PowerShell to Check GPOs
UPDATE - 30/06/2016
Official detect and fix script released. See here:
Powershell script to adjust permissions for Authenticated Users on Group Policy
Further information:
Deploying Group Policy Security Update MS16-072 \ KB3163622
Hello,
There is a known issue with the application of particular GPOs once MS16-072 is applied. Click the following link and browse to 'Known Issues' for more information:
MS16-072: Security update for Group Policy: June 14, 2016
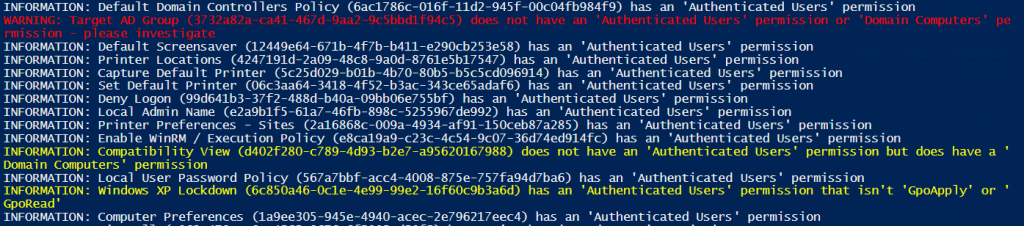
In response, I've put together the below PowerShell example to help identify GPOs, from the current domain, that might experience the issue once the update is applied. The output should be the basis for further investigation, i.e. it lists GPOs that may need the 'Authenticated Users' read permission or 'Domain Computers' read permission adding.
In the above image, a red 'WARNING:' message indicates a GPO that may experience the known issue.
There are also three types of 'INFORMATION' message*:
1) yellow - the GPO does not have an 'Authenticated Users' permission, but does contain a 'Domain Computers' permission
2) yellow - the GPO has an 'Authenticated Users' permission that is not 'GpoApply' (Read / Apply) or 'GpoRead' (Read)
3) white - the GPO has the expected 'Authenticated Users' permission.
*NB - all three 'INFORMATION:' messages can be commented out in the script to reduce the output to screen, although the first two may require further investigation
You should also take a look here:
New Group Policy Patch MS16-072– “Breaks” GP Processing Behavior
Cheers,
Mr P. Chap.
#Load GPO module
Import-Module GroupPolicy
#Get all GPOs in current domain
$GPOs = Get-GPO -All
#Check we have GPOs
if ($GPOs) {
#Loop through GPOs
foreach ($GPO in $GPOs) {
#Nullify $AuthUser & $DomComp
$AuthUser = $null
$DomComp = $null
#See if we have an Auth Users perm
$AuthUser = Get-GPPermissions -Guid $GPO.Id -TargetName "Authenticated Users" -TargetType Group -ErrorAction SilentlyContinue
#See if we have the 'Domain Computers perm
$DomComp = Get-GPPermissions -Guid $GPO.Id -TargetName "Domain Computers" -TargetType Group -ErrorAction SilentlyContinue
#Alert if we don't have an 'Authenticated Users' permission
if (-not $AuthUser) {
#Now check for 'Domain Computers' permission
if (-not $DomComp) {
Write-Host "WARNING: $($GPO.DisplayName) ($($GPO.Id)) does not have an 'Authenticated Users' permission or 'Domain Computers' permission - please investigate" -ForegroundColor Red
} #end of if (-not $DomComp)
else {
#COMMENT OUT THE BELOW LINE TO REDUCE OUTPUT!
Write-Host "INFORMATION: $($GPO.DisplayName) ($($GPO.Id)) does not have an 'Authenticated Users' permission but does have a 'Domain Computers' permission" -ForegroundColor Yellow
} #end of else (-not $DomComp)
} #end of if (-not $AuthUser)
elseif (($AuthUser.Permission -ne "GpoApply") -and ($AuthUser.Permission -ne "GpoRead")) {
#COMMENT OUT THE BELOW LINE TO REDUCE OUTPUT!
Write-Host "INFORMATION: $($GPO.DisplayName) ($($GPO.Id)) has an 'Authenticated Users' permission that isn't 'GpoApply' or 'GpoRead'" -ForegroundColor Yellow
} #end of elseif (($AuthUser.Permission -ne "GpoApply") -or ($AuthUser.Permission -ne "GpoRead"))
else {
#COMMENT OUT THE BELOW LINE TO REDUCE OUTPUT!
Write-Output "INFORMATION: $($GPO.DisplayName) ($($GPO.Id)) has an 'Authenticated Users' permission"
} #end of else (-not $AuthUser)
} #end of foreach ($GPO in $GPOs)
} #end of if ($GPOs)
Comments
- Anonymous
June 16, 2016
Thanks for the script, the Get-GPPermission should be Get-GPPermissions?- Anonymous
June 16, 2016
I have both in v5! :)
- Anonymous
- Anonymous
June 16, 2016
Cool script Ian. I like the check for custom permissions. I did an assess-fix script here: https://sdmsoftware.com/group-policy-blog/bugs/new-group-policy-patch-ms16-072-breaks-gp-processing-behavior/The one thing you may want to add, is a test to see if Domain Computers is in the ACL, since I believe that is sufficient to resolve this to? Also, because I think this only effects GPOs with per-user settings that use sec filtering, I test for that. Reduces the impact a bit.- Anonymous
June 16, 2016
Thanks, Darren.Have added the 'Domain Computers' test and linked back to your post :)
- Anonymous
- Anonymous
June 16, 2016
Get-GPPermissions is just an alias for Get-GPPermission :) - Anonymous
June 16, 2016
This is amazing. Thank you for posting this. - Anonymous
June 16, 2016
If using Security Filtering, we are supposed to add Read permissions Domain Computers for the GPO. This script doesn't check for that from what I see.- Anonymous
June 16, 2016
Check added
- Anonymous
- Anonymous
June 16, 2016
How do I view the output?- Anonymous
June 16, 2016
Hey, Anthony - new version will now provide output for non-conflict policies, too.- Anonymous
June 16, 2016
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
June 16, 2016
Sorry I'm a bit of a noob when it comes to this. I do not have any output when I do this powershell. Is it only supposed to return results IF there is one that might conflict and if not, then it will just go back to my regular prompt?- Anonymous
June 16, 2016
Correct, Nickolas.New version will now provide output for non-conflict policies, too.- Anonymous
June 19, 2016
Hey Ian, Thank you very much for the response and thank you very much again for making this script. This has helped me and my teammates tremendously!!
- Anonymous
- Anonymous
- Anonymous
June 16, 2016
good stuff as alwaysThanks - Anonymous
June 16, 2016
Converted to a function with object output so you can easily export to csv:Function Test-GPOAuthenticatedUsers{ #Load GPO module Import-Module GroupPolicy #Get all GPOs in current domain $GPOs = Get-GPO -All #Check we have GPOs if ($GPOs) { #Loop through GPOs foreach ($GPO in $GPOs) { #Nullify $AuthUser $AuthUser = $null #See if we have an Auth Users perm $AuthUser = Get-GPPermissions -Guid $GPO.Id -TargetName “Authenticated Users” -TargetType Group -ErrorAction SilentlyContinue #Alert if we don’t have an ‘Authenticated Users’ permission if (-not $AuthUser) { $status = 'Missing Authenticated Users Permission' } #end of if (-not $AuthUser) else { #Alert on a custom permission if ($AuthUser.Permission -eq “GpoCustom”) { $Status = 'Custom Authenticated Users Permission' } #end of if (-not $AuthUser) else{ $Status = $true } } #end of if (-not $AuthUser) [pscustomobject]@{'DisplayName'=$GPO.DisplayName;'ID'=$GPO.ID;'Status'=$status} } #end of foreach ($GPO in $GPOs) } #end of if ($GPOs)}Test-GPOAuthenticatedUsers | Export-Csv -path c:\temp\gpoauthusersissues.csv -NoTypeInformation - Anonymous
June 16, 2016
Most of our GPOs are linked to an OU where the computer objects reside. I think this is the case, but just to be clear..."domain computers" isn't actually necessary if we have an "exception" GPO that overrides another, but only applies to a subset of machines (which are in turn added to security group), correct? It is just necessary that the computer object that needs the access, is able to read. Also, do you need to set the Read permission on the Security Filtering section, or can you just do it on the Delegation tab and only set Read (or...does it require Read+ApplyGPO)?- Anonymous
June 17, 2016
Have added Domain Computers were no authenticated users also missing on the delegation tab of each GPO for read. But your script still shows me all GPOs in red stating out both are missing.
- Anonymous
- Anonymous
June 17, 2016
Is there a way to allow this script to work for older SBS2008 servers? The Import-Module GroupPolicy is not valid in these installs. - Anonymous
June 17, 2016
Has anyone created a script that will produce this report but also allow you the option to repair? We have a bunch of clients we're going to have to run this on - it would be nice to have a simple solution, once we "approve it" to have it repaired vs. having us automatically fix each one by hand. - Anonymous
June 17, 2016
The comment has been removed - Anonymous
June 17, 2016
The comment has been removed - Anonymous
June 17, 2016
couple things on this. any way to specify a domain? i have 32 domains i manage. if you log in with an account from domain x on to domain y, the script will take your logon domain. can we specify a domain controller? since i have 100's of dc's, i'm waiting for replication. i tested this on a domain with 2 dc's. made the change on one dc, and the script still didn't show. i check the other dc, and replication didn't go through yet. i'd like to be able to pinpoint 1 dc so that when i make updates, it will report back from that dc, not some other random dc. sorry I'm definitely learning powershell but by no means can write it. this is a bit above my powershell level. - Anonymous
June 20, 2016
When a script will be available via the KB homepage, it would be helpful if it can handle a multi-domain forest as well, e. g. by providing a domain parameter.Nevertheless, thanks for the script. - Anonymous
June 20, 2016
It sounds like the security change in the MS16-072 patch will affect GPOs with User Settings only, is that right? If I'm understanding this correctly, we have some GPOs that contain only Computer Settings and won't need to touch those... Can anyone confirm? Thanks - Anonymous
June 21, 2016
Nice script Ian. I've taken your ideas and Darren's script and rolled them into one big assessment and remediation script here: http://www.jhouseconsulting.com/2016/06/22/script-to-report-on-and-remediate-the-group-policy-security-change-in-ms16-072-1627Cheers,Jeremy- Anonymous
June 22, 2016
Thanks for this!!
- Anonymous
- Anonymous
June 22, 2016
May I suggest adding the following to your script for those of us who are not using English ('Authenticated User' is 'Utilisateurs Authentifiés' in French). So Why not use the SID of groups instead :# Get 'Authenticated Users' group name from SID$AuthUserSID = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-11") $AuthUserName = ($AuthUserSID.Translate( [System.Security.Principal.NTAccount])).value# Get 'Domain Computers' group name from SID$DomCompSID = New-Object System.Security.Principal.SecurityIdentifier("$(((get-addomain).DomainSID).value)-515") $DomCompName = ($DomCompSID.Translate( [System.Security.Principal.NTAccount])).valueAfter that you'll have to fix ever -TargetName 'Authenticated Users' and -TargetName 'Domain Computers' to use the new variables :-TargetName $AuthUserName-TargetName $DomCompNameThanks for the script, saved me lot of time.- Anonymous
June 26, 2016
Great suggestion from Jean-Pierre Paradis. I added this to my script: http://www.jhouseconsulting.com/2016/06/22/script-to-report-on-and-remediate-the-group-policy-security-change-in-ms16-072-1627Cheers,Jeremy
- Anonymous
- Anonymous
June 23, 2016
Nice script. thnx! - Anonymous
June 23, 2016
Maybe I did something wrong, but when I run this script I get errors:At D:\desktop\gpcheck.ps1:20 char:166+ ... omputers’ permission – please investigate†-ForegroundColor Red+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~The string is missing the terminator: ".At D:\desktop\gpcheck.ps1:19 char:20+ if (-not $DomComp) {+ ~Missing closing '}' in statement block or type definition.At D:\desktop\gpcheck.ps1:17 char:21+ if (-not $AuthUser) {+ ~Missing closing '}' in statement block or type definition.At D:\desktop\gpcheck.ps1:8 char:25+ foreach ($GPO in $GPOs) {+ ~Missing closing '}' in statement block or type definition.At D:\desktop\gpcheck.ps1:6 char:12+ if ($GPOs) {+ ~Missing closing '}' in statement block or type definition. + CategoryInfo : ParserError: (:) [], ParseException + FullyQualifiedErrorId : TerminatorExpectedAtEndOfString- Anonymous
June 29, 2016
Check the quotation marks....I had the same problem....had to convert the quotation marks in the script to standard 'single' and "double" quotes for it to work.
- Anonymous
- Anonymous
June 24, 2016
I know this is fir the script but I do have a question about the solution, So am I understanding correctly that it is no longer possible to use Security Filtering by user groups? I have several policies that span multiple OUs and use Security filtering to pick out users by security group. Mainly these are for users that work in multiple departments. - Anonymous
June 29, 2016
I just published a script to modify the defaultSecurityDescriptor attribute on the Group-Policy-Container schema class object: http://www.jhouseconsulting.com/2016/06/29/script-to-modify-the-defaultsecuritydescriptor-attribute-on-the-group-policy-container-schema-class-object-1668Hope people find that helpful.Cheers,Jeremy - Anonymous
August 05, 2016
Thanks for sharing the script. - Anonymous
August 08, 2016
Great - Anonymous
September 21, 2016
I am having some issues to apply a GPO to a nested group structure using Security Filtering. I wonder whether that's also caused by the same update. This is the scenario:AD Users: 1, 2, 3AD Groups: A, B, CGroup C is a member of Group BGroup B is a member of Group AGPO filtered to Group AUser1: Member of group A - GPO applies successfullyUser2: Member of group B - GPO doesn't apply (access is denied)User3: Member of group C - GPO doesn't apply (access is denied)GPModeling tells me that all the 3 users - Anonymous
October 19, 2016
You can one-liner this and return an object instead of text, makes it easier to filter later on...Get-GPO -All | Select *,@{n='AuthUser';e={[bool](Get-GPPermissions -Guid $.Id -TargetName "Authenticated Users" -TargetType Group -ErrorAction SilentlyContinue)}},@{n='DomainComputers';e={[bool](Get-GPPermissions -Guid $.Id -TargetName "Domain Computers" -TargetType Group -ErrorAction SilentlyContinue)}}