August 2016 Updates
Hello again! It's been a while since our last update. Many of you have provided excellent feedback and feature requests. We have been very busy incorporating them. We have also added Key Vault in more regions and integrated with more services. Here's a quick summary of updates in last few months, details follow.
- Key Vault is now available in more regions - India (Central India, South India, West India)*, Canada (Canada Central, Canada East), US (West Central US, West US 2)
- Key Vault logs are now available in Azure China. We are still working to enable Key Vault logs for Azure Government and Azure Germany. Stay tuned.
- Now you can grant permissions to access key vault to a security group - See details below.
- Analyze and visualize your key vault usage with OMS Log Analytics (Preview) - see details below
- Key Vault now supports native clients - see details below
- Azure Disk Encryption, SQL Connector are now generally available - see details below
- Distribute certificates stored in Key Vault to Service Fabric clusters and App Services Web Apps - see details below
- Cloud Service Providers can now manage Key Vaults for their customers - details to follow in coming weeks.
- Compliance: Key Vault now complies with FedRAMP (US Federal Risk and Authorization Management Program) and PCI-DSS (Payment Card Idustry - Data Security Standard) - see details below
* The India regions are available to volume licensing customers and partners with a local enrollment in India. The India regions will open to direct online Azure subscriptions in 2016.
And that's not all! In coming weeks and months we'll be adding more features, including preview of one of the most often requested features that will be announced next month.
As usual, we value your input so please take a moment to join our advisory board, send us private feedback,and/or visit our forum .
Details
Now you can grant permissions to access key vault to a security group: Key Vault stores sensitive information and hence you want to tightly control who gets access to it. To that end originally we limited key vault access policies to only 16 entries. But we encountered a few usage scenarios where you may need to grant access to a large group of users to manage a key vault. With support for security groups, you can create a security group in Azure Active Directory and then grant permissions to this group to access key vault. For example, say you had a group named 'group2' in Azure Active Directory that consisted of several users, and you want to grant access to these users to manage keys and secrets, here's how you would use the Set-AzureRmKeyVaultAccessPolicy command to grant permissions:
Set-AzureRmKeyVaultAccessPolicy -VaultName 'myownvault' -ObjectId (Get-AzureRmADGroup -SearchString 'group2')[0].Id -PermissionsToKeys All -PermissionsToSecrets All
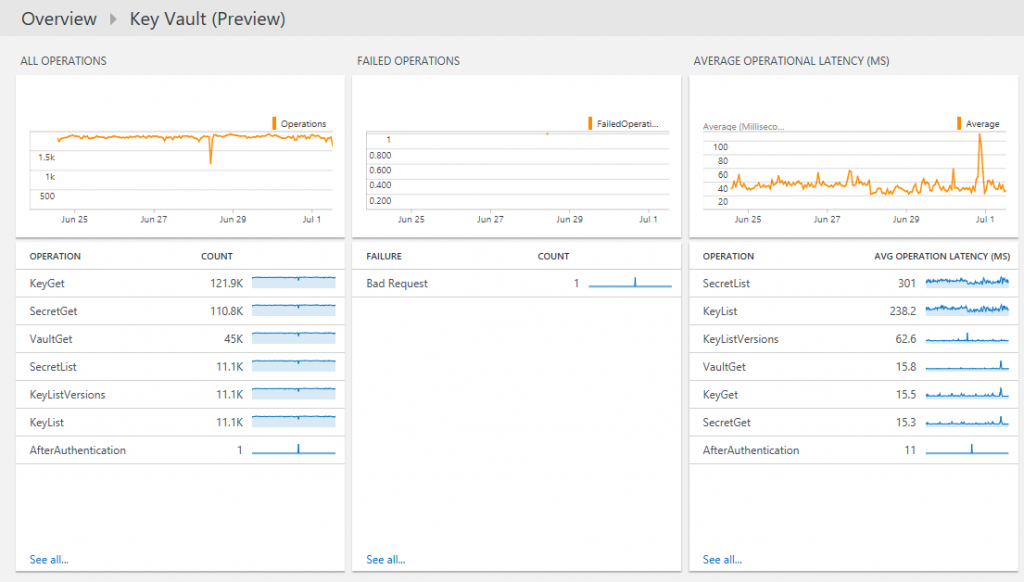
Analyze and visualize your key vault usage with OMS Log Analytics (Preview): You can now pipe Key Vault logs into OMS (Operations Management System) Log Analytics tool and view your logs in a nice dashboard that gives you quick overview of all key vault operations. OMS Log Analytics is a sophisticated tool that allows you to slice and dice your logs, including key vault logs to analyze response times, failures, access trends and so on. You can also set alerts to receive notifications when a particular criteria is met. Follow the step-by-step instructions to get log analytics setup for key vault logs. Here's how a typical dashboard looks like.
This view shows three dashboard tiles: a summary of frequency of all operations, a query showing failed operations and the last one shows average latency for all operations. You can drill down by selecting the tile and modifying the query to diagnose problems quickly. OMS Log Analytics also allows you to set alerts to get notified when specific events happen.
Key Vault now supports native clients: Say you want to develop your own client application so that users can use their own credentials and access key vault. Azure PowerShell and Azure Cross-platform Command Line Interface are examples of such native clients, but they worked without this feature, as they were well known apps that were grandfathered in. Now you can write your own native client applications to access Key Vault. Native client application needs to be configured differently from the web apps or headless worker role etc. our next blog will explain more about configuring and using native client with key vault. Stay tuned.
Azure Disk Encryption, SQL Connector are now generally available - Azure Disk Encryption for Windows is generally available since May, and disk encryption for Linux will be generally available soon. Azure Disk Encryption uses Key Vault to store the encryption keys. SQL Connector has also reached general availability. With SQL Connector, you can use Azure Key Vault to store master key for transparent data encryption in your SQL Server.
Distribute certificates stored in Key Vault to Service Fabric clusters and App Services Web Apps - Now you can distribute certificates store in Key Vault to Service Fabric clusters. This uses the same mechanism that we have already blogged about which is also documented here. And as part of App Service Certificate (ASC) offering you can now deploy certificates stored in Key Vault into your Web Services Web App. Last month Azure App Services also announced a new feature that enables users to buy (from GoDaddy) and configure an SSL certificate for your Azure App Service. This certificate is stored in Key Vault as a secret and can be distributed to any app (not just App Services app) when it is deployed.
Compliance: Key Vault now complies with FedRAMP (US Federal Risk and Authorization Management Program) and PCI-DSS (Payment Card Idustry - Data Security Standard). This is in addition to ISO/IEC 27001, CJIS (Criminal Justice Information Services), CSA CCM (Cloud Control Alliance Cloud Controls Matrix), ENISA IAF (European Network and Information Security Agency Information Assurance Framework), EU Model Clauses, FACT (Federation Against Copyright Theft), HIPAA (Health Insurance Portability and Accountability Act), IRS 1075 (Internal Revenue Services Publication 1075), ISO/IEC 27017, ISO/IEC 27018, and ITAR (International Traffic in Arms Regulations) for Azure Government, which Key Vault already complies with.