Renew Web Server (SSL) Certificates Automatically
Working with Internet Information Services (IIS) certificates can be a bit challenging especially during renewal time. Most organizations do not track Web SSL certificates which in turn might expire and cause an unplanned outage. Those who track this information on the other hand, have to make sure certificate are renewed before their expiration period or find ways to notify the application owners of their certification expiration beforehand.
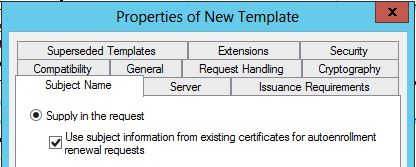
Windows Server 2008 R2 and Windows Server 2012 addresses this issue through Auto-enrollment and Certificate Templates. The Certificate Template’s design includes a new option Use subject information from existing certificates for autorenewal requests. This option allows the certificate to renew automatically, including any information in the Subject Name, or any additional information in Subject Alternate Names fields. This option is available for client certificates installed on computers running Windows 7 or Windows Server 2008 R2 and later.
The Use subject information from existing certificates for autoenrollment renewal requests option causes the certificate enrollment client to read subject name and subject alternative name information from an existing computer certificate based on the same
certificate template when creating renewal requests automatically or using the Certificates snap-in. This applies to computer certificates that are expired, revoked, or within their renewal period.
The Autoenrollment Group Policy has to be enabled for this feature to work. This feature will also work on certificates issued prior to enabling it. For example, an administrator can change the original template’s settings to include Use subject information from existing certificates for autoenrollment renewal updates after a certificate is issued because the scope of enrollment in a Microsoft PKI is the template. Autoenrollment Group Policy and this feature will allow the certificate to renew in the future without any administrative intervention when the certificate is within the renewal validity period time specified by the template – typically within 20% or less of the certificate’s validity period.
Amer F Kamal
Senior Premier Field Engineer
Comments
Anonymous
January 01, 2003
The comment has been removed- Anonymous
February 01, 2017
But no option for Server 2008 R2 / IIS 7.5 - only 2012 R2?
- Anonymous
Anonymous
January 01, 2003
Amer Kamal offers a solution to a long-standing request for auto-renewing IIS web server certificatesAnonymous
January 01, 2003
Yes I concur the process is flawed, it does successfully renew the certificate but as the digital fingerprint of the cert is renewed this has to be manually bound to the website its used on using the IIS management console. Has anyone got any bright ideas that might automate that final step?Anonymous
August 27, 2013
Hi Amer, thank you for your post but how does IIS pickup the new certificate for use? The other thing I want mention is, when you assign a new certificate to the website existing sessions will be disconnected and users might have to re-authenticate depending on your hosting scenario. And with auto-enrollment you can't define a maintenance Windows or predict the certificate renewal happens at a certain time window. How do you solve issues with certificate renewal in a web server farm using auto-enrollment? Might you can expand your blog post to address those questions. Regards, LutzAnonymous
October 10, 2013
Hello Ricardo, I see your comment but no link to Amer's solution to Lutz's question. Can you repost? Thanks, BillAnonymous
November 18, 2013
although the certificate can be renewal automatically, the un-planned downtime will also exist. Don't forget your IIS will not offer an “auto re-binding correct certificate” feature. After certificate expired, you will see a 501 error.Anonymous
April 04, 2014
http://www.iis.net/learn/get-started/whats-new-in-iis-85/certificate-rebind-in-iis85Anonymous
April 28, 2014
Hello All, This is Wes Hammond with Premier Field Engineering back with follow up to a previous blogAnonymous
June 18, 2014
server renewAnonymous
June 26, 2014
How I open this option i dont know please help if anyone there.Anonymous
January 10, 2015
Gr8
Will this work With he CEP/CES service as well? Or will it only work when the server har RPC Connection to the CA?Anonymous
March 24, 2015
The auto rebind can also be performed via automation engines like Orchestrator. Almost everything can be administratively executed using PowerShell. With the script on hand, you can copy and paste them into Orchestrator to automate the task post trigger. The trigger would come from a Monitoring System looking for 20%- expiring certificate notice in event logs (event: CertificateServicesClient-Lifecycle-System and CertificateServicesClient-Lifecycle-User ). Once these events are detected, Orchestrator would receive a notice to start the binding process once the AD CS completed the certificate renewal.- Anonymous
August 30, 2016
Hi,Does the auto-renewal based on existing Cert "require" that the Autoenroll permission on CertTemplate is set as well?
- Anonymous
Anonymous
May 27, 2016
It works perfectly! Thank you very much. Great article!Anonymous
November 21, 2016
So how do I configure the Access Control Entries (securely) if I want to use this feature?If I initially manually enroll a certificate like this for a server (as a user that has been delegated permissions) with the correct Subject / SAN's configured, can I allow, say, Domain Computers -> Autoenroll on the template and they will only be able to renew existing certificates and not enroll arbitrary new ones?So the combination of "Supply in the request" + "Autoenroll" for a computer account will not allow the computer account to request NEW certificates with arbitrary Subjects/SANs? That would be massively insecure, especially if you're not using issuance requirements.If so, that is kind of confusing, you would think there would be a "Renew existing" ACE for this.Anonymous
January 02, 2018
The comment has been removed