Add your Cisco ASA logs to OMS Security
Summary: Forward your Cisco ASA logs to OMS via the Linux agent, and use OMS to analyze the logs.
Hello, this is Meir Mendelovich from the OMS team, and today I want to talk about forwarding your Cisco ASA logs to OMS via the Linux agent.
OMS Security and Audit solution provides security insights about many sources of data from Windows and Linux machines. You can add any source that emits Syslog to OMS, but today we announce a new capability to parse Cisco Adaptive Security Appliance (ASA) logs and integrate them into OMS Security and Audit solution.
After you forward your Cisco ASA logs to OMS via the Linux agent, OMS would not just index the log string but also parse most of the messages that are related to security. This makes it easy to search the data and use it in queries, alerts, and dashboards.
Other than parsing it, the logs are also searched to find IP addresses that, according to our threat intelligence feeds, are used by malicious actors. This will provide a good insight for attack attempts (denied) and successful attacks (access granted) on your systems. Even more important, it highlights cases where servers within your datacenter are contacting malicious computers on the Internet. This usually indicates a malware that contacts its command and control or data infiltration. In the future, we would also geo-tag these IP addresses so that they can be presented on maps.
You can read the instructions about how to configure the Cisco ASA integration. The following diagram has an overview of the Cisco ASA log processing architecture:
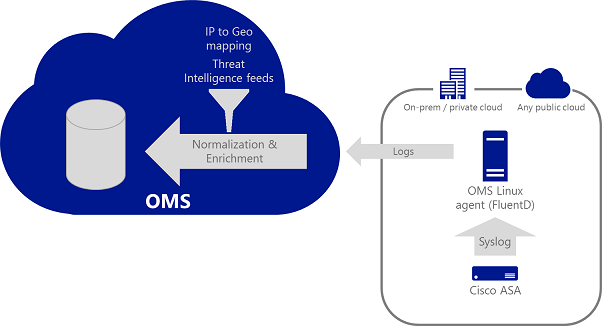
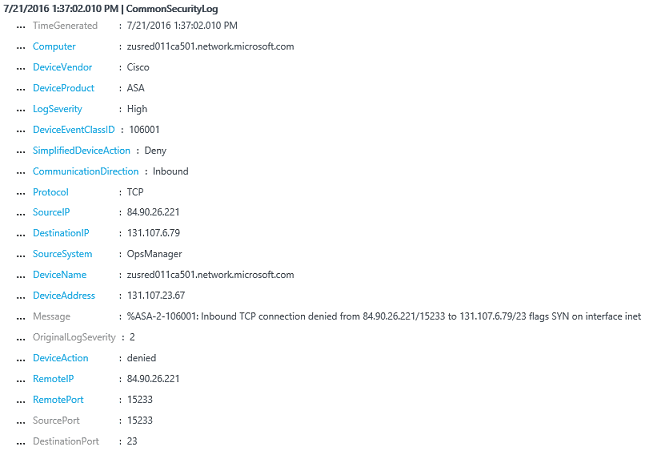
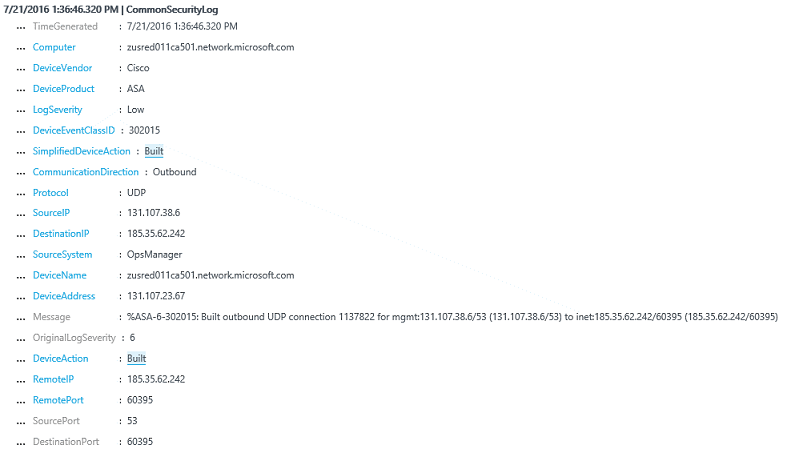
The end-result is a new type of log called CommonSecurityLog. In the future, more security log sources will be normalized for this type. Following is an example of these records in the search result:
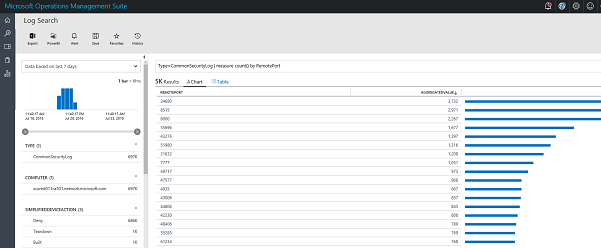
You can use the full power of the OMS search language to analyze the data:
Meir Mendelovich
Microsoft Operations Management Team
Comments
- Anonymous
December 13, 2016
Will the same method be available soon for WSA logs.