WinRM (Windows Remote Management) Troubleshooting
What is WinRM?
New in Windows Vista, Windows Server 2003 R2, Windows Server 2008 (and Server 2008 Core) are WinRM & WinRS. Windows Remote Management (known as WinRM) is a handy new remote management service. WinRM is the “server” component of this remote management application and WinRS (Windows Remote Shell) is the “client” for WinRM, which runs on the remote computer attempting to remotely manage the WinRM server. However, I should note that BOTH computers must have WinRM installed and enabled on them for WinRS to work and retrieve information from the remote system.
While WinRM listens on port 80 by default, it doesn't mean traffic is unencrypted. Traffic by default is only accepted by WinRM when it is encrypted using the Negotiate or Kerberos SSP. WinRM uses HTTP (TCP 80) or HTTPS (TCP 443). WinRM also includes helper code that lets the WinRM listener to share port 80 with IIS or any other application that may need to use that port.
WinRM with SCVMM uses Kerberos for authentication, and does not support fall-back to NTLM. There will be an error instead. If no credentials are specified, then the logged-on credentials are used to authenticate against the remote machine. This allows for a single sign-on experience.
What is WinRS?
Remote Shell, (WinRS) is used to execute a program on a remote host. Similar in operation to the former Sysinternals tool PSExec, WinRS leverages Windows Remote Management to let you launch processes on remote machines. For example, if you want to perform a directory listing on the system drive on a remote machine, you can remotely launch ‘dir’ using this syntax:
winrs -r:machinename dir
Another handy use of WinRS can be when installing software on remote systems. If you want to quietly install an application using an MSI file onto a remote machine, use the following syntax. This syntax assumes the MSI file has already been deposited into the C:\ folder.
winrs -r:machinename msiexec.exe /i c:\install.msi /quiet
When specifying the remote machine, the following are valid:
· Localhost
· NetBIOS name
· Fully Qualified Domain Name (FQDN)
· IP address
How to install WinRM
The WinRM is not dependent on any other service except WinHttp. If the IIS Admin Service is installed on the same computer, you may see messages that indicate WinRM cannot be loaded before Interent Information Services (IIS). However, WinRM does not actually depend on IIS: these messages occur because the load order ensures that the IIS service starts before the HTTP service. WinRM does require that WinHTTP.dll be registered.
(Stated simply: WinRM service should be set to Automatic (Delayed Start) on Windows Vista and Server 2008)
· The WinRM service starts automatically on Windows Server 2008.
· On Windows Vista, the service must be started manually.
· UPDATE! Windows 2003 requires an update for WinRM
936059 An update is available for the Windows Remote Management feature in Windows Server 2003 and in Windows XP
https://support.microsoft.com/default.aspx?scid=kb;EN-US;936059
How to configure WinRM
To set the default configuration type:
winrm quickconfig (or the abbreviated version, winrm qc)
‘winrm qc’ performs the following operations:
1. Starts the WinRM service and sets the service startup type to auto-start.
2. Configures a listener for the ports that send and receive WS-Management protocol messages using either HTTP or HTTPS on any IP address.
3. Defines ICF exceptions for the WinRM service and opens the ports for HTTP and HTTPS.
(Note: Winrm quickconfig also configures Winrs default settings)
If ‘winrm qc’ throws an error:
If the firewall is disabled the quick config command will fail. The firewall can either be started in Services long enough to run ‘winrm qc’ or the commands below can be run:
sc config "WinRM" start= auto
net start WinRM
winrm create winrm/config/listener?Address=*+Transport=HTTP
netsh firewall add portopening TCP 80 "Windows Remote Management"
Group Policy configuration:
WinRM can be configured by group policies.
1. Type gpedit at a command prompt. The Group Policy Object Editor window opens.
2. Look for the Windows Remote Management and Windows Remote Shell Group Policy Objects (GPO) under Administrative Templates and Windows Components.
Troubleshoot WinRM
Common Issues:
1. If the ISA2004 firewall client is installed on the computer, it can cause a Web Services for Management (WS-Management) client to stop responding. To avoid this issue, install ISA2004 Firewall SP1.
2. Antivirus software can prevent proper WinRM communication. Disable antivirus software and reboot the machine if the Antivirus software is known to scan processes and protocols, or if there is any doubt about the software.
Test WinRM communication on the local and remote machines
This section addresses how to test whether WinRM is working on the local system, and whether it can communicate with the remote system. Test remote communication in both directions between machines.
Local communication:
Locate listeners and addresses: (No output means WinRM is not installed)
winrm e winrm/config/listener
Localhost Ping:
(Successfully completing this step pretty much insure complete access to WSMan on the local system)
Winrm id
Further:
Check state of configuration settings:
winrm get winrm/config
Check the state of WinRM service:
winrm get wmicimv2/Win32_Service?Name=WinRM
Remote communication:
Locate listeners and addresses:
winrm e winrm/config/listener
Remote Ping:
(Successfully completing this step pretty much insure complete access to WSMan on the remote system)
Winrm id –r:machinename
Further:
Check state of configuration settings:
winrm get winrm/config -r:machinename
Check the state of WinRM service:
winrm get wmicimv2/Win32_Service?Name=WinRM -r:machinename
Sample Commands
Here are some sample commands to play with. If you cannot get the ‘Test WS-Man...' step to work, none of the steps following will work either (you're probably not using the right credentials to access the remote machine). One more caveat, the remote commands work best on domain joined machines. For workgroup machines, the WinRM service needs additional configuration.
Description |
Command |
Run from an Elevated Command prompt |
|
Quickly configure the WS-Man service |
winrm QuickConfig |
Quickly delete the WS-Man listener |
winrm invoke Restore winrm/Config @{} |
Run from an standard Command prompt |
|
Display your machine's basic hardware info |
winrm enumerate wmicimv2/Win32_ComputerSystem |
Display your operating system properties |
winrm get wmicimv2/Win32_OperatingSystem |
Output your OS info in XML |
winrm get wmicimv2/Win32_OperatingSystem -format:pretty |
Test WS-Man access to a remote machine** |
winrm id -remote:<some machine> |
Grab a remote machine's WS-Man config |
winrm get winrm/Config -r:<some machine> |
Grab a remote machine's CPU load |
winrm g wmicimv2/Win32_Processor?DeviceID=CPU0 -fragment:LoadPercentage -r:<some computer> |
Grab a remote machine's free memory |
winrm g wmicimv2/Win32_OperatingSystem -fragment:FreePhysicalMemory -r:<some computer> |
Stop a service on a remote machine |
winrm invoke stopservice wmicimv2/Win32_Service?name=w32time -r:<some computer> |
Start a service on a remote machine |
winrm invoke startservice wmicimv2/Win32_Service?name=w32time -r:<some computer> |
Reboot a remote machine |
winrm invoke reboot wmicimv2/Win32_OperatingSystem -r:<some computer> |
Run a command on a remote machine (this uses winrS, not winrM) |
winrs -r:<some computer> ipconfig /all |
Run from PowerShell |
|
Use PowerShell to grab the WS-Man Win32_OperatingSystem XML output |
[xml]$osInfo = winrm get wmicimv2/Win32_OperatingSystem /format:pretty |
Display the OS version property |
$osInfo.Win32_OperatingSystem.Version |
Display the last boot time |
$osInfo.Win32_OperatingSystem.LastBootupTime.DateTime |
Put free memory metric into an XML variable |
[xml]$freemem = cmd /c "winrm get wmicimv2/Win32_OperatingSystem -fragment:FreePhysicalMemory -f:pretty -r:<some computer>" |
Display the free memory value |
$freemem.XMLFragment.FreePhysicalMemory |
**Note: This step verifies that you have good connectivity to the remote machine, WS-Man is running and properly configured on the remote machine, AND you have the correct permissions to fully leverage WS-Man on the remote machine. If this step fails, it's probably a permissions issue.
Advanced Concepts
URI Aliases
URI aliases can simplify the Winrm command line. The following URI aliases are supported:
wsman = wsman:microsoft.com/wsman/2005/06/
cimv2 = https://schemas.microsoft.com/wsman/2005/06/wmi/root/cimv2
For example, the following command:
winrm get https://schemas.microsoft.com/wsman/2005/06/wmi/root/cimv2/Win32_Service?Name=WSMan
Gets replaced with:
winrm get wmi/root/cimv2/Win32_Service?Name=WinRM
Performing an Invoke Operation
‘Invoke’ initiates commands
winrm invoke StartService wmicimv2/Win32_Service?Name=WinRM -r:machinename @{}
This will likely return ‘ReturnValue = 10’ on a remote system where WinRM is running
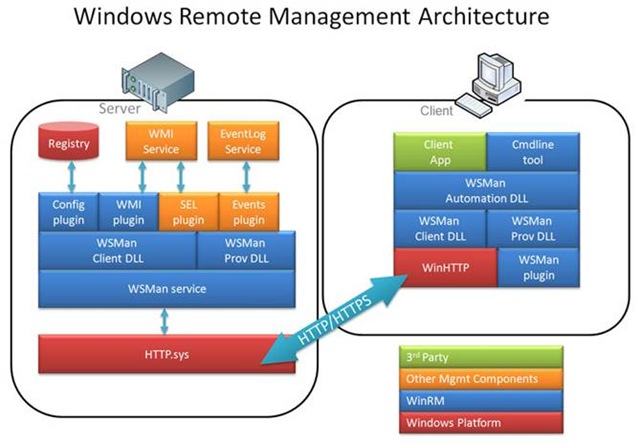
WS-Man (WinRM) Architecture
The following diagram shows a high-level overview of the WS-Man (WinRM) architecture. In the diagram the 'Client' is querying the 'Server' for WS-Man information. Note that HTTP.sys and WinHTTP support the HTTP(s) transport for WS-Man, not IIS. In addition, IIS (or another web publishing service) can co-exist with WS-Man and share port 80.
Remember:
WinHTTP = Client
HTTP.SYS = Server
The Windows Remote Management architecture consists of components on the client and server computers. The following illustration shows the components on both computers, how the components interact with other components, and the protocol that is used to communicate between the computers.
Requesting Client
The following WinRM components reside on the computer that is running the script that requests data.
· WinRM application
This is the script or Winrm command-line tool that uses the WinRM scripting API to make calls to request data or to execute methods. For more information, see the WinRM Scripting API [ https://msdn.microsoft.com/en-us/library/aa384469(VS.85).aspx ] .
· WsmAuto.dll
The OLE automation layer that provides scripting support.
· WsmCL.dll
C API layer within the operating system.
· HTTP API
WinRM requires support for HTTP and HTTPS transport.
Responding Server
The following WinRM components reside on the responding computer.
· HTTP API
WinRM requires support for HTTP and HTTPS transport.
· WsmAuto.dll
The OLE automation layer that provides scripting support.
· WsmCL.dll
C API layer within the operating system.
· WsmSvc.dll
WinRM listener [ https://msdn.microsoft.com/en-us/library/aa384465(VS.85).aspx ] service.
· WsmProv.dll
Provider subsystem.
· WsmRes.dll
Resource file.
· WsmWmiPl.dll
WMI plug-in [ https://msdn.microsoft.com/en-us/library/aa384465(VS.85).aspx ] . This allows you to obtain WMI data through WinRM.
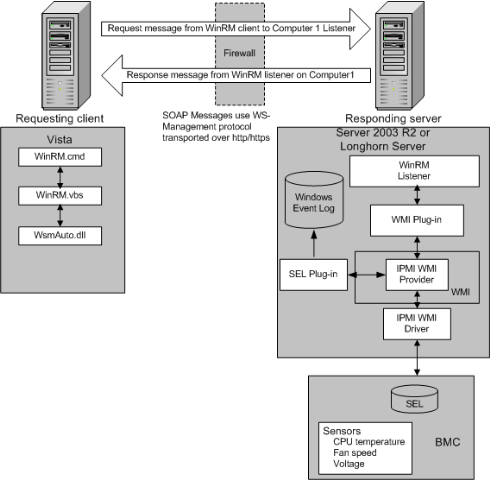
· Intelligent Platform Management Interface (IPMI) driver and WMI IPMI provider
These components supply any hardware data that is requested using the IPMI classes. For more information, see Intelligent Platform Management Interface (IPMI) Classes [ https://msdn.microsoft.com/en-us/library/aa390891(VS.85).aspx ] . BMC hardware must have been detected by the SMBIOS or the device created manually by loading the driver. For more information, see Installation and Configuration for Windows Remote Management [ https://msdn.microsoft.com/en-us/library/aa384372(VS.85).aspx ] .
References
Installation and Configuration for Windows Remote Management
https://msdn.microsoft.com/en-us/library/aa384372(VS.85).aspx
Windows Remote Management Command-Line Tool (Winrm.cmd)
https://technet.microsoft.com/en-us/library/cc781778.aspx
How can Windows Server 2008 WinRM & WinRS help you
https://windowsnetworking.com/articles_tutorials/How-Windows-Server-2008-WinRM-WinRS.html
The things that are better left unspoken Remotely managing your Server Core using WinRM and WinRS
Redmond Print First Look WinRM & WinRS
https://redmondmag.com/columns/article.asp?EditorialsID=2262
Otto Helweg - Management Matters A Few Good Vista WS-Man (WinRM) Commands
https://blogs.technet.com/otto/archive/2007/02/09/sample-vista-ws-man-winrm-commands.aspx
Windows Remote Management Architecture
https://msdn.microsoft.com/en-us/library/aa384464(VS.85).aspx
Comments
Anonymous
January 01, 2003
The comment has been removedAnonymous
January 01, 2003
Jonathon Jordan has written a great article on troubleshooting WinRM on his blog site. SCVMM relies heavilyAnonymous
January 01, 2003
Excellent information! Thanks! Could you please write something up ( :-)) ) how to configure WinRM communication over https rather than http which transmit over clear-text? Thanks :-) You give us more, we want more ;pAnonymous
January 01, 2003
What we will be going over in this blog is one of the improvements of Distributed Transaction CoordinatorAnonymous
January 01, 2003
thank youAnonymous
January 01, 2003
PingBack from http://antivirussoftware.titeblog.com/?p=2483Anonymous
August 07, 2010
How to retrieve WMI property qualifiers using WINRM? Example: By using below query we can disk read rate, so how we can get countertype property qualifier of "DiskReadsPerSec ".? "select DiskReadsPerSec from Win32_PerfRawData_PerfDisk_LogicalDisk" Thanks in Advance. VJAnonymous
August 31, 2010
The comment has been removedAnonymous
September 07, 2010
The comment has been removedAnonymous
September 22, 2010
The comment has been removedAnonymous
June 22, 2011
Great Blog found it in a search for some troubleshooting I was doing and it had a great mix of architecture, troubelshooting and usage.Anonymous
April 07, 2014
The comment has been removed