Slipstreaming a Client Security client installation
As I mentioned in my previous blog posting, there have been several updates to the FCS antimalware client since its release. Through traditional deployment methods you will install the release to manufacturing components(RTM) of the FCS client which has no updates and extremely limited detection capabilities. At installation, the client has the base 1.0.0.0 antimalware definitions. Immediately after the installation it will use the Windows Update API(WUA) to attempt to download the current definitions from either your WSUS server or Microsoft Update(whichever it is configured for). During the next Automatic Updates cycle it will download the latest antimalware update(currently KB956280) and install it.
At the time this posting was made Microsoft has not published an updated FCS client package to WSUS (although it is being considered) or revised the CD media available for download. Therefore, if you choose to deploy the FCS client via WSUS or the CD it will go through the above RTM installation and then subsequent update.
If you are doing a manual, scripted, or System Center Configuration Manager/SMS/similar style of deployment then you can update the antimalware client installation package to install the latest version, instead of the RTM. You can do this through the following steps:
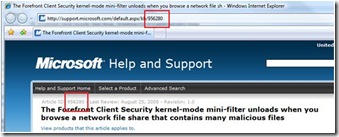
1. Determine the latest version of the antimalware client. This link points to the KB article https://go.microsoft.com/fwlink/?LinkId=125926 for that version
(above the article number is 956280)
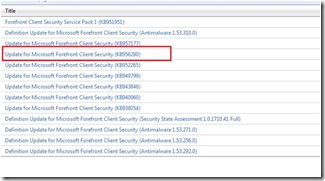
2. Visit the Microsoft Update catalog and query for “Forefront Client Security” https://catalog.update.microsoft.com/v7/site/Search.aspx?q=forefront%20client%20security
3. Add the appropriate language of the KB from Step #1 to your basket and download (both x86 and x64 will be included).
4. Extract the contents from the update package
- Open a command prompt
- Change directory to the download location
- Run the executable with a /extract switch for each package:
>all-fcsam-kb956280-x64-enu_1dfb1029721f86ea98674400ffcb5cba629d0bc8.exe /extract - In the dialog presented, enter a temporary directory
5. Locate the mp_ambits.msi file in the temporary directory extracted contents
6 . Copy the entire client directory from the CD media (including the MSI files, KB914882 installers, and the x64 subdirectory) to the deployment location(typically a file share)
7.Replace the mp_ambits.msi in the deployment location with the extracted copies of both x86 and x64 in their respective \client and \client\x64 directories
Using this method will deploy a slipstreamed FCS antimalware client; however, that client will still have the base 1.0.0.0 definitions and invoke a WUA download of definitions at installation completion. This download cannot be prevented in the current version of the FCS product. If you were scripting an installation and did not wish this WUA download to occur, you might disable network connectivity or temporarily stop the Automatic Updates service and use a standalone definition update installation. The standalone definition installers are also available from the Microsoft Update catalog website shown in the screenshot above as well as through links off of the MMPC portal and KB938202.
Thanks,
Craig Wiand
Forefront Client Security Escalation Engineer
Comments
- Anonymous
January 01, 2003
Hello folks! I'm happy to share with you another wonderful post from our friends over at the FCS CSS