Security Filtering, WMI Filtering, and Item-level Targeting in Group Policy Preferences
Hi, I’m Florian, one of the Group Policy MVPs . You may know us MVPs from conferences, seminars, books, Newsgroups and Forums where we voluntarily provide help and guidance to Group Policy and its associated products.
Today, I’d like to write about a feature in Group Policy Preferences you could find useful. Guidance tells us create a GPO (test-drive it) and apply it to an OU; it will then target all objects in the OU.
Question: What if we need to fine-tune GP application to target a subset of the objects in the OU only? Will we need to redesign our whole OU concept?
Answer: Not necessarily, Group Policy brings by default two facilities we can use to adjust our GP application scope: security filtering and item level targeting.
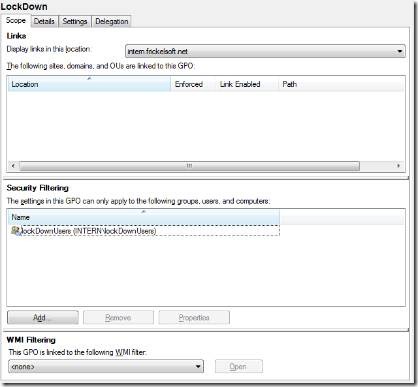
Security Filtering: this is simply tweaking permission on the Group Policy Object for a subset of targets (targets = users and computers in the scope of a policy). Users and Computers need both “Read” and “Apply Group Policy” permission on the object to successfully apply the GPO. If we had a “LockDown” GP that restricts the desktop to a minimum and we would apply that to the “ManufacturingOU”, all objects in that OU would be affected. To only apply the LockDown-GP to a number of targets, we can create an Active Directory group, put the target objects into the group and modify the security filtering settings in the “Scope” tab of the GP as shown in the screenshot:
We remove “Authenticated Users” from the “Security Filtering” tab and add our security group with the targets. Another approach would involve the “Delegation” tab. It lists the correct permissions on the GPO. Clicking the “Advanced” button there, opens the Access Control Editor you may be familiar with from NTFS permissions:
You can see that the lockdown group has “Read” and “Apply Group Policy” permission. Using the ACL editor, you can even put that scenario the other way around: you leave “Authenticated Users” in the list of allowed groups and users and deny a specific group both “Read” and “Apply Group Policy” permission to prevent them from applying the GPO.
WMI filtering: you can further filter the scope of a policy by applying a WMI filter on the GPO. WMI filters are run prior to executing the GPO in question. If the filter evaluates to “TRUE”, the GPO is applied, otherwise it is ignored. A classic use case for this is GPOs for different operating systems. Right-click the “WMI filters” node in GPMC and create a new WMI filter with WQL syntax. An example for targeting Windows Vista would be:
SELECT Version, ProductType FROM Win32_OperatingSystem WHERE Version >= ‘6.0′ AND ProductType = ‘1′ .
After that, open the “Scope” tab of the GPO in question and choose the Vista-WMI-filter in the “WMI filters” section. The GPO will only be applied on Vista machines then as only on those machines the filter evaluates “true”. Obviously, you need to know how to create WQL queries. A great help on putting WQL queries together is the Scriptomatic: https://www.microsoft.com/downloads/details.aspx?FamilyID=09dfc342-648b-4119-b7eb-783b0f7d1178&DisplayLang=en .
So now that we have Group Policy Preferences, there’s another way of filtering the policies on the targets. It’s called “Item-level targeting”. As the name implies, you can now go define filters for every setting you configure in GP Preferences. You read right: for every setting. Security Filtering and WMI filtering were used to filter per GPO – item level targeting is per setting. That allows you to have a GPO with multiple GP Preference items configured but have only a subset of them applied based on filters and their evaluation. Where you would add these filters? Check the “Common” tab of a GPP:
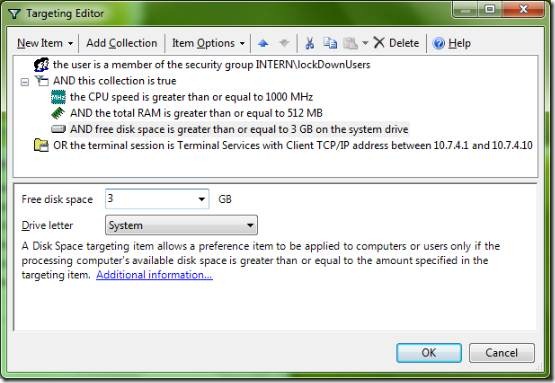
You need to tick the “Item-level targeting.” checkbox to enable the button. Once you open “Targeting…”, you see the following editor:
I’ve already opened the “New Item” menu for you so you can see all the options in GPP you can filter for. That’s right, you can filter a GPP item (within a GPO with other GPPs and GP settings) to only apply if – say… the user is in the Security Group “Help Desk” and the Computer Name is “XP-00233”, it is between 8 AM and 5PM (Time Range) and the user is on a Terminal Session with a specific session name on Windows XP as the Operating System and has 20GB free Disk Space on the System partition. Well, theoretically, you can. If that’s actually useful, that’s up to you.
The item-level targeting editor allows you to form filters based on the “New Item” criteria shown in the screenshot. You can use Boolean logic (AND, OR, IS NOT) to combine filters for even complex logics:
Where ever you can enter strings into text boxes, you can hit F3 to get a list of known environment variables GPP understands. That makes it easier to (for example) create file match rule as you can use the “CommonAppDir”, “CommonStartUpDir” or simply the “ProgramFilesDir” variables the local system will translate into the actual path.
Think about the configurations you could use in a single GPO with item-level targeting on different settings defined – just for a second:
- Create multiple GPP mapped drives in one GPO and have them apply based on Group membership (easier than scripting!)
- Have different GPPs applied to targets depending on what time it is (working hours vs. non-working hours!)
- Create and deploy different printers/shortcuts/files depending on the user’s site or IP address
- Apply GPP on a given date in a certain time range.
- Copy files based on the user’s language.
Now what do you say? Worth a look, huh?
Florian Frommherz is a systems engineer from Germany working in Switzerland. Specialized in Windows environments, Florian helps customers design their Directory Services and Group Policy implementations to unleash the central management capabilities. Read more of his advice on the Group Policy TechNet forum.
Comments
Anonymous
August 02, 2009
is there anything in the works to replace GPO security filtering and WMI filtering with item-level targeting? Item-level targeting is leap-years ahead of security and WMI filtering.Anonymous
August 04, 2009
Rick, as I noted above, there's a difference between what ILT and what security filtering target. ILT is on item-level whereas security filtering does filtering on GP level. Having something like ILT for GPOs - I assume you think of this as having a GPO and then creating a filter to specify machines/user that shall apply the GPO across the domain - isn't possible yet. That would be a complete change to how GP works now. One would have to move away from the target<->OU<->GPO relation that exists today. That definitely good feedback for the team to hear! FlorianAnonymous
August 06, 2009
WMI query filtering has been known to influence performance. I guess this is still the case.Anonymous
August 11, 2009
We use Group Policy Preferences in our lab-forest, which provides the latest workspace technology to users in our main-forest. However we now see that ILT only allows for security groups in its own domain/forest. On a GPO in the lab-forest, we are not able to do ILT against a security group from the main-forest. Is this a bug or a feature? Regards, KevinAnonymous
August 24, 2009
is there any commands or scripts to specify groups or users used for security filtering in a GPO through command prompt