Project VAST and Azure Sentinel: a Match Made in the Cloud
Howdy folks,
Whew, what an eventful couple of weeks. As you may have heard, Microsoft unveiled the public preview of Azure Sentinel in which we have "reimagined the SIEM tool as a new cloud-native solution..." (https://azure.microsoft.com/en-us/blog/introducing-microsoft-azure-sentinel-intelligent-security-analytics-for-your-entire-enterprise/). I couldn't be more excited about this solution, and the complimentary story between Sentinel and VAST. By way of background, here's a nice summation from the PG: Azure Sentinel provides intelligent security analytics at cloud scale for your entire enterprise. Azure Sentinel makes it easy to collect security data across your entire hybrid organization from devices, to users, to apps, to servers on any cloud. It uses the power of artificial intelligence to ensure you are identifying real threats quickly and unleashes you from the burden of traditional SIEMs by eliminating the need to spend time on setting up, maintaining, and scaling infrastructure. Since it is built on Azure, it offers nearly limitless cloud scale and speed to address your security needs. Traditional SIEMs have also proven to be expensive to own and operate, often requiring you to commit upfront and incur high cost for infrastructure maintenance and data ingestion. With Azure Sentinel there are no upfront costs, you pay for what you use.
One concept included in Sentinel is that of "Dashboards." These are pre-configured data visualizations that are optimized to intelligently display a particular data stream.
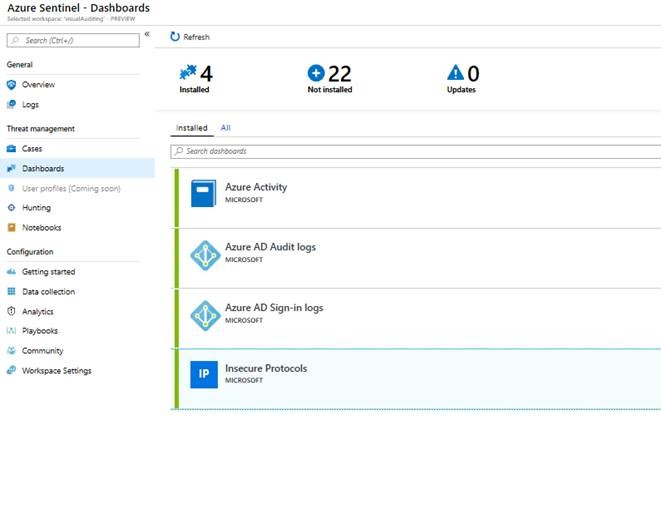
You can probably see where this is heading. For VAST KPIs and detections that solely depend upon log data (and not on, for example, querying Active Directory attribute data), Sentinel dashboards offer an excellent lighter-weight solution. And I'm happy to announce that Brian and I (the VAST team) supplied the Insecure Protocols dashboard with the Azure Sentinel product team. It's right there, baked into the product. :)

Rather than trying to describe it to you, I think it's best if I walk through the steps to utilize Sentinel for Insecure Protocol detection. Let's take the example of SMB1. In case this somehow isn't clear, you really need to get SMB1 out of your environment. And if you've been following along to the previous entries, you know that can be tricky without some intelligent log aggregation and thoughtful visualizations. (For more on auditing SMB1 with VAST, go here.)
To start, you would turn on SMB1 auditing on your servers or a subset of servers. You would install the MMA and configure Azure Monitor (Log Analytics) to forward EventID 3000. (Note: Sentinel supports Windows Event Forwarding, meaning that we no longer have to install the Microsoft Monitoring Agent on every server we want to audit.) Once you have the data in Azure, the Insecure Protocols dashboard will display the log data to you visually. In other words, what VAST does with Power BI, Sentinel does with a built-in dashboard (and it's VAST approved :) ).

There it is -- and you're off to go root out SMB1 across your estate.
I've already been getting some questions that merit some attention here:
- Is Sentinel replacing VAST? No. There are some advantages, and different focuses, to both. For example, the Sentinel Insecure Protocols dashboard is much lighter weight and easier to implement than VAST's Power BI-based dashboard. On the other hand, this single dashboard only represents about 25% of the KPIs and detections available in VAST at present. Sentinel is also a full-on cloud-native SIEM replacement in a way that VAST doesn't intend to be. That said, there may come a time when it makes sense for us to re-platform VAST onto Sentinel, but that time is in the future. For instance, we would need to figure out how to import Administrative User data into Sentinel before we could report on Administrative behavior.
- Which should our org use? It depends on your goals. Insecure Protocols is but one of 26 (and counting!) dashboards that ship with Sentinel. And dashboards are but one facet of Sentinel's functionality. And as I mentioned, Insecure Protocols is only a fraction of VAST's capability as well. If you are using one and it is working for you, I would broadly suggest you continue using it, while learning about additional capabilities.
- What about for Insecure Protocols only? If you want Insecure Protocol information with the lightest touch possible, Sentinel. If you need information about your Privileged Accounts and Insecure Protocols, VAST.
- Is VAST going away? No. :)
As always, please send me your questions or comments. And until then, happy auditing.
Edit: For detailed instructions on setting up the Insecure Protocols Dashboard in Sentinel, please navigate here.
Comments
- Anonymous
March 05, 2019
Great article Jon, thanks for taking the time to share.