Cloud Identity Overview - Part 2 (Authorisation)
Part 2 - Authorisation
Authentication is the process to validate that an individual is who they say they are. Authorisation extends this to determine what are they allowed to access given what we know about the user at that point. As we move into an era of working anywhere, on any device at any time, authorisation becomes very important to safeguard corporate assets as we need to factor in where, on what and when the user is trying to access data.
Microsoft has extensive capability in this space so here are the options I see customers using with Microsoft Cloud Services.
- Multi Factor Authentication (MFA) - While technically this should be in the authentication discussion I have placed it here as MFA is commonly enforced as a result of an authorisation evaluation. Azure MFA enables you to enforce strong authentication (phone, pin, application) in a variety of scenarios. You could, if you wanted to enable it for all users all of the time (strongly advised for administrator accounts) or you could just enforce when needed (step up authentication). i.e. you detect a user is outside of the network, on a non-managed device and many other scenarios.
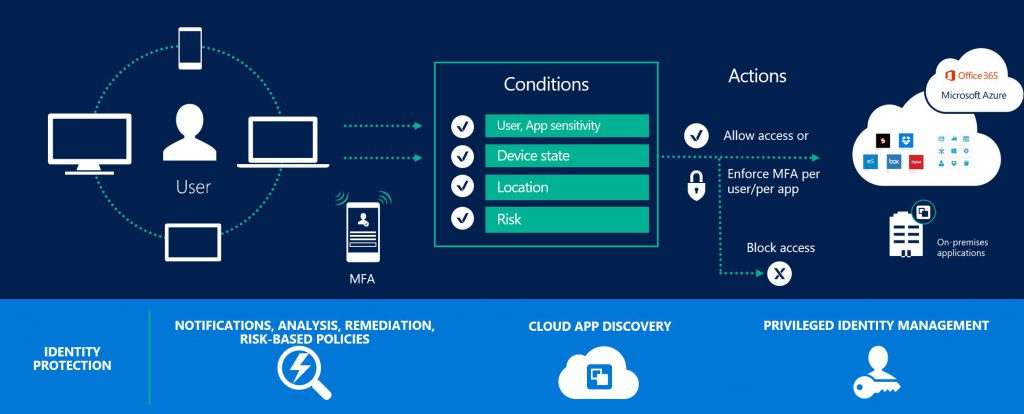
- Azure Conditional Access - This functionality is included with Azure AD Premium and is extensively used by enterprises. Azure Conditional Access works by providing you the ability to allow\deny access or potentially step up authentication based on the following parameters
- Group membership - Allow users to access a resource if they are a member of a group.
- Location - Allow, Deny users based on the location from which they are trying to access resources.
- Device Platform - Allow or Deny users to access a resource based on the OS of the device they are trying to access from.
- Device State - The ability to enable\disable a device and include the state of the device in the authorisation decision. i.e. require that users accessing Exchange from a browser on an unknown device perform MFA.
- Sign-in and user risk - Advanced protection to determine the risk of the access request. I.e. user is attempting to logon from USA and had previously logged on from UK 5 mins earlier (Available with Azure Identity Protection).
- Enterprise Mobility Suite (EMS) - builds upon the capabilities provided by Azure Conditional Access to bring more device based intelligence into the authorisation decision. With EMS you can start to define conditional access policies that enforce that the device is of a certain type or configuration, application level intelligence, domain joined, under management of Intune amongst many other options.
- AD FS Client Access Policies - As with Azure Conditional Access, AD FS also provides the ability to allow\deny access or potentially step up authentication based on certain parameters. This is called AD FS client access policies and prior to the release of Azure Conditional Access was heavily used by customers.
So what's the best authorisation option for my organisation?
Again this is something that really depends on your requirements as an organisation, but a common thread I see amongst customers is the use of MFA. As a rule I haven't met a customer yet who hasn’t thought that enabling "step up" authentication when users are trying to access cloud resources from outside of the corporate network or on a non-managed device is a good idea. From that as a baseline it's down to your organisational requirements to determine how much more evaluation of device, location etc you wish to bring into the authorisation flow.
See you in Part 3 - Synchronisation
MD