Operations Management Suite (OMS) Adds Security Analytics to Power Threat Detection
SUMMARY: OMS adds Security Analytics to Power Threat Detection for the Security and Audit solution
The OMS Security and Audit solution includes many tools to secure your organization and detect threats. It has access to all of this security data across your environment, provides insight into your security posture, and correlates data with threat intelligence. But to stay ahead of rapidly evolving threats, we have to make use of advanced analytics, and techniques like behavioral analysis. Today, we introduce the preview of a new and powerful tool to detect threats in your datacenter. The advanced detection analytics is examining the security events and look for patterns that indicate a threat.
We began rolling out these new detections, powered by security analytics, to workspaces in the United States (EUS region). Over time, this will be expanded to more regions. The first release includes virtual machine behavioral analytics for Windows machines, which enable detection of suspicious processes on Windows virtual machines, attempts to move laterally within the environment and more.
Traditional tools that analyze security events are based on a fixed set of detections that are either updated manually or only when a new version is deployed. Not only the advanced detection analytics includes built-in security detection logic, it is unlocking the full power of the cloud by updating this logic constantly. Every time our security researchers find a new attack pattern, we will update the analytics. Your data is always evaluated using a fresh set of security detections.
A constantly updated list of detections will be presented on the main security dashboard right next to the notable issues. This list will also contain threats detected by the OMS Security solution as well as other Microsoft security solutions, such as Microsoft Advanced Threat Analytics (ATA) in instances where the OMS agent is running on the ATA Center machines. 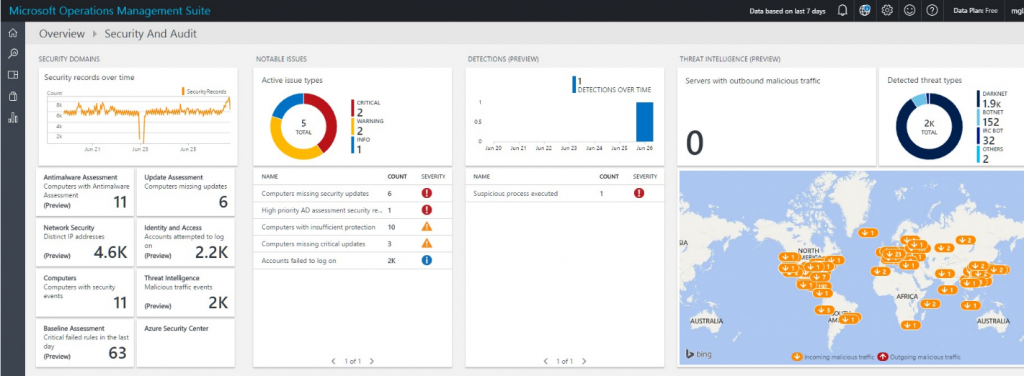
The detections are also available in search as a new object type named SecurityDetection. This object appears here: 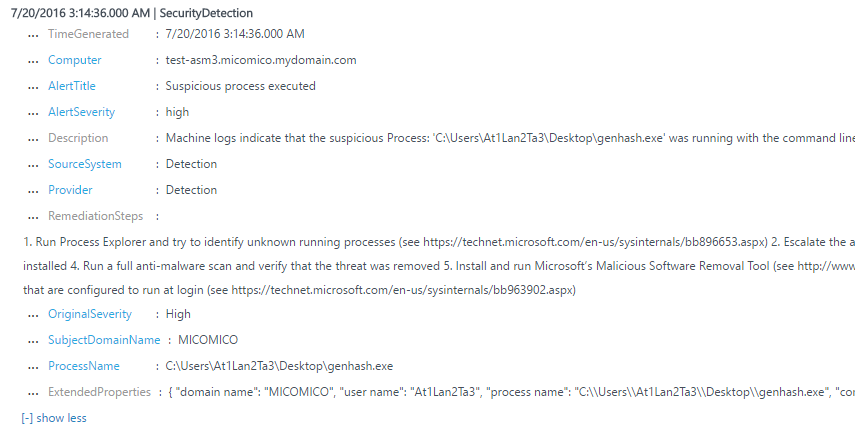
You can define alerts on the SecurityDetection type to get e-mail or text message according to your own preferences. For example, you can use the following query to create an alert that would send e-mail when high or medium severity detections are found: Type=SecurityDetection (AlertSeverity=High or AlertSeverity=Medium)
Example Detection Scenarios
The advanced detection is analyzing many patterns that might indicate a threat. The full list of detections is not disclosed to protect our customers. If the full list is revealed, attackers would have easier time finding techniques to avoid it. Below are two examples for detections that are being evaluated. These examples could also be used by you to test OMS Security advance detections on your environment.
Executable with double extension
One technique that is used by attackers is to trick administrators to run their tools without intend. This is done by disguising the malicious executables as an innocent document. For example, naming it troubleshoot.PDF.exe. Since every execution is logged in security event 4688, the detection analytics can scan all of these records and look for such patterns.
Irregular SVCHost.exe execution
Once attackers manage to run their malicious code, there are various techniques that they are using to make these executables less noticeable on the compromised machines. Many attackers try to give their malicious executables the same name as operating system executable. It is very common to see them using SVCHost.exe which is used to execute Windows services. In most cases, attackers cannot run these files from the Windows System32 folder like a regular SVCHost.exe. The detection analytics is using this to find records of SVCHost.exe execution from different folders.
Architecture
The following diagram illustrate how the advanced detection is integrated into OMS: 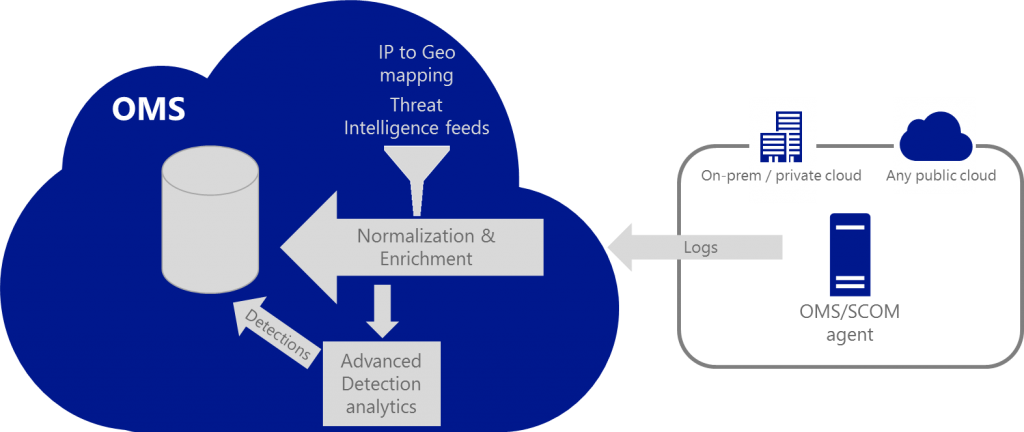
How to improve your detections
While the advanced detection analysis is working for everybody with no prerequisites or configuration, it is recommended to set two policies on your servers to make sure that all data is available:
1. Log command line parameter for executed process – See instructions under “Process Command Line” here.
2. Enable AppLocker at least in audit-only mode. More details here.
What’s Next
Our team keeps on adding new detections all the time. Microsoft has hundreds of security researchers that defends our own resources and our customers. We will constantly use their insights to extend our detection capabilities. This includes the following initiatives:
· Threat intelligence monitoring: Threat intelligence includes mechanisms, indicators, implications and actionable advice about existing or emerging threats. This information is shared in the security community and Microsoft continuously monitors threat intelligence feeds from internal and external sources.
· Signal sharing: Insights from security teams across Microsoft’s broad portfolio of cloud and on-premises services, servers, and client endpoint devices are shared and analyzed.
· Microsoft security specialists: Ongoing engagement with teams across Microsoft that work in specialized security fields, like forensics and web attack detection.
· Detection tuning: Algorithms are run against real customer data sets and security researchers work with customers to validate the results. True and false positives are used to refine machine learning algorithms.
These combined efforts culminate in new and improved detections, which you can benefit from instantly – there’s no action for you to take.
On top of that, we are looking to extend the advanced detections in OMS as follows:
- Support detections on all OMS regions
- Fuse multiple detections that align with kill chain patterns into a single incident so you can quickly understand what actions the attacker took and what resources were impacted
- Apply security analytics to other types of data, including network data, to detect network based attacks
- Add security analytics for Linux machines
- Integrate detections from other security products/services
Learn more
Make sure to visit OMS Security documentation page to learn more about OMS Security capabilities:
- Getting started with Operations Management Suite Security and Audit Solution
- Monitoring Resources in Operations Management Suite Security and Audit Solution
- Monitoring and Responding to Security Alerts in Operations Management Suite Security and Audit Solution
I invite you to follow the Microsoft OMS Facebook site. If you want to learn more about Windows PowerShell, visit the Hey, Scripting Guy Blog.
If you would like to get a free Microsoft Operations Management Suite (#MSOMS) subscription so that you can test it out, you can do so from here. You can also get a free subscription for Microsoft Azure as well by selecting this link.
Microsoft Operations Management Team
Comments
- Anonymous
August 02, 2016
Great post ! Security analytics is getting more important then ever before. - Anonymous
August 03, 2016
How does this capability compare to Security Center?- Anonymous
August 10, 2016
Hi Mark, this is exactly the same detection engine that is used in Azure Security Center. In OMS, you can also get the same detection capabilities for hybrid environments supporting on-prem servers and other clouds.
- Anonymous