EFS - “Element not found” error
Hello
It’s Rafal Sosnowski from Microsoft Dubai Security PFE Team. Today I will troubleshoot with you one error related to EFS (Encrypting File System).
EFS (Encrypting File System) is a component of the NTFS file system present in Windows starting from Windows 2000. EFS enables transparent encryption and decryption of files by using advanced, standard cryptographic algorithms. EFS uses hybrid cryptography: symmetric key is used to encrypt data; asymmetric key is used to protect the symmetric one. To take advantage of asymmetric cryptography EFS uses certificates: self-signed or issued by Certification Authority (CA).
To encrypt the file just right click on it, select Properties> Advanced > Encrypt contents to secure data

On rare occasion when we try to encrypt file or folder, we might get an error “An error occurred applying attribute to the file: Element not found”

Troubleshooting:
So let’s start with enabling verbose EFS\Debug log in Event Viewer. Go to the Eventvwr.msc and select Application and Services Logs > Show Analytic and Debug Logs. This will add dozens of new and very interesting logs to your MMC, including EFS\debug log.
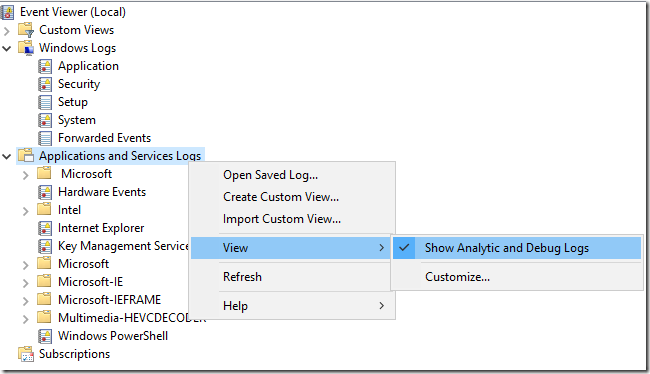
Enable EFS\Debug log and try to encrypt file again to reproduce an error.

Instantly in the log we will see repetitive errors:
event 277: try and locate the matching key based on cert hash
event 1: An API call failed at 2.93. Error code: 2148081668
2148081668 translates to - CRYPT_E_NOT_FOUND
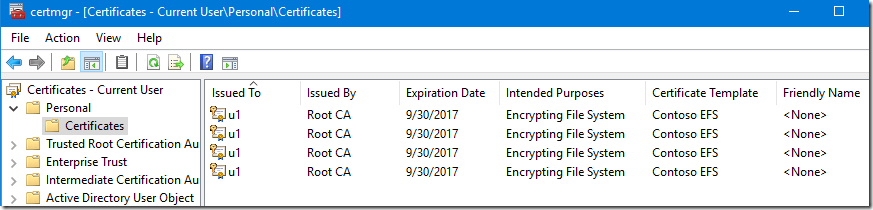
So at the first glance it looks like certificate or proper private key cannot be found. However, when we look at the personal store using command certmgr.msc we see that multiple EFS certificates are delivered from Certification Authority:
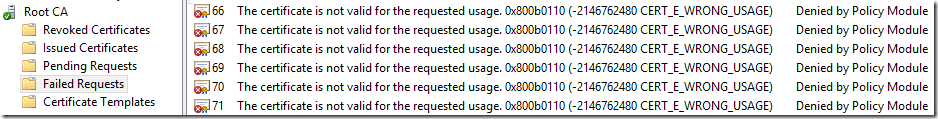
Note: when you don’t see certificate delivered to the user personal store, you can take a look at “Failed Requests” container on the CA server to verify why the certificate request was denied:
In our case certificate was successfully issued and delivered by the CA. Moreover we got more than one certificate because File Properties UI cannot find proper certificate and send additional requests to the CA.
Now verify our certificate in the user store using command:
Certutil – verifystore -v -user my
Among the lines we see that certificate has been issued with next generation cryptographic provider called Key Storage Provider (KSP) and public/private key pair has been generated with RSA algorithm. The problem is that EFS doesn’t support keys from KSP based on RSA.
Provider = Microsoft Software Key Storage Provider
ProviderType = 0
Unique container name: a58f5c5c98486fdb30e11dee7877ce02_042a9558-f6ac-4d95-a6ab-6e99a8c2e2a7
RSA
UI Policy = 0
CERT_KEY_PROV_INFO_PROP_ID(2):
Key Container = te-ContosoEFS-cc8788c8-f9bc-4ab1-a784-7266cb7cb673
Unique container name: a58f5c5c98486fdb30e11dee7877ce02_042a9558-f6ac-4d95-a6ab-6e99a8c2e2a7
Provider = Microsoft Software Key Storage Provider
ProviderType = 0
Flags = 0
KeySpec = 0 -- XCN_AT_NONE
EFS will work with keys generated from KSP based on Diffie-Hellman Algorithm (ECDH):
Provider = Microsoft Software Key Storage Provider
ProviderType = 0
Unique container name: b0e837b6acbbb65ddf5142a288e107ef_042a9558-f6ac-4d95-a6ab-6e99a8c2e2a7
ECDH_P521
ECDH
UI Policy = 0
CERT_KEY_PROV_INFO_PROP_ID(2):
Key Container = te-ContosoEFS-42d4a65d-e55f-411d-9f8e-a026bbbabcd3
Unique container name: b0e837b6acbbb65ddf5142a288e107ef_042a9558-f6ac-4d95-a6ab-6e99a8c2e2a7
Provider = Microsoft Software Key Storage Provider
ProviderType = 0
Flags = 0
KeySpec = 0 -- XCN_AT_NONE
Also EFS will work fine with keys generated in legacy cryptographic providers (CSP) and using RSA algorithm.
Provider = Microsoft Strong Cryptographic Provider
ProviderType = 1
Simple container name: te-ContosoEFS-2adf345e-263e-490a-af3b-d1a86ce54018
RSA
PP_KEYSTORAGE = 1
CERT_KEY_PROV_INFO_PROP_ID(2):
Key Container = 4d85da42c5c12b17ccd2c4833db0e856_042a9558-f6ac-4d95-a6ab-6e99a8c2e2a7
Simple container name: te-ContosoEFS-2adf345e-263e-490a-af3b-d1a86ce54018
Provider = Microsoft Strong Cryptographic Provider
ProviderType = 1
Flags = 0
KeySpec = 1 -- AT_KEYEXCHANGE
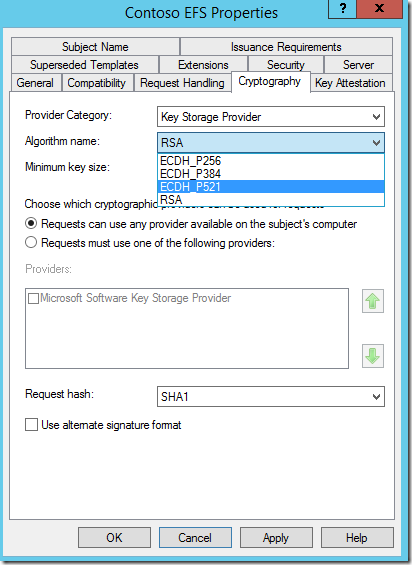
So where shall we configure proper cryptographic providers and algorithms for EFS? The answer is of course on the certificate template. Remember don’t select RSA while Key Storage Provider is your cryptography provider or you will face “Element not found” error.
Hope this was informative for you and happy encrypting!
Comments
- Anonymous
March 22, 2019
Hi Rafal,Thanks for the good post. Looks like I can ask you for a small advise related to EFS.I am trying to enable Encrypting File System (EFS) on almost 4.5 Terabyte of FileStream data . 4.5 Terabyte of FileStream data consists of 7 SQL Server Databases . Each Database consists of almost 700 GB of Blob data folder each.While applying the EFS on each of the 7 Blob folders with 700 GB each , I am getting below error :"The process cannot access the file as it is being used by another process" . It is very tough for me to identify WHAT IS THE PROCESS that is using the file in the background. I am using Resource Monitor , Process Monitor and Task Manager to identify which process is using the file. Cannot find anything so far . Please do help me on this issue .