Artificial Intelligence and Machine Learning for NextGen Threat Protection

Traditionally detecting and responding to cyber threats always relied on understanding precedence, matching patterns, writing definitions and configuring rules based actions for mitigations.
Given the kind of sophistications, polymorphism and expedited rate of change in threat landscape seen nowadays, traditional methods involving human touch at each and every point proving to be inadequate and inefficient.
Rule based action can only scale up to manage commodity attacks but whenever there is a slight difference in the attack technique the whole rule falls apart.
Machine learning and Artificial Intelligence can achieve high rate of precision of detecting and responding to a threat by analyzing various datasets with lots of dimension which human cannot scale.
Just to give you an idea and how polymorphic pattern of threats are emerging :
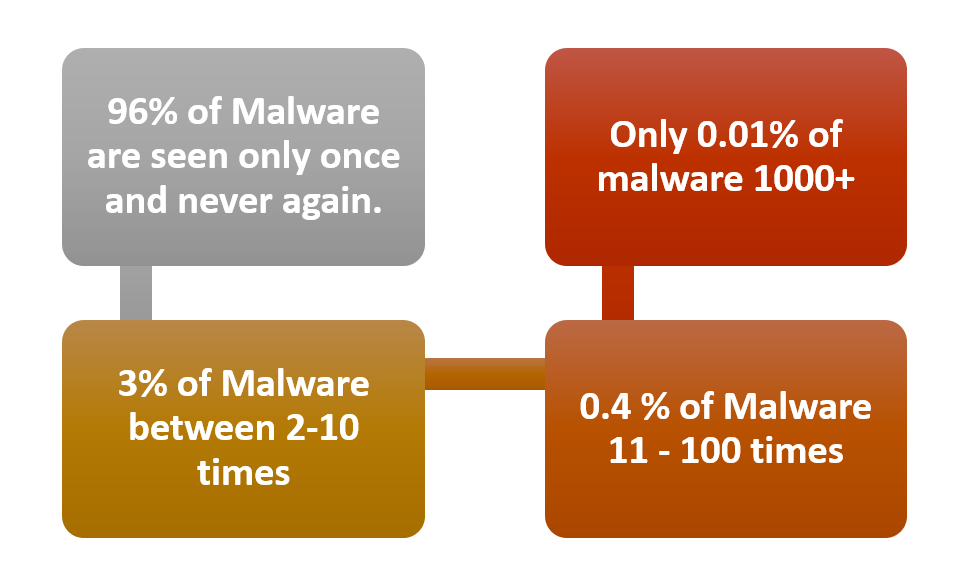
Machine Learning models can uncover blind spots by removing human bias that comes with expertise, such as confirmation bias to reveal greater insights.
Machine learning for building Threat Intelligence: The Intelligence Security Graph (ISG)
In reducing the time it takes to detect an attack and its techniques, enterprise companies are struggling with a contradictory dilemma between having too much security-related data to process yet still not having enough information to separate the signal from the noise and understand an incident quickly.
The challenge here is not just sheer volume, but also separation. Many indicators of attack either seem innocent on their own, or are separated by industries, distances and timeframes. Without clear insight into the whole dataset, early detection becomes a game of chance. Even the largest enterprise companies are facing these limitations:
- Real threat intelligence requires more data than most organizations can acquire on their own.
- Finding patterns and becoming smarter in that huge data pool requires advanced techniques like machine learning along with massive computing power.
- Ultimately, applying new intelligence so that security measures and technologies constantly improve requires human experts who can understand what the data is saying, and take action.
As a platform and services company, Microsoft’s has a wider optics of threat and activity data comes from all points in the technology chain, across every vertical industry, all over the world. This enables us to diagnose attacks, reverse engineer advanced threat techniques, and apply that intelligence across the platform.
Following image shows how ML can see various signals across the technology chain and helps building threat Intelligence which can help detect attacks much faster and help mitigate. 
For nearly two decades, Microsoft has been turning threats into useful intelligence that can help fortify its platform and protect customers. Since the Security Development Lifecycle born from early worm attacks like Blaster, Code Red and Slammer, to modern security services woven into our platforms and services, the company has continually built processes, technologies and expertise to detect, protect, and respond to evolving threats.
These threat intelligence has helped Microsoft to work with law enforcements in various countries in taking down some of the major global botnets like Citadel, Ramnit, Dorkbot, and very recently Gamarue.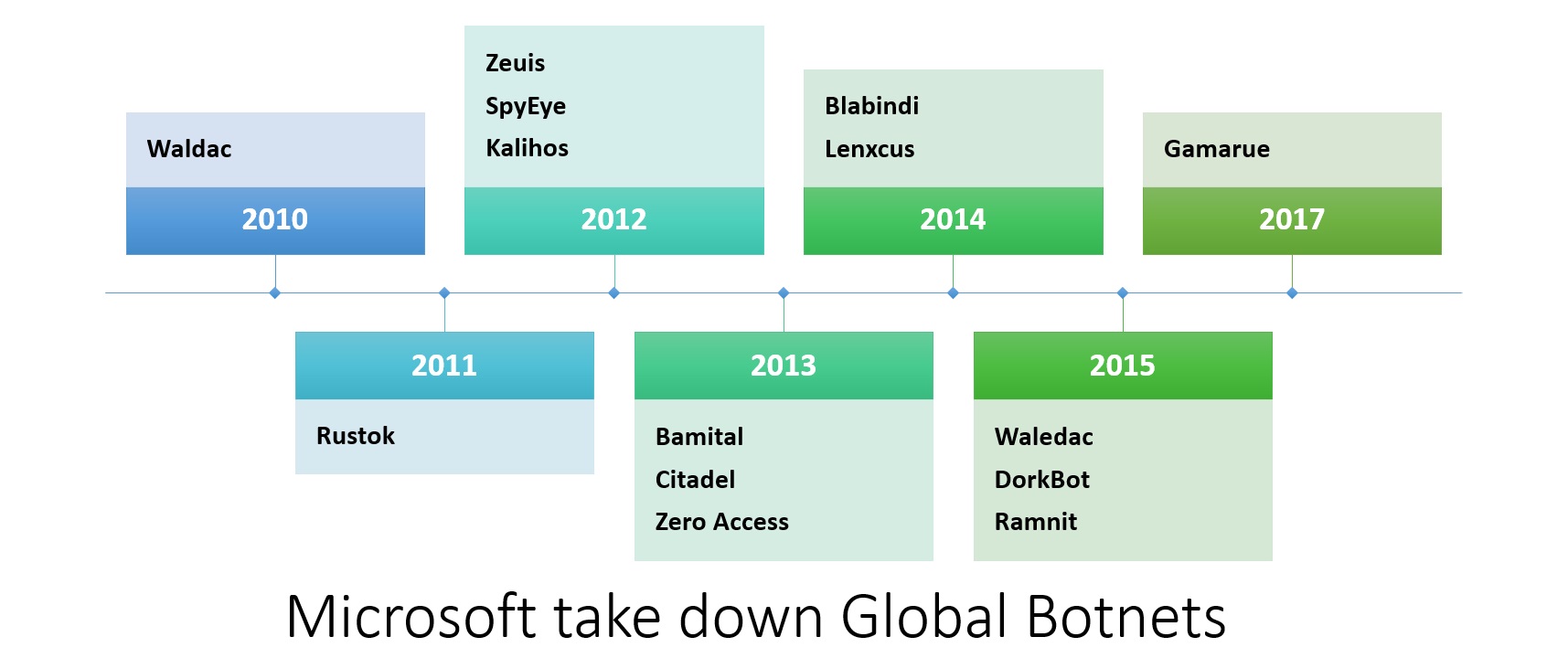
Today, with the immense computing advantages afforded by the cloud, the Machine learning and Artificial Intelligence is finding new ways to use its rich analytics engines and by applying a combination of automated and manual processes, machine learning and human experts, we are able to create an intelligent security graph that learns from itself and evolves in real-time, reducing our collective time to detect and respond to new incidents.