Configuring Network Inspection System (NIS)
Network Inspection System (NIS), the vulnerability signature component of TMG Intrusion Prevention System (IPS), comes with a pre-defined recommended policy out of the box – this is the recommended configuration for NIS. Nevertheless, NIS supports granular control and policy configuration to comply with your specific organization needs, troubleshooting and investigation requirements.
In this blog, I would like to explore NIS configuration options while in subsequent blog postings, we will explore how they can be used for specific detailed scenarios.
General configuration
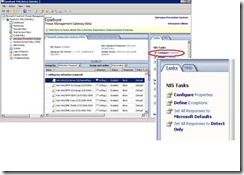
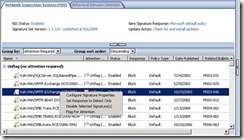
You can easily locate configuration options on the Task Menu of the NIS IPS Tab.
Once you click on Configure Properties task, the main NIS Properties Configuration Pane is ready to use.
Enabling NIS– Properties Configuration Pane:
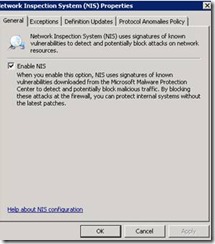
NIS is enabled by default.
If NIS is disabled, click on Configure Properties the main NIS Properties Configuration Pane.
Check Enable NIS à you are ready to go!
You can choose to Enable or Disable NIS. If you choose to Disable NIS, your policy configuration (signature overrides, new signature policy, exception list etc) are still saved. Once you enable NIS you are up and running again with no further action required. NIS it will immediately check for new updates and comply with your signature snapshot update policy.
Configuring Signature Sets Updates
NIS uses signatures developed by the Microsoft Malware Protection Center to protect un-patched systems from attacks that exploit known vulnerabilities of Microsoft operating systems and applications. To keep your systems protected from the latest threats, we recommend that you verify that you have connectivity to the appropriate update source (Microsoft Update or WSUS) and that you enable automatic installation of the latest signatures.
Before you can use Forefront TMG to block attacks on known vulnerabilities, you must first download the latest NIS signature set. Follow the instructions below to configure NIS signature set updates.
To manage NIS signature set downloads:
- In the Forefront TMG Management console, in the tree, click the Intrusion Prevention System node.
- On the Tasks tab, click Configure Settings.
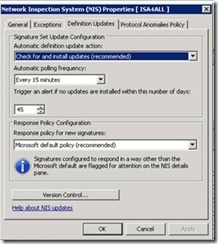
- On the Update Configuration tab, under Select automatic update action, select one of the following options:
- Check for and install updates (recommended) — select this configuration to automatically download and install the latest signature updates.
- Only check for updates — select this configuration to be notified of the availability of new signatures for download.
- Do nothing — select this configuration to disable automatic updates.
- Select Automatic Polling Frequency – Recommended default is 15 minutes. Definition Updates will be downloaded only when new ones are available!
- Under Select the response policy for new signatures, select one of the following options:
- Microsoft default policy (recommended) — select this configuration to accept the default response to the signature.
- Detect only response — select this configuration to record a log only when traffic matching this signature is detected.
- No response (disable signature) — select this configuration to take no action and to not record a log if traffic matching this signature is detected.
You can click the Version Control button to select older signature snapshot. This feature should be used only for troubleshooting scenario; this will be discussed in detail in a future blog posting; stay tuned…
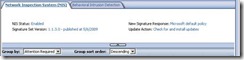
You can verify the NIS overall Signature Update Configuration in the Information Bubble in the main Pane:
or through the TMG Update Center, the centralized management console for all TMG protection mechanisms definition updates. This is an area for a dedicated blog; stay tuned…
Configuring Exceptions
NIS allows you to exclude network entities from inspection. You may choose to exclude any network objects known to TMG (IP Sets, URLs Sets etc) for capacity planning or troubleshooting scenarios. When you exclude a network object both incoming and outgoing traffic is excluded from inspection.
To manage NIS exceptions:
1. In the Forefront TMG Management console, click the Intrusion Prevention System node.
2. On the Tasks tab, click Define Network Inspection System Exceptions.
3. On the Exceptions tab, click Add, and then select the network entities you want to exclude from inspection.
4. When finished, on the Apply Changes bar, click Apply.
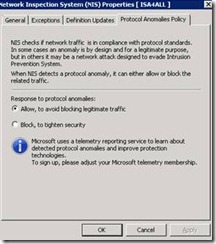
Configuring Protocol Anomaly Policy
Network Inspection System (NIS) checks that the network traffic is in compliance with protocol standards. In some cases, an anomaly is by design and for a legitimate purpose, but in others it may be a network attack designed to evade intrusion prevention systems. You can choose which action NIS takes when detecting traffic with a protocol anomaly: Allow, avoiding blocking legitimate traffic or Block, to tighten security.
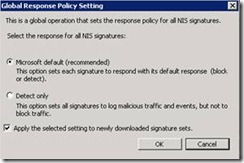
Configuring Global Setting
NIS can be operated in Either Microsoft Recommended Default (Discussed more in Signature Overrides section next) or as Intrusion Detection System (IDS). Once Global Policy is chosen new signature updates will receive the Global Policy setting automatically.
Configuring Signatures Overrides
NIS allows you to have granular control over policy configuration. Basically, NIS comes with a pre-defined recommended policy out of the box – this is the recommended configuration for NIS. The NIS Response Team set the Recommended Policy based on multiple factors including the vulnerability severity and business impact. Microsoft Malware Protection Center may change the recommended policy automatically through signature snapshot update. If you choose your own policy, such as setting a “Block” mode signature to "Detect Only" we will not change it automatically for you.
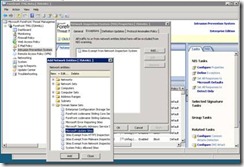
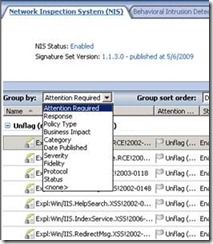
You can change the policy for a specific signature, multiple selection signatures or a group of signatures.
To select a group of signatures, you should group the signature by choosing one of the pull down options available in the NIS IPS Tab: Response, Policy Type, Business Impact, Category, Date Published, Severity, Fidelity, Protocol or Status.
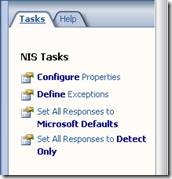
Once a group is selected , you can choose the appropriate policy from the Task Menu or by right click options available below:
You can also perform an operation on all signatures to enable NIS as an Intrusion Detection System (IDS) by setting all responses to “Detect Only” or Intrusion Prevention System (IPS) by setting all responses to Microsoft Recommended Defaults.
Watch for our upcoming blog entries and whitepapers planned for the near future discussing NIS deployment, monitoring and troubleshooting in depth.
Author
Moshe Golan, GAPA Program Manager – Forefront
Reviewers
David B. Cross, Product Unit Manager – Forefront
Avi Ben-Menahem, GAPA Group Manager – Forefront
Evgeny Skarbovsky, GAPA Senior Development Lead – Forefront
Erez Sharvit, GAPA Software Developer Engineer – Forefront