First look on Azure Stack TP2
By now, there are many reviews of Azure Stack TP2 on the public internet. In this article, I would like to provide you some screenshots to give you a better understanding what is the value of running Azure Stack as a service provider. Microsoft Azure Stack (MAS) gives you a lot more compared to some other IaaS + networking focused portals (more services to come in later releases, it is possible to add resource providers today, you can customize it to deliver your unique value for your tenants).
After a successful deployment of TP2 you need to open the console of MAS-Con01 VM, or better to connect with RDP from the POC Hyper-V host to the 192.168.200.6 IP address.
You will find a shortcut ("Microsoft Azure Stack Portal") on the desktop to start the new Portal.
IP addresses and internal DNS names are the same for everybody on the planet, you start here: https://portal.azurestack.local/
This will redirect you to https://login.microsoftonline.com/
Now you need to use admin or tenant kind of (*.onmicrosoft.com) login here. I recommend to start with admin to see more functionality. The account you enter here should be aligned with users you created before the deployment, in my case I use admin@ceetp2.onmicrosoft.com (same as used for the deployment when asked).

First time you need to grant permission to Azure Stack portal to be able to use Azure Active Directory, just hit Accept button.

After successful login, you will start at https://portal.azurestack.local/ 
First thing you will try is to create a new VM. By default, you can do that - there is a Windows 2012 R2 image is waiting for you. Image is not standalone virtual machine, or VMM template, or VM Role (MAS is different from Windows Azure Pack). Azure Stack Marketplace item is the same thing what public Azure is using for a long time. Modern template for VMs and more…


I have HDDs in my lab. When I selected SSD for the VM disk type, VM size was not showing up on the next page.
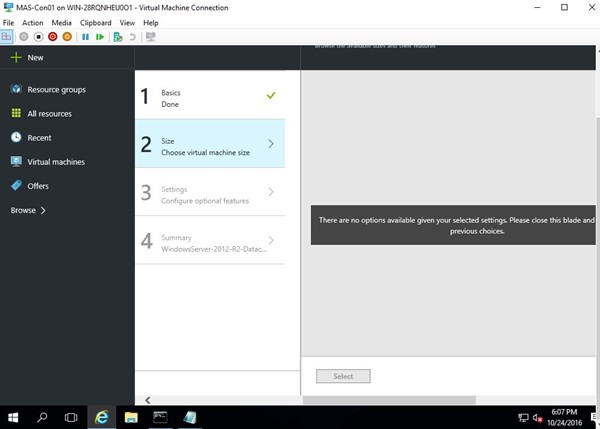
Go back, change to HDD, then it works as expected. Same as Azure with some differences: you will be able to set your prices goes to billing.

Step 3 gives you the full picture of the required objects comes together with a VM in a new resource group.
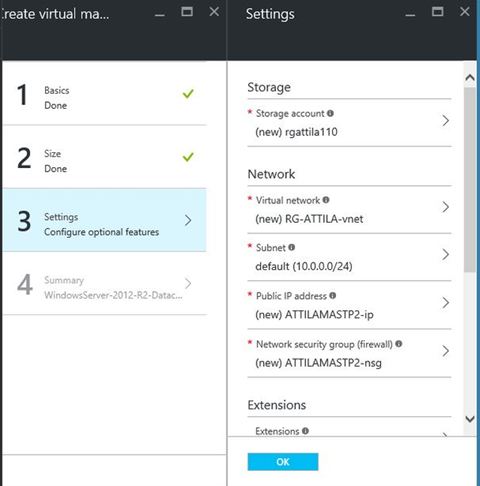

I see extensions and monitoring as a great value added service to position as a service provider in the future for tenants. As you deploy a VM, you will get some additional objects the same time as a gift within the same resource group.

Network interface, Public IP, probably the most interesting is the Network Security Group - virtual firewall - capable of doing many things. By default it is used to connect the VM internal IP address to public IP address by defining NAT (network address translation/port forwarding) rules.
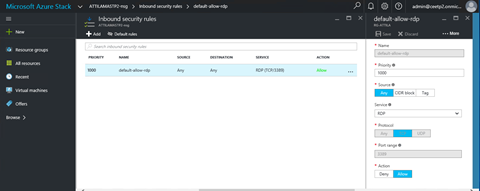
See below the default RDP rule created to access Windows 2012 RDP remote administrative session:
Without getting too much into the details, let me show you my 2 favorite function. Monitoring new and available in TP2. You can customize the look, add more charts, change size, type etc. I am very impressed on this. I used to sell realtime performance monitoring software (and hardware) - and many people confirmed that having a powerful/highly customizable dashboard can make your life a lot easier. An example of a performance monitoring application is Virtual Instruments VirtualWisdom works with Hyper-V as well. Very powerful platform!

I used to develop web applications - see the difference - very few of the chart components works as good as the mentioned ones. Good job on this!

Condition to trigger alters - can send notification e-mails. This is the way to go!

My second favorite is that Azure Stack is not only monitoring the virtualization layer (hypervisor) for CPU, memory, etc. but it has visibility to the operating system as well. Diagnostics gives you insights to the SQL servers, Windows Events, and lot more interesting metrics getting collected here.

GUI speaks only English today, but as Azure already has many languages implemented, I do think that we will have more luck in CEE with some unique languages - not only the ones we have seen in Windows Azure Pack. Nice colors, and I am waiting for more insights how to customize it (white label as XY service provider).

If I compare Stack with Windows Azure Pack I have only one big plus to Windows Azure Pack. WAP offers CONSOLE access to deployed VMs. Azure, and Azure Stack only offers RDP connection to Windows, or SSH to Linux (networking based access). RDP access below (if it is not blocked by any reason within the OS).
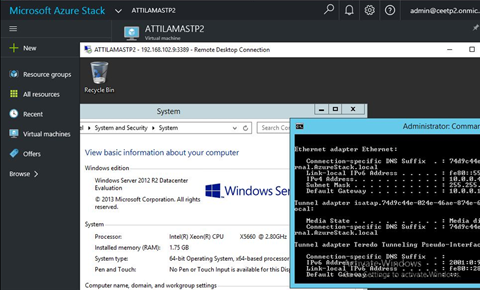
Imagine, that the tenant installs an antivirus blocks RDP. Or misconfigure IP. Or stop SSH or networking services in Linux. Single user Linux, kernel panic, blue screen troubleshooting becomes difficult without having a console. Good news, that we have boot diagnostics: that is a static screenshot of the VM console - this refreshes every X times.

In an ideal world, people does not need the console as all IP pre-configured, none of the operating system crash, etc. See below my WAP screenshot using console access to Hyper-V server:
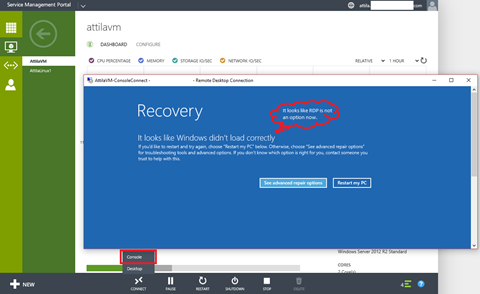
I am too small in CEE to influence Azure/Stack development, but (on behalf of partners) can I have one ask? Please enable the VM console access for MAS, just like in Windows Azure Pack. I hope, this will come in some later versions to both Azure and Stack. I am proud to say that was the only minus after several partner meetings - got very positive feedback - everybody excited and waiting for next releases, news.
In my next blog articles, I will focus on Windows Server 2016 features used by Azure Stack - such as Storage Spaces Direct, new networking stack (with and without Virtual Machine Manager 2016) and Remote Desktop Services (more like for better DaaS not because of MAS). Understating underlying MAS technology is key - simplified deployment and world of appliances comes with people are not able to fix the black box deployments - let's avoid that and learn what those 13 VMs doing for you. Thanks for reading.