Understanding Forefront Client Security Fix 940060
A new fix has been released for FCSv1in how the system handles Overrides and “Ignore” vs “Ignore Always”. The associated KB article describes the details, but this fix changes a basic functionality of FCSv1 from the admin and end-user perspective, so we wanted to provide some extra guidance to help customers understand what the fix means and how it will affect them.
Impact #1: End-User notification when allowing an application that is blocked by default
First, the scenario in which this applies is when you have selected Ignore in the Overrides tab in a Client Security policy for a specific application that would by otherwise be blocked by default through the FCS antimalware signatures.
Before the fix
If an end user launches the application you have set to Ignore, then the end user will receive a notification despite the administrator having selected Ignore.
OK, so this is obviously not correct. The administrator chose Ignore for the application, and yet clearly the FCS client is NOT ignoring it.
What does the end user see exactly?
- Notification pops up to informing the end user that the particular application has been ignored
- FCS icon will go red
Why is this bad? The above behavior would result in a help desk call to the administrator.
After the fix
When an end user launches any application that has been configured to Ignore, application launches and end users do not get notified. This is Goodness, The FCS client behaves exactly like the administrator configured it to.
What does the end user see exactly? Nothing (which is what is desired)
- No notification will be seen
- FCS Icon will not change color
Impact #2: Change in the override model
Before the fix
In the Overrides tab in Client Security policy, you can do these things:
- Be more restrictive or less restrictive for specific applications
- Be more restrictive or less restrictive for a category of applications.
More restrictive = you want to block more than what the default behavior would be.
Less restrictive = you want to block less than what the default behavior would be.
After the fix
In the Overrides tab in Client Security policy, you can do these things:
- Be less restrictive for specific applications.
- Be more restrictive or less restrictive for a category of applications.
In other words, we removed a feature. You can no longer be more restrictive for a specific application. Specifically, you can no longer select Remove or Quarantine for specific applications.
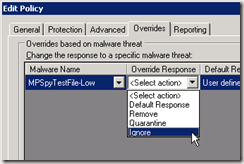
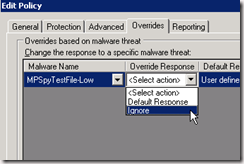
Here how the UI changes:
Policy Dialog Before
Policy Dialog After
By removing this feature for specific applications, we have moved to a pure ”whitelist” model for applications.
Why we did this:
- Moving to a “whitelist” model for specific applications covers the vast majority of customer needs in practice.
- We believe the change makes it simpler to understand what the UI is doing, and as a result simpler to predict the impact on end users.
- Most importantly: it now accurately explains what the FCS client will do. Before the fix, there were situations in which the FCS client behaved inconsistently with respect to what the Client Security policy said; after the fix, the two are consistent.
In general we do not like removing a feature, because that’s just rude. But in this case, the feature caused more problems than it solved. And our job is to make sure your problems are solved, not make new ones.