Claims based Identity & Access Control Guide – Updated drafts & samples available
Yesterday, we uploaded a new release of the Guide and the samples. You can download the content from here. (Note: if you downloaded them yesterday, you might want to check again. We mistakenly uploaded the samples with no docs. It is fixed now).
You’ll find:
- Updated introduction & WebSSO chapters, incorporating quite a bit of feedback
- New updated samples, including scenario #2 (Federation with Partners). This is inspired in this article I wrote some time ago.
Getting started with the samples:
Just download the zip file, expand somewhere in your disk. There’s a readme.htm with some very basic instructions and prerequisites.You’ll have to run StartHere.cmd batch file with elevated privileges (this essentially installs necessary certificates). Open the solution (as admin), compile and run.
Prerequisites haven’t changed:
- Visual Studio 2008
- IIS (for HTTPS)
- WIF
There are 2 scenarios folders now: scenario #1 (WebSSO), which is the same we published a couple of weeks ago. Then there’s the new one that shows federation between Adatum’s a-Order and Litware.
The first time you open Visual Studio, it will create some new web sites for you.It might happen that those websites already exist from previous drop, you might want to delete them beforehand if you expand the files in a different location.
Make sure the default app is “Litware Portal”:
This is the launching point for the application from Litware’s perspective.
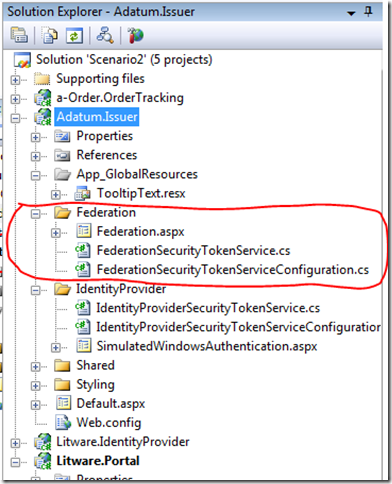
The major changes from the code in Scenario #1 is that now Adatum.IdentityProvider has been extended to other things, namely manage the trust relationship between Adatum and Litware. That’s why we now call it Adatum.Issuer. This new functionality includes transforming claims issued by Litware into claims understood by a-Order. All this is happening in the FederationSecurityTokenService class.
Adatum.Issuer is a “mock” STS and its implementation is no more and no less than what is strictly needed for the sample to work. In the real world you would replace it, as we did in our test Lab, with a real/production quality issuer such as ADFS v2.
The transformation rules in our mock STS are trivial and are all implemented in the GetOutputClaimsIdentity method override:
protected override IClaimsIdentity GetOutputClaimsIdentity(IClaimsPrincipal principal, RequestSecurityToken request, Scope scope)
{
var outputIdentity = new ClaimsIdentity();
if (null == principal)
{
throw new InvalidRequestException("The caller's principal is null.");
}
var claimsIdentity = (ClaimsIdentity) principal.Identity;
var issuer = claimsIdentity.Claims.First().Issuer;
switch (issuer)
{
case "litware":
ProcessClaimsFromLitwareIssuer(claimsIdentity, outputIdentity);
break;
default:
throw new InvalidOperationException("Issuer not trusted.");
}
return outputIdentity;
}
The samples contain a number of annotations and hints here and there to explain what is happening. Make sure you hover with the mouse over this little information icon to get extra context:
This is still under development of course, so expect quite some changes. But we hope you’ll find it useful anyway. Feedback is very much welcome as always.
Very special thanks to the following people for their extensive feedback and suggestions for this Guide:
Mario Szpuszta, Pablo Cibraro, Travis Spencer, Mario Fontana, Jason Hogg, Michele Leroux Bustamante, Pedro Felix.