Support for SSL/TLS protocols on Windows
***********Updated on 4th October 2017***********
NOTE: Support for TLS 1.1 and TLS 1.2 is now available in Windows Server 2008 SP2. Install the following update: Update to add support for TLS 1.1 and TLS 1.2 in Windows Server 2008 SP2 |
Secure Socket Layer (SSL) and its successor Transport Layer Security (TLS) are protocols which use cryptographic algorithms to secure the communication between 2 entities. It is just a secure layer running on top of HTTP.
| ||||||||||||||||
Overview of SSL Protocol Stack
Several versions of SSL have been released after its advent in 1995 (SSL 2.0 by Netscape communications, SSL 1.0 was never released). Here is the list:
- SSL 1.0, 2.0 and 3.0
- TLS 1.0 (or SSL 3.1, released in 1999)
- TLS 1.1 (or SSL 3.2, released in 2006)
- TLS 1.2 (or SSL 3. 3, released in 2008)
SSL was changed to TLS when it was handed over to IETF for standardizing the security protocol layer in 1999. After making few changes to SSL 3.0, IETF released TLS 1.0. TLS 1.0 is being used by several web servers and browsers till date. What I have never understood, is there have been newer versions released after this, with the latest being TLS 1.2 released in 2008.
On Windows the support for SSL/TLS protocols is tied to the SCHANNEL component. So, if a specific OS version doesn’t support a SSL/TLS version, this means it remains unsupported.
All the windows components/applications abide by this rule and can support only those protocols which are supported at the OS level. For e.g.: IIS and Internet Explorer. |
Below table should give you a good understanding of what protocols are supported on Windows OS.
| Windows OS Version | SSL 2.0 | SSL 3.0 | TLS 1.0 | TLS 1.1 | TLS 1.2 |
|---|---|---|---|---|---|
| Windows XP & Windows Server 2003 | ✓ | ✓ | ✓ | X | X |
| Windows Vista & Windows Server 2008 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Windows 7 & Windows Server 2008 R2 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Windows 8 & Windows Server 2012 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Windows 8.1 & Windows Server 2012 R2 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Windows 10 & Windows Server 2016 | ✓ | ✓ | ✓ | ✓ | ✓ |
TLS 1.1 & TLS 1.2 are enabled by default on post Windows 8.1 releases. Prior to that they were disabled by default. So the administrators have to enable the settings manually via the registry. Refer this article on how to enable this protocols via registry: https://support.Microsoft.com/en-us/kb/187498
On the client side, you can check this in the browser settings. If you are using IE on any of the supported Windows OS listed above, then in IE, browse to Tools -> Internet Options -> Advanced. Under the Security section, you would see the list of SSL protocols supported by IE. IE supports only those security protocol versions, which is supported by the underlying SCHANNEL component of the OS.
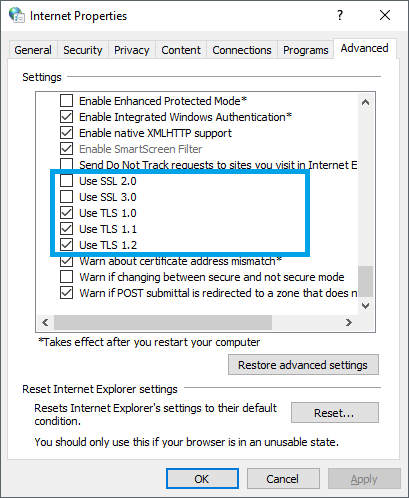
TLS settings in IE on Windows 10
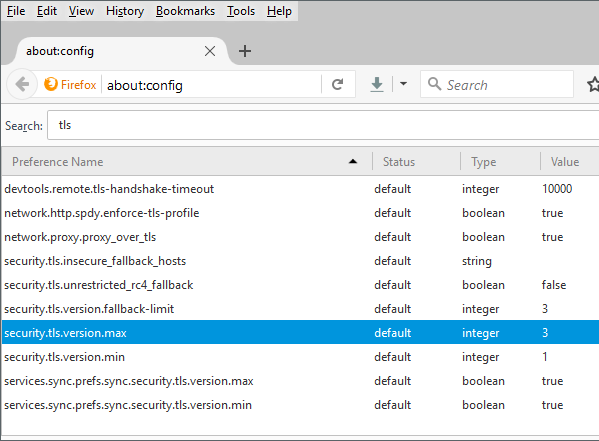
Chrome supports whatever IE supports. If you intend to check the support in Firefox, then enter the text "about:config" in the browser address bar and then enter TLS in the search bar as shown below.
The settings security.tls.version.max specifies the maximum supported protocol version and security.tls.version.min specifies the minimum supported protocol version . They can take any of the below 4 values:
- 0 - SSL 3.0
- 1 - TLS 1.0 (This is the current default for the minimum required version.)
- 2 - TLS 1.1
- 3 - TLS 1.2 (This is the current default for the maximum supported version.)
NOTE: The behavior is undefined if security.tls.version.min is larger than the security.tls.version.max value. |
Refer this Mozilla KB for more info:https://kb.mozillazine.org/Security.tls.version.*
Comments
Anonymous
October 01, 2011
Nice clear information !!! helpfulAnonymous
October 04, 2011
Excellent!! This was very helpful for meAnonymous
October 31, 2011
Hello thanks Much, About TLS 1.2 in windows Seven7, blogs.msdn.com/.../support-for-ssl-tls-protocols-on-windows.aspx, Says you have to Turn On "TLS 1.2", so Where Is The Instruction Setup, if you please ? ? ? Only In internet explorer , and, Or ,What, where, howTo, more, etc. plzzAnonymous
November 09, 2011
Hi Calvin, Sorry for the late reply. I was out on vacation, so couldn't reply to you earlier. I didn't include the instruction setup because there is a KB article on the same. Here is the link: support.microsoft.com/.../245030 Basically if you want to disable or enable TLS/SSL on the server side, it has to be done via registry. Below is a snippet from the article: <Snippet> SCHANNEL Key Start Registry Editor (Regedt32.exe), and locate the following key in the registry. HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNEL SCHANNELProtocols SubKey To enable the use of the protocols that will not be negotiated by default (such as TLS 1.1 or TLS 1.2), change the DWORD value data of the DisabledByDefault value to 0x0 in each of the following registry keys under the Protocols key:•SCHANNELProtocolsTLS 1.1Client •SCHANNELProtocolsTLS 1.1Server •SCHANNELProtocolsTLS 1.2Client •SCHANNELProtocolsTLS 1.2Server <Snippet>Anonymous
February 18, 2012
Great article, but I'd appreciate it if you'd put descriptions (altText), under your images so that users reading your information using screen readers have an idea of what you're showing us.Anonymous
February 19, 2012
thanks for the feedback Cron. I've included them now. Let me know if this helps.Anonymous
January 14, 2013
have a 32 Bit Windows 2008 machine, how do I disable the Ciphers on that server and make it not vulnerable to the BEAST.Anonymous
January 14, 2013
Kashif, There is already a fix for the Beast. Read this article: blogs.msdn.com/.../fixing-the-beast.aspxAnonymous
February 11, 2014
Why TLS 1.1 and 1.2 is not turned on by default?Anonymous
February 12, 2014
@Ray - Well the reason is that not many existing client browsers don't support TLS 1.1 and later. Even though they are the latest versions of TLS, the problem has been with the adoption of these versions. If they are enabled, there will be additional time spent in re-negotiating these parameters with the server or client. Hence they are always kept disabled.Anonymous
February 19, 2014
i m using windows 8. when i open browger its show ssl connection errors. how can i solveAnonymous
February 27, 2014
@Arif - Could you provide a snapshot or provide more details on what is being done? -- What site are you browsing? -- What browser are you using? -- What is the actual error?Anonymous
May 01, 2014
The comment has been removedAnonymous
August 14, 2014
Why Windows Server 2008 (non R2!) do not get new schannel which supports TLS 1.1/1.2 and new ciphers ? It is still in Mainstream Support till 2015. support.microsoft.com/.../default.aspxAnonymous
September 01, 2014
Hello, I am not sure why it was not added as it would have been really great to add support for latest TLS versions. The only problem I see was the major over-hauling required as the support for SSL is inbuilt into Windows. However you could provide your feedback here: http://wfp.microsoft.com/Anonymous
September 03, 2014
Hello Kaushal, I have a few android browers accessing my application which is hosted on iis 7.5 & browsers are throwing a error message saying: =============================================== Your connection to www.mysite.com is encrypted with 256 bit encrption. The connection uses TLS 1.0 The connection is encrypted using AES_256_CBC.....with sha1 for msg authencation and rsa as the key exchange mechanism. The server does not support the TLS renegotiation extension ================================================ Need your suggestion on this..do i need to change the TLS to 1.2 in registry? please help.Anonymous
September 07, 2014
Could you verify if the necessary updates are installed on the server? Check this: support.microsoft.com/.../977377. Please read carefully the instructions on how to fix this. This will affect certain functionality. You may also consider posting this problem on Windows Security Forums to get a quicker and better response: social.technet.microsoft.com/.../homeAnonymous
September 11, 2014
The comment has been removedAnonymous
September 21, 2014
@Deepak, that is a very vague issue description, Have you checked if the issue happens from other clients while accessing the same server?Anonymous
September 22, 2014
I had a problem, where TLS states were Grayed out in Win 7 64-bit OS.Anonymous
September 22, 2014
Sorry I am facing a problem when checking for a particular website its showing the page cannot be displayed. When moved to IE options , TLS states were Grayed out, How should I proceed further.Anonymous
October 16, 2014
Hello Santhosh. Looks like these settings are managed for your computer via group policy or you may want to consider launching IE as an administrator to give it a second try.Anonymous
October 28, 2014
hi Kumar, how if i enabling the TLS on Windows Server 2008 R2, is any error in the communication, whereas i enabling both SSL and TLS on IIS Service. can you explain a little bit how SSL and TLS work in encryption before 3-way TCP hanshake key. many thanks and this is a good topic.Anonymous
January 29, 2015
How can I enable TLS 1.1, 1.2 for my clients which are using windows application to connect to wcf service? I think browser specific settings to enable TLS 1.1, 1.2 are not applicable in thi case.Anonymous
February 01, 2015
Hello. I am on Windows 7 using wamp and opens SSL. How do i enable TLS 1.1 and 1.2?Anonymous
February 01, 2015
@DJ Danni OpenSSL has its own implementation for SSL/TLS. They don't rely on SCHANNEL. For OpenSSL I would suggest you to check their documentation on how to enable it. The recent version of OpenSSL does support TLS 1.1 & TLS 1.2.Anonymous
February 01, 2015
Here is my OpenSSL Version OpenSSL/0.9.8k openssl OpenSSL support enabled OpenSSL Library Version OpenSSL 0.9.8k 25 Mar 2009 OpenSSL Header Version OpenSSL 0.9.8r 8 Feb 2011 So is it possabole to use TLS 1.2 on that version? If so how do i update?Anonymous
February 02, 2015
@DJ Danni. From what I read, it is supported on 1.01 and higher versions.. www.openssl.org/.../openssl-1.0.1-notes.htmlAnonymous
February 16, 2015
Not mean to discourage people, but with technology progressing all the time, this article needs update or clearly marked so.Anonymous
March 30, 2015
Hi, can any one help me on my below query. A client has had a security assessment conducted of the web servers in their environment. They want the servers to be configured to disable SSL version 2, and to only accept SSL ciphers greater than, or equal to, 128 bits. The web servers in the environment consist of Apache 2.2 on Red Hat Enterprise Linux 6, IIS 6 on Windows Server 2003, and IIS 7.5 on Windows Server 2008 R2. Please answer the following questions:
- How do you test the servers to determine which SSL versions and ciphers are currently supported / accepted? Please describe the process.
- What changes are needed for each of the web servers / operating systems to meet the client's requirements? Please be specific.
Anonymous
April 10, 2015
what happens if you create tls 1.0, 1.1 and 1.2 keys in gpo for a mix win2k3, win2k8, win2k8r2, win2k12 environment? the keys for 1.1 and 1.2 would not enable features unsupported on win2k3, however would this cause issues if those keys now existed for gpo or is there a better method similar to enabling IE tls via gpo? (for server/apps/programs like iis)Anonymous
April 23, 2015
Hi We are using IE9 and TLS 1.0 is enable by default, if i will enable TLS 1.2 IT it will impact the other sites...?Anonymous
April 23, 2015
@Prashant - It wont!Anonymous
April 23, 2015
Hi Kaushal, Thanks for your prompt replied.. :) TLS 1.2 what exactly its enable and how it is different from TLS 1.0..? As just want to check the effects before implementing the changes.Anonymous
April 26, 2015
There are lots of difference. TLS 1.2 is the latest version while TLS 1.0 is almost obsolete.. Most of the vulnerabilities that we encounter today are related to 1.0 There re several posts describing he differences. you could go through them.Anonymous
April 27, 2015
I have a question. With PCI standards dictating now that TLSv1 needs to be disabled on web servers in order to be compliant. Yet many users are still sitting on IE 8-10 which has support for TLSv1.1 and 1.2 disabled by default. Many users simply won't be able to use these PCI compliant sites. Does Microsoft plan to enable 1.1 and 1.2 in IE 8-10 in a patch?Anonymous
April 27, 2015
It has nothing to do with IE. IE supports whatever the underlying OS supports. Until Windows Server 2012 R2/Windows 8.1 TLS 1.1/1.2 was disabled by default. It is debatable to say whether to enable it or not. However a simple solution is that we can have the registry key switched to enable the support for these protocols.Anonymous
April 28, 2015
It has everything to do with IE. Other than IE8-10 every single other browser has TLSv1.1. ans 1.2 enabled by default. IE 8-10 has that support as well but has it turned off by default. And this has nothing to do with IIS, most web servers are running on apache, tomcat or other linux variants. As it stands now, in June 2016 when every single web site on the net that has to be PCI compliant will need to disable TLSv1. Then you will have a significant number of people who are still running IE 8-10 who will not be able to access these sites by default.Anonymous
April 28, 2015
The comment has been removedAnonymous
April 28, 2015
Hi All, Couple of website is hosted in system (Windows 2008 R2) in IIS7.0 environment and now working with SSL V3.0. I want to move to TLS1.2. I have setup the the TLS1.2 in registry and disable my existing SSLv2.0,3.0, TLS1.0 & TLS1.1. Also, enable the TLS1.2 in IE and disdable all other type of SSL & TLS. Now, when I browse the app, i am getting error.
- Do I need to chnage anything in website configuration for TLS support?
- The services are currently hosted using a Verisign SSL certificate. Can we use same certificate for TLS?
Anonymous
April 28, 2015
@ Ambarish Correction: Windows Server 2008 R2 has IIS 7.5. Could you let me know the registry that you have added? You can email me at kaushalp@microsoft.com. There is no configuration in IIS to enable/disable a specific SSL protocol version. Ensure the browser you are using to communicate has TLS 1.2 enabled as well. Secondly, SSL Certificates are not dependent on the SSL protocol version.Anonymous
April 29, 2015
The comment has been removedAnonymous
April 29, 2015
Yes it is absurd that it is switched off by default on earlier OS's. I am not quite certain of the future updates that will be provided. Rather waiting as I suggested earlier push these settings off to machines via group policies. You could also submit your feedback to the IE dev team here: connect.microsoft.com/IEAnonymous
May 05, 2015
So, we just went under a Scan and now it's complaining that we need to disable TLS 1.0. That throws a couple of quick wrenches. 1st, the back end app talks over TLS 1.0 to SQL Server so we need to keep the client side enabled. Second, if I disable the server side, I can't RDP into the server. I can use weaker RDP encryption, but that's not good either. How are we getting past this aging TLS v1.0? On top of that, there are still a lot of browsers that can't use 1.1 or 1.2. I'm more concerned about RDP. Oh, and I do NOT use RDP over the internet, VPN tunnel only, so I'm guessing you'll say it's ok to use the weaker encryption. Thanks.Anonymous
May 07, 2015
@Kevin. Every single browser currently supports TLS 1.1 & 1.2. The ones that don't support them are IE running on Windows XP/Windows server 2003. The Reason being both the OS don't have native support for TLS 1.1 & TLS 1.2. If you are using Windows Vista o higher, you shouldn't have any issues. At some point you need to make the transition, it is better you do it now than at a later stage. I'm not an RDP expert, but check if the RDP client supports TLS 1.1/1.2.Anonymous
May 11, 2015
Very helpful! Thanks!Anonymous
May 28, 2015
The comment has been removedAnonymous
June 12, 2015
Hello, I am trying to make some changes to pass the PCI Compliance Scan. For starters, I was able to disable TLS 1.0 on the Exchange server but now many users outside of the network are having trouble connecting to the server via Outlook, would you happen to know what would be the best way to get them to connect? Also, I am running a terminal server on Windows Server 2008 (not R2) and I see on the top of the page that the server does not support TLS 1.1 and 1.2. Is there a way around that? I am failing because of TLS 1.0 being enabled. Thanks, SaulAnonymous
June 16, 2015
@Saul Windows Server 2008 doesn't support TLS 1.1 & 1.2. The best solution for you is to upgrade to 2008 R2 or higher.Anonymous
June 21, 2015
i am currently running windows vista and internet explorer 9, and cannot see support for tls 1.1 or tls 1.2 when i go control panel-advanced internet options. what gives? would like to keep current os and browser. you said vist or higher should have no problems.Anonymous
June 22, 2015
@Kaushal - Very useful article - thanks. In your response of the 8th May, you say "If you are using Windows Vista o higher, you shouldn't have any issues." but the table above says that Vista doesn't support TLS1.1/1.2. Can you say which is correct? (Ron's message of the 22nd suggests the table is correct). Thanks.Anonymous
July 08, 2015
This is a good but very old article. Since some people are still commenting on this article it is worth mentioning a few things. Some things are no longer true. For example all major browsers such as Chrome and Firefox have had support for TLS1.1 and TLS 1.2 for quite some time now. @Kaushal, when you enable TLS1.1 and TLS1.2 in Schannel through the registry, it is not automatically also enabled in IE settings. While it is true that IE is dependent on whatever your version of Schannel.dll supports, these are two separate settings. For viewing/changing settings on Microsoft servers without editing the registry manually you can use the free tool IISCrypto that makes the necessary registry settings for you. When disabling older protocols on the server side, such as SSL2.0, SSL3.0 please be aware that many older devices may not support TLS, for example Windows XP, older versions of android and windows mobile etc.Anonymous
July 09, 2015
I find it quite shocking that if I set up the browsers on my windows 8.1 client to insist on secure connections (ie no support - not even fall-back - for RC4, and no support for anything earlier than TLS1.2, I can no longer access the MSDN website. That doesn't much matter for pages like this one, but it's a bit of an issue for, for example, downloads.Anonymous
July 15, 2015
Hi Kushal, Can I expect help in resolving this problem : stackoverflow.com/.../ssl-protocol-tweaking-at-operating-system-level-by-editing-registry-on-windows. Thanks in advance!Anonymous
August 20, 2015
Hi Kushal, Its really a good article and gave me a lot of information about SSL and TLS. I have a problem regarding TLS 1.2. One of the webservice hosted on a customer server is having TLS 1.2, to consume that webservice I was told to use TLS 1.2 in my application hosted in different server. How this can be done. I am using Windows 2008 R2 server. I have enabled tls 1.2 in my server and tried to initiate the requests to consume the customer server's web service. But it is erroring out "could not establish secure channel for SSL/TLS with authority"Anonymous
September 01, 2015
I had confirmation that MS are developing a hotfix for Windows 2008R2 to support TLS v1.1 and v1.2. Testing is still underway (90 day test cycles) so it could be soon released.Anonymous
September 08, 2015
Tracked down a browser not able to access a web page to the SSL cert used on the web server using TLS 1.0. Similar web server apps, when SSL uses TLS 1.2 can be accessed by browser with no problem. Question: who/how decides what TLS version to use with SSL cert? Is it baked into the SSL cert at the time the SSL cert is created? It's not in the app/web server, because the app/web server code is the same in both cases -- only the SSL certs are different.Anonymous
September 22, 2015
@Aleks I have covered your answer in this post here: blogs.msdn.com/.../ssl-handshake-and-https-bindings-on-iis.aspx To answer your question, both client and server engage into a dialog (SSL Handshake) to decide the SSL protocol version.Anonymous
September 30, 2015
Hi Kaushal, I have a server 2003 machine and I'm researching what I need to do to get it to pass an SSL test (e.g. ssllabs.com). I see a lot of information about how server 2003 does not support TLS 1.1 and 1.2, but I'm also seeing a ton of information online regarding workarounds by editing the registry or various other things. e.g.: portal.chicagonettech.com/.../maximizing-ssl-security-for-windows-server-2003-ssl-tls.aspx That article appears to show only registry changes which appear to result in a grade of B from ssllabs.com, and if schannel doesn't support TLS 1.1 to begin with I don't see how any registry tweaks are going to change that. I'm not clear - is there any way to get server 2003 to disable the older insecure protocols and ciphers and only allow the current ones like TLS 1.1 and 1.2? Is the only option to upgrade the OS to a newer version? ThanksAnonymous
October 03, 2015
Since PCI DSS 3.1 will force retire TLS 1.0 from all e-commerce websites by end of June 2016, what will be Microsoft position regarding IE 9 on Vista? Will they upgrade SCHANNEL on Vista to add TLS 1.1/1.2 support or urge users to drop IE 9 and use Firefox or Chrome instead? www.pcisecuritystandards.org/.../Migrating_from_SSL_Early_TLS_Information%20Supplement_v1.pdfAnonymous
November 11, 2015
Hi Kaushal, QQ is TLS1.0 Client & Server side enabled by default on Windows 2003 and 2008? I notice that the key Client with the Dword "Enabled" (with value ffffffff) is not present by default. On Windows 2008R2 and 2012 I was able to find documentation that explicitly say is enabled by default, but for 2003 I found a bunch of kbs and notes on How to disable protocols. Thanks in advanced!Anonymous
November 13, 2015
sorry for the delayed response folks. Been away from blogging for quite some time. @Steve Windows Server 2003 and Windows Server 2008 do not have native support for TLS 1.1 and TLS 1.2. Even if you add a registry key it is of no use as the protocol itself is not recognized by the OS. There is also a reason for this. Both the protocols were proposed around 2006 and the industry started adopting this around 2010. The only solution for you would be to upgrade latest version which is Windows Server 2012 R2. @Valérie as I mentioned above TLS 1.1 and TLS 1.2 are not supported on Windows Vista and I don't see any investments being made for them to be made available on Vista. However, I am not on the product team which makes such decisions. I think it would be better if you could post a query for this on UserVoice: windows.uservoice.com/.../265757-windows-feature-suggestions @Fercha Yes, TLS 1.0 is enabled by default for client and server side on Windows Server 2003 and Windows Server 2008. You may not see any keyword in the registry for this as they are built-in.- Anonymous
November 20, 2017
The comment has been removed- Anonymous
November 29, 2017
Is the update metioned in KB installed on the server?
- Anonymous
- Anonymous
Anonymous
November 30, 2015
I am using IISCrypto at the last few years and until now all works fine with my sites Today I was asked by the PCI company to Disable TLS 1.1 AND TLS 1.0 and to enable TLS 1.2 From the moment that I enable only TLS 1.2 nobody from any browser and any pc can login to my site and the error msg is : Runtime Error Description: An exception occurred while processing your request. Additionally, another exception occurred while executing the custom error page for the first exception. The request has been terminated. Few months ago I did the same at my other sites and all works fine. I will really appreciate your help to help me understand what I am doing wrong and what should be done to solve this issue ASAP Btw- my server is windows server 2008R2 with the last updates.Anonymous
January 25, 2016
is this what the end user sees if they are trying to access a LTS1.2 encrypted portal with a browser that does not support TLS1.2?Anonymous
February 02, 2016
The comment has been removedAnonymous
February 18, 2016
@Rameez Raja IIS version is tied to Windows version. You are actually running IIS 7.5 as it is Windows Server 2008 R2. There are 2 things to note, there is a client stack and server stack. IIS consume the server stack configuration. In this blog when we modify the IE settings it is changing the settings only for IE and not IIS. You will have to modify the Even if you enable TLS1.2 it depends on the client connecting to the server. Basically you have to do this: Support article: support.microsoft.com/245030 In order to disable or enable TLS/SSL on the server side, registry has to be modified. Below is a snippet from the article: <Snippet> SCHANNEL Key Start Registry Editor (Regedt32.exe), and locate the following key in the registry. HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNEL SCHANNELProtocols SubKey To enable the use of the protocols that will not be negotiated by default (such as TLS 1.1 or TLS 1.2), change the DWORD value data of the DisabledByDefault value to 0x0 in each of the following registry keys under the Protocols key:•SCHANNELProtocolsTLS 1.1Client •SCHANNELProtocolsTLS 1.1Server •SCHANNELProtocolsTLS 1.2Client •SCHANNELProtocolsTLS 1.2Server <Snippet>- Anonymous
August 18, 2016
Any one please tell me how can i enable TLS 1.2 in excel vba to use it for a service call which uses TLS 1.2. - Anonymous
April 13, 2017
Hi Kaushal,I have TLS 1.0 , 1.1 , TLS 1.2 enabled on both Client and Server and both have the same cipher order.So which protocol is agreed by both before exchange of actual messages ? I have read somewhere they use the highest possible protocol. Is this right ? Thanks,Mrunal
- Anonymous
Anonymous
June 28, 2016
The comment has been removedAnonymous
July 27, 2016
"It is just a secure layer running on top of HTTP."No, it's a layer on top of TCP.Anonymous
August 18, 2016
Any one please tell me how can i enable TLS 1.2 in excel vba to use it for a soap service call which uses TLS 1.2.Anonymous
September 22, 2016
Hi,I have a Windows Server 2003. IIS 6 is running on that and TLS 1.0 is available. I have a classic ASP based web application hosted on that server. It has a payment module that connects to PayPoint payment API via https query string from the server side. I checked the paypoint url in the ssllabs and it supports all transport protocols. The application stopped working since March 2016. I am not able to figure out the error. I initially thought it could be because of the TLS 1.2 version because most of the industry is heading towards that direction and thought that the issue is because the server is Windows 2003. However, the test payment link from PayPoint worked in FireFox browser and it showed that it used TLS 1.2 for the transaction. For a moment I lost my mind.. Does FireFox has the complete implementation of TLS 1.2 build within? So, if the browser or the client application is going to support TLS 1.2 does it really matter whether the server supports TLS 1.2 or not, windows server 2003 in this case? On the receiving end of the transport connectivity, PayPoint in this case, is it possible for the PayPoint software to put restrictions on the inbound connections to use only TLS 1.2. The ssllabs says the server supports all protocols. I am sorry for so many questions, but I no very little about this level of connectivity.Please provide any thoughts.ThanksPanduAnonymous
September 22, 2016
An associated question to my previous question:Can a browser or a client application fully support or implement a Transport Layer Protocol (either directly or with the help of .NET framework, in the case of applications) even if the underlying Operating System does not support that version of protocol?ThanksPanduAnonymous
October 24, 2016
Mozilla just announced plans to enable TLS 1.3 by default in Firefox 52 (currently scheduled for March, 2017) https://groups.google.com/forum/#!topic/mozilla.dev.platform/sfeqeMkyxCI. Can you talk about Microsoft's plans for enabling TLS 1.3 in Schannel (to allow those of us running IIS web sites to use it)? Thanks.Anonymous
October 31, 2016
Hi Kaushal,Why my IE11 shows encrypted in connection properties..?Supose showing TLS something, right?Anonymous
November 02, 2016
Firefox now supports TLS 1.3 with version 49 it will be default on after version 49 0 – SSL 3.0 1 – TLS 1.0 (This is the current default for the minimum required version.) 2 – TLS 1.1 3 – TLS 1.2 (This is the current default setting in version 49) 4 – TLS 1.3 (This is the capable setting for version 49+)Anonymous
November 15, 2016
No commentsAnonymous
November 17, 2016
We need to provide https support to Windows XP clients with IE 6.0.We are using wininet API for internet communication. On XP SP3 after enabling TLS 1.0 https connection is established.But this doesn't work on XP SP2 and lower. Is https connection possible on XP SP2 and lower?How can we find weather the IE and OS support Https connection or not?Please suggest solution.Anonymous
November 24, 2016
Hello,I want to know what are all the dependencies needed for upgrading TLS v1.0 to v1.2 for various web servers.Anonymous
December 02, 2016
Nice 1! Like a breath of fresh air. U turned on the light bulbs for me mate. ThanksAnonymous
December 14, 2016
The comment has been removedAnonymous
December 20, 2016
Does anyone know a way to get server 2008 r2 to be able to do tls 1.2 to paypal on the classic asp server side posts? I haev set the registry and in the code I have set option 9 to 128, etc.I still get channel error. Same code on my windows 10 pro IIS server works just fine.Anonymous
January 07, 2017
Can anyone give me some insight on how to update Openssl on a Windows Server 2012 R2? We are being impacted by the PCI industry changes and have not been able to get much support from our host provider. It seems we are running 0.9.8c and need to upgrade to 1.1.0c. Any thoughts or insight that you can share will be greatly appreciated. I tried to look on the consulting boards for a Openssl or TLS expert, but couldn't find anyone in my query. Been struggling to fix this for 4 weeks now...please hlep. Thanks!Anonymous
January 20, 2017
Hi Kaushal, Nice article. I want to know by default in Internet Explorer TLS 1.0, TLS 1.1, TLS 1.2 is used/enabled.If i unchecked this all TLS then my website is not displaying giving error like : "This page can’t be displayed, Turn on SSL 3.0, TLS 1.0, TLS 1.1 and TLS 1.2 in Advanced settings and try connecting to website name"Can you please suggest why this is happening and other websites are running without TLS checked.If you can provide any idea then it will be great ASAP.ThanksAnonymous
March 14, 2017
is there any script to get this output of this ( security tab) from multiple servers at once.Anonymous
July 25, 2017
Windows Server 2008 SP2 now supports TLS 1.1 and TLS 1.2https://support.microsoft.com/en-us/help/4019276/update-to-add-support-for-tls-1-1-and-tls-1-2-in-windows-server-2008-s- Anonymous
October 04, 2017
It was pending for quite some time now. Thanks! I updated the article.
- Anonymous
Anonymous
August 11, 2017
Do you have any experience or are you aware of any issues for UWP apps?We have an UWP app running in Windows 10 that stopped working after the service we were connecting to disabled TLS1.0. We tried several things and we are not sure if the issue is on the app or on the network. But it seems there are no options for enforcing TLS1.2 on the WEB APIs for UWP,- Anonymous
October 04, 2017
I am not familiar with UWP as such. But can provide pointers. What namespace are you using to initiate the TLS connection?
- Anonymous
Anonymous
October 04, 2017
The update made to this page today has broken the formatting in the tableAlso, does Google Chrome use it's own built-in support for TLS 1.1 and 1.2, and if so, would this work on XP clients, or does it use the system libraries for this and so wouldn't?Thanks- Anonymous
October 04, 2017
Google chrome seems to use the SSL client stack of internet explorer for this and hence doesn't support.- Anonymous
November 20, 2017
Google Chrome uses NSS libraries for SSL/TLS which are independent from Windows and Internet explorer TLS settings (https://developer.mozilla.org/en-US/docs/Mozilla/Projects/NSS). Therefore, regardless of TLS support on OS or IE level, Chrome will still work as long as we don't change TLS settings in Chrome.- Anonymous
November 29, 2017
@Anh, You are mistaken. Chrome uses native Windows API for implementing SSL/TLS on Windows. if you try changing the TLS setting in the chrome browser on Windows, you will see a pop-up for IE settings. Instructions are available here: https://productforums.google.com/forum/#!topic/chrome/Ij5Ylga52ygAlso, Chrome is transitioning to OpenSSL from NSS. See the discussion thread here: https://security.stackexchange.com/questions/59184/which-browsers-are-using-openssl
- Anonymous
- Anonymous
- Anonymous
Anonymous
October 04, 2017
Hi Kaushal,Thanks for sharing knowledge through this article and your support. Currently we ran through a problem. We updated TLS-1.2 in Windows-2012 Enterprise and we were accessing through RDP session from Windows 2008 R2-SP1. We lost our RDP session W2K8 -R2 throws an error while connecting RDP session. We used KB3080079 (https://support.microsoft.com/en-us/help/3080079/update-to-add-rds-support-for-tls-1.1-and-tls-1.2-in-windows-7-or-windows-server-2008-r2 ).But still unable to open a RDP session. Any Suggestions?- Anonymous
October 16, 2017
Its difficult to provide recommendations without much insights into the issue. I would suggest to perform checks on the client and server and ensure that TLS 1.2 is enabled for both Client and Server stacks. Take a network trace from both client and server to ensure that the SSL handshake is completing.
- Anonymous
Anonymous
November 13, 2017
Note that you can't just use GetVersionEx to discover if you're on Windows 8.1 or Server 2012 R2 or newer to know TLS 1.2 will be there. GetVersionEx will lie and return an incorrect value if your application hasn't been manifested for 8.1/2012 R2 :( Ticked off right now...Anonymous
June 25, 2018
Kaushal, thank you so much for this information. It was very helpful for me.Anonymous
July 17, 2018
• Disablement of TLSv1.0 on vCenter Server and/or Platform Services Controller on Windows Server 2008 as the Host OS (Windows) supports only TLSv1.0. Newer versions of Windows Server support disablement of TLSv1.0. We have installed vCenter Server and/or Platform Services Controller on Windows Server 2008 R2 will it be able to disable TLS 1.0 ?Could you please check and assist on this.