BitLocker in Windows Embedded Standard 2011
In this blog article I will be talking about a new security feature in Windows Embedded Standard 2011 (“Quebec”). This security feature has been part of Windows Operating System since Vista timeframe. I will touch upon the usefulness of this feature. The main idea of this article is to go over the procedure of adding this package to your image and using it afterwards.
BitLocker in Windows Embedded Standard 2011 – Overview
Windows BitLocker Drive Encryption (BitLocker) is a new security feature that provides better data protection for your device by encrypting all data stored on the Windows Embedded Standard 2011 operating system volume. BitLocker allows an admin of a machine to encrypt volumes to protect data contained on them.
A Trusted Platform Module (TPM) is a microchip that is built into a device. It is used to store cryptographic information, such as encryption keys. Information stored on the TPM can be more secure from external software attacks and physical theft.
BitLocker has three possible modes; two need a TPM and a compatible BIOS, the 3rd does not require a TPM.
1. TPM only: BitLocker uses the TPM to provide a transparent user experience. The machine boots, and the user logs on as normal. The encryption key for the drive is stored in the TPM and only given to the boot loader if the boot files and BIOS have not been tampered with.
2. TPM + Token: The user needs to provide some additional authentication to the TPM/OS Loader - either a PIN entered manually at each boot or a USB key.
3. USB Key: BitLocker can also be used without a TPM. When BitLocker is used without a TPM, the required encryption keys are stored on a USB flash drive that must be presented to unlock the data stored on a volume.
Other points to note: BitLocker can be controlled via Active Directory (AD) as well. In this case, AD schema must be extended to support this. To control TPM recovery from AD, permission on computer class object in AD must be changed. To back up recovery information for TPM and BitLocker on AD, you will need to enable “Turn on BitLocker backup to Active Directory Domain services” via group policy management console.
Pre-requisites for BitLocker
BitLocker requires the user’s computer to be configured with at least two partitions. Partition A (the system partition) contains boot critical files and must remain unencrypted. All other partitions may be encrypted by Bitlocker.
System partition is a small 100MB partition that will co-exist with OS partition. To create this small unencrypted partition, the user could use diskpart (or disk preparation tool). This volume must be different than the OS volume.
If you add BitLocker package via IBW, this 100MB system partition is automatically created by IBW.
Adding BitLocker to your image
We realize that Windows Embedded customers care a lot about the amount of disk space their image requires. The small unencrypted 100MB partition is added to the Windows Embedded Standard 2011 image only to better support BitLocker. Hence, by default, your image will not create this system partition unless the BitLocker package has been selected to add to your image.
You could add BitLocker to your image when running Image Builder Wizard IBW setup or to your answer file created using Image Configuration Editor (ICE).
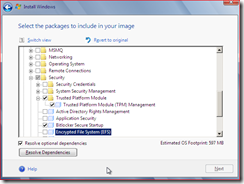
The screenshot below shows the packages you need to select when building an image using IBW
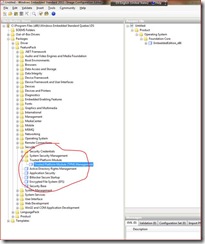
Screenshot below shows the packages you need to select when creating an answer file using ICE.
Enable BitLocker
BitLocker can be enabled one of the two ways – via command-line interface (CLI) or via GUI. You can use Windows Management Instrumentation WMI classes to manage either way. Also, you can write WMI scripts to manage BitLocker and TPM. This approach is especially useful in cases of headless devices (devices that don't have display output).
For more information on the WMI provider classes, please click on the following links:
· To manage BitLocker – https://msdn.microsoft.com/en-us/library/aa376483(VS.85).aspx
· To manage TPM - https://msdn.microsoft.com/en-us/library/aa376484(VS.85).aspx
Again, when enabling BitLocker, there are two main scenarios to consider. Both of those scenarios are outlined below.
1. Enabling Bitlocker on hard drive.
a. BitLocker with TPM (note that BitLocker requires TPM chip 1.2):
- Verify that all TPM drivers are loaded; Ensure that TPM is enabled in BIOS before running setup of Windows Embedded Standard 2011;
- Initialize TPM (either using WMI scripts or Microsoft Management Console MMC snap-in);
- Take ownership of the TPM;
- Save the TPM key (AD could be used to back up this TPM recovery information); and Now run manage-bde on the hard drive to turn on Bitlocker
b. BitLocker without TPM:
- Run manage-bde to turn on Bitlocker
2. Enabling Bitlocker on USB drive
This is the same as turning BitLocker on for the hard drive – when running manage-bde, you can specify the disk you want to encrypt via BitLocker. Run Manage-bde with “-status” switch to check status of various drives available and their corresponding encryption status.
BitLocker To Go (BTG)
Loss of confidential data via a removable drive costs the industry and governments billions of dollars every year, not to mention the resulting inconvenience. Windows Embedded Standard 2011 includes a new feature known as BTG that provides the ability to encrypt removable storage devices, such as USB drives, making sure the data is secure in case the device is lost or stolen. BTG encrypted drives can be unencrypted using a password, smart card or specific machine automatically. IT administrators can configure policy that mandates BTG encryption to grant write access to a removable disk.
Using BTG is really easy. Once your USB device is inserted and has been recognized by your device, go to the control panel and access BitLocker Drive Encryption.
Screenshots below are examples of enabling BTG when inserting a USB flash drive.
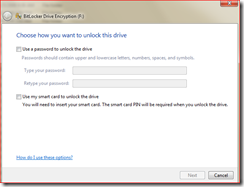
Once you insert the USB flash drive, go to the explorer shell and right click on the USB drive (F:\, for example) and select “Turn On Bitlocker”. You will get a screen as shown below:
At this point you could select a method to unlock this drive post encryption. I select password to unlock drive.
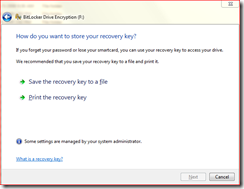
I get the next screen.
Here I can either save the recovery key to a file or print the recovery key. I recommend saving it to a file, which is more secure than printing it.
Browse to a location you want to save this key and then start encrypting.
- Hema