Claims Based Authentication – Part III
This is continuation of two previous posts. Please check them out first, otherwise this one might not make much sense at all.
Step 6 in step-step guide configures Fabrikam STS with Relying Party and shows how to configure Information Cards to automate home realm discovery. I’m not going to talk about Information Cards yet, for now we stick with STS configuration and claims flow.
Afetr the RP for Contoso STS was created we configured three claim rules. The first rule is using AD as the directory source. It should be easy to predict the mappings in this rule. Just take a look back at how Fabrikam IDP on Contoso STS was configured. It expects certain type of incoming claims. This rule has the following mappings:
| LDAP Attribute | Outgoing Claim Type |
| E-Mail Address | |
| tokenGroups | Role |
This could be configured to just send this claim out to the relying party, but it was not. Fabrikam STS Administrator decided to provide some extra checks and only send out claims that match certain criteria.
The following table shows two new rules:
| Rule # | Rule Type | Incoming Claim Type | Pass Through All Claim Values | Pass Through only a specific Claim Value | Pass through only claim values that end in a specific value | Pass through only claims that start with specific value |
| 1 | Pass Through Incoming Claim | E-Mail Address | Yes | |||
| 2 | Pass Through Incoming Claim | Role | DrugTrial1Auditors |
The first rule will pass any E-Mail Address claim, but the second rule will filter out all claims that do not have DrugTrial1Auditors in its value.
At this point users from Fabrikam are ready to access Contoso SharePoint site.
What is the single qualifying requirement for Fabrikam user to get access to the Contoso site? Fabrikam user must be member of DrugTrial1Auditors Active Directory group.
Lets examine the entire authentication flow for Fabrikam user. Figure 1 provides steps in this process.
Figure 1. Authentication by Fabrikam user to Contoso SharePoint site
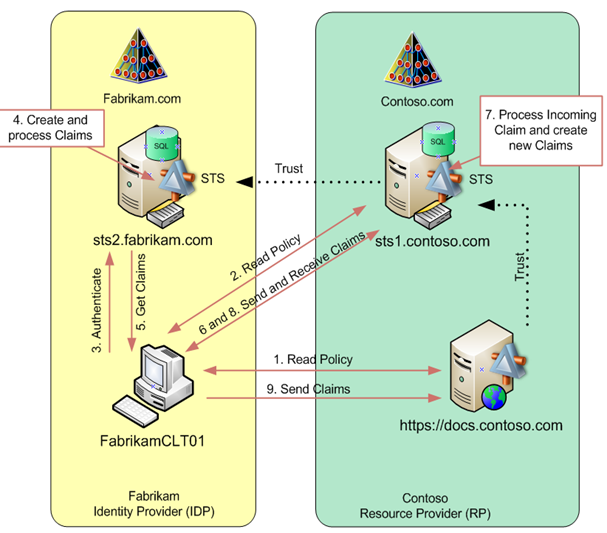
Fabrikam user Frank Miller will access Contoso SharePoint site.
In step 1, Frank opens his browser and opens https://docs.contoso.com site. SharePoint site will provide its policy information a redirect Franks browser to a trusted STS.
In step 2, Franks browser will access https://sts1.contoso.com and reads its policy. At this point Frank must select his home realm. If Information Card was already configured in Fabrikam forest for Contoso SharePoint site, the home realm discovery would automatically redirect his browser to his home STS. Without Information Card, he would be required to choose his STS server in the drop down list. At this point no claims yet have been exchanged and all authentication been done via anonymous authentication mechanism.
In step 3, Franks computer will authenticate to the STS. Since our STS is running on the same computer as Domain Controller, it is already authenticated to it, so it just presents existing Kerberos ticket, which will have all required information in it, such as list of groups this user belongs to (list of SIDs of those groups).
In step 4, Fabrikam STS will create and process new claim for Frank Miller. The first rule will create the following claim:
| Outgoing Claim Type | Claim Value |
| E-Mail Address | frankm@fabrikam.com |
| Role | DrugTrial1Auditors Purchaser Domain Users |
Next, it will pass this claim onto second and 3rd rules. Second rule allows to pass all claims with any E-Mail Address. 3rd rule will check value of the Role claim type and it will discard 2 values out of this claim. The final outgoing claim from Fabrikam STS for user Frank Miller should have the following information:
| Outgoing Claim Type | Claim Value |
| E-Mail Address | frankm@fabrikam.com |
| Role | DrugTrial1Auditors |
In step 5 this claim is delivered back to Franks computer.
So now Frank has his claim from Fabrikam STS. Can he present this claim to Contoso SharePoint site? It would not work because Contoso SharePoint site does not trust Fabrikam STS, it only trusts Contoso STS and it would accept claims only from Contoso STS.
In step 6, Franks computer will deliver his claim to Contoso STS.
Now it is up to Contoso STS to evaluate incoming claim and decide what to do with it. In step 7, Contoso STS receives incoming claim from Fabrikam STS and it will pass it onto Fabrikam IDP rule set configured on Contoso STS. If you remember, those rules will evaluate incoming claim values and will pass claims only if their E-Mail Address value ends with @fabrikam.com and its role value is equal to DrugTrial1Users. Incoming claim from Frank satisfies both criteria. At this point Contoso STS accepted incoming claim, it is not going back out yet to the user computer. The value of this claim should be the same:
| Outgoing Claim Type | Claim Value |
| E-Mail Address | frankm@fabrikam.com |
| Role | DrugTrial1Auditors |
Next, it will pass this claim onto Relying party rule set to create outgoing claim suitable for the SharePoint. Contoso SharePoint RP is configured with two rules for incoming claims. First one will pass Role claim type without any changes to its Role type. Second rule is a transformation rule. It will change the E-mail Address claim type to Name claim type, but will keep its value the same.
The final claim for Frank Miller, coming out from Contoso STS destined for SharePoint RP should look like this:
| Outgoing Claim Type | Claim Value |
| Name | frankm@fabrikam.com |
| Role | DrugTrial1Auditors |
In step 8, this claim is send back to Franks computer, in step 9 it is delivered to Contoso SharePoint site. SharePoint site will authenticate Frank Miller (frankm@fabrikam.com) at gives him appropriate rights configured for Role#DrugTrial1Auditors. Just like that simple and easy.
In next post we’ll look at how role membership information can be outsourced to SQL database.