Understanding workstation analysis, under the hood
When you connect UAG, in an internal phase called “install and detect” the UAG client will download from the UAG server a file named Detection.VBS.
This Detection.vbs file contains all the “VBS” code that will analyze the client machine. This file is located in the InternalSite directory of the UAG Server.
You can’t modify it (otherwise you will break it, since this file is “signed” by Microsoft for security reasons) but can edit it in order to see how it works, and how UAG gather such and such information.
ð In another post I will explain how to “add” your own script part of the global process in order to perform checks that may be important for you.
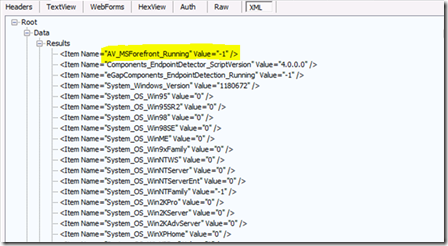
As soon as this VBS is downloaded on the client machine, it is executed in the security context of the UAG client. It will gather all the information, and create a “result” file… sort of XML files that contains 1 line per check, each line contains the name of the variable (that you will use later in your security policy) and its value. For example “AV_MSForeFront_Running=TRUE”.
Once this XML file is created it is sent by the UAG client back to the UAG server (via Internalsite/Setpolicy.asp), and then will be kept in memory by UAG. This analysis is linked to the user’s session. Here is an extract of a trace that shows that “XML” file sent via an HTTP POST (captured via Fiddler) :
All the +200 checks will be in this XML file.
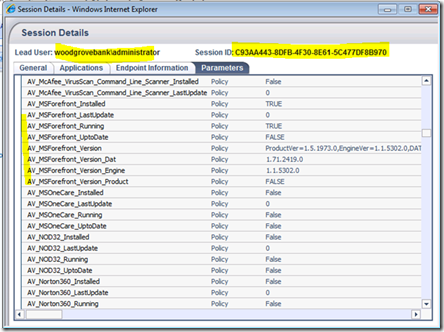
Now UAG has associated for a “session” a list of checks. You can verify this running the UAG Web monitor on the UAG server:
At this level, every time this user is “asking” something, UAG will use that methodology:
· User ask to do a specific action: for example and read an attachment.
· UAG checks if a security policy is associated with this “action”: for example FCS must be running.
· If there is a security policy for this action, UAG will compare the security policy with the workstation analysis :
o If compatible: you can do this action
o If not: user gets an error message, explaining the problem, and “error” is also tracked.
It is also important to notice that UAG client is also able to gather information via the Windows Security Center. In the XML file you will find variables such as “AV_WMI…”. They contain information exposed via WSC. As a result of that, as soon as a “security product” can register himself in WSC, UAG can detect it without a line of code.