How to make use of a custom IP-STS with SharePoint 2010? (Part 2)
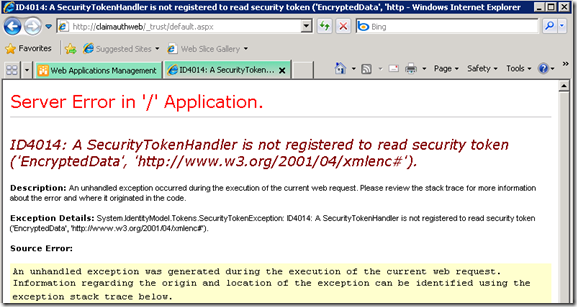
ID4014: A SecurityTokenHandler is not registered to read security token ('EncryptedData', 'https://www.w3.org/2001/04/xmlenc#').
Here comes the answer of the little quiz in the end of Part 1.
When I clicked SimplePassiveSTS, I was redirected to the sign-in page of my STS, which was what I want.
But when I signed in and was redirected back to the SharePoint site, I saw what I didn’t want. It ended up with an exception of WIF, ID4014: A SecurityTokenHandler is not registered to read security token ('EncryptedData', 'https://www.w3.org/2001/04/xmlenc#').
From the description of the exception, it looks like SharePoint does not know how to handle the security token sent from my STS because of no corresponding SecurityTokenHandler registered. So what SecurityTokenHandlers does SharePoint load by default?
By examining the web.config of the web app and debugging into the process, the following 3 SecurityTokenHandlers were loaded by default:
-
Microsoft.IdentityModel.Tokens.X509SecurityTokenHandler -
Microsoft.SharePoint.IdentityModel.SPSaml11SecurityTokenHandler -
Microsoft.SharePoint.IdentityModel.SPTokenCache
But the security token issued by Asp.Net STS was generated by Microsoft.IdentityModel.Tokens.Saml11.Saml11SecurityTokenHandler and encrypted by Microsoft.IdentityModel.Tokens.EncryptedSecurityTokenHandler. By consulting other colleagues, it looks like SharePoint 2010 cannot handle the encrypted security token by default.
A simple solution: stop encrypting.
To verify whether the exception ID4014 was caused by the encrypted security token, a simple way is to stop encrypting the token in the STS. In Asp.Net STS, just leaving the value of the following app setting empty will stop encrypting the token.
<add key="EncryptingCertificateName" value=""/>
This setting is handled in GetScope function of the STS. If it is empty, scope.TokenEncryptionRequired will be set to false. Hence, the token will not be encrypted anymore.
After stopping encrypting, I could see the access denied page of SharePoint after I was redirected back from the STS site. It was expected because I didn’t give the user identity from the STS any permission to the site yet.
Another solution: making SharePoint be able to handle encrypted security tokens.
Let us go one step further. What if a custom STS has to send an encrypted security token?
According to my testing, by adding the following settings in the web.config of the web app, we can make SharePoint be able to handle an encrypted token.
- Add EncryptedSecurityTokenHandler:
<add type="Microsoft.IdentityModel.Tokens.EncryptedSecurityTokenHandler,
Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" />
- Add the encrypting certificate information:
<serviceCertificate>
<certificateReference x509FindType="FindByThumbprint"
findValue="2E00D604A5DA08B2C212B0533D38F4646F314255"
storeLocation="LocalMachine" storeName="My"/>
</serviceCertificate>
- Export the encrypting cert from the STS server and import it to SharePoint.
For testing purpose, this way works. But if you want to use this way in the production, I think the good practice is to create an encrypting cert for SharePoint to decrypt security tokens and make use of this cert in the STS to encrypt tokens. In this way, the STS will be able to choose using different encrypting cert for different Relying Party.
Summary
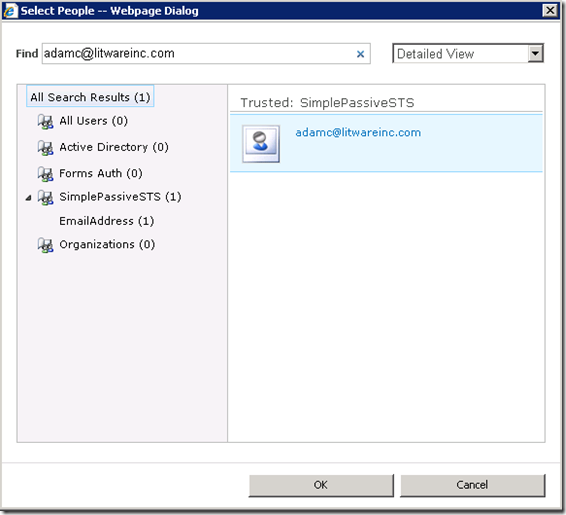
After finishing the above configuration, I can now add users from the STS to the SharePoint site. The CheckName function does not work because I didn’t implement a custom claim provider to handle it. For how to create a custom claim provider, please refer to the series by Steve Peschka.
The Select People and Groups dialog box works well.
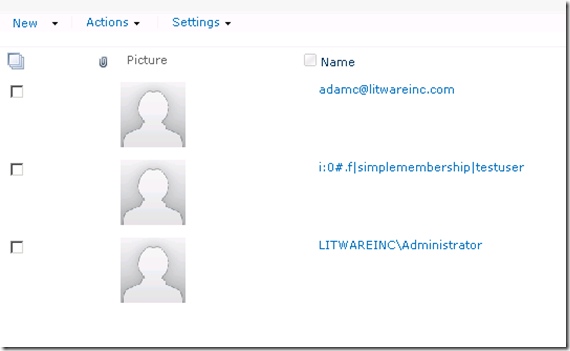
And here comes a page with user accounts from Windows Auth, Form based auth and Trusted STS.
-- The End.
Comments
- Anonymous
June 03, 2010
I perform the steps you proivided in SharePoint Foundation 2010 and got same error you mentioned but after I set <add key="EncryptingCertificateName" value=""/> the following error raised:Operation is not valid due to the current state of the objectDo you have any idea? - Anonymous
June 04, 2010
Would you tell where is <serviceCertificate> path in config xml? - Anonymous
June 05, 2010
dear Chun LiuI really need your help. - Anonymous
June 07, 2010
Hi Madnik7G,Sorry, I just saw your comments. The <serviceCertificate> should be added to <microsoft.identityModel><service>. Just before </service> is ok.You need to pay attention to the certificate you use here. It must be the one your STS uses to encrypt the token, and you should import both the cert and its private key into SharePoint server. You should also grant Read permission on the private key to the application pool account of your web app.Feel free to let me know if you need any further information. Good luck. - Anonymous
July 17, 2010
Thanks Chum LiuI create such IP-STS, and create custom SPClaimProvider, but couldn't find how to get issued claim by this STS in SPClaimProvider.FillClaimsForEntity.I need to add some custom claim to entity depending to claims issued by custom STS.Do you have any idea? - Anonymous
August 20, 2010
What should I look for if I get an exeception: "The token issuer is not a Trusted Issuer."? I have registered my CA as the Trust Root Authority and IP-STS and the TrustedIdentityTokenIssuer. I checked that both certs are in the local computer stores. The CA root cert is in the Trust Root Authority Store, and the IP-STS in the Trusted Publisher store. I also tried but in both stores and both in the Sharepoint store. All of which give the same results. How do I look at the SAML token to inspect its appearance/content (eg the name of the token issuer compared to what I registered.) - Anonymous
August 23, 2010
@CBB_II: according to the error message, it looks like the trusted token issuer was not registered correctly. one thing in my mind is the cert chain of your IP-STS need to be trusted by SharePoint. You can verify it through Central Admin > Security > Manage Trust.To check the claims before SharePoint accepts them, you can implement an HTTP Module. Steve Peschka has implemented one. you can find it on his blog. - Anonymous
August 23, 2010
I have verified that Manage Trust shows both the CA cert (Trust Root) and the IP-STS (Token Issuer)under one relationship. I have triple checked the thumbprints also. What cert stores should they be in, I assume the CA in the Local Computer, Trust Root Certificate Authority, I also put the STS in the local computer trusted publisher store and both in the Sharepoint store with no difference.Any other Ideas? - Anonymous
August 24, 2010
@CBB_II: maybe you want to look at this artilce blogs.msdn.com/.../sharepoint-2010-claims-based-auth-with-adfs-v2.aspx. it's quite hard to troubleshoot problems in this comments way. i'd suggest you raising your problem to Microsoft online forum to get someone look into the problem. - Anonymous
September 05, 2010
Hi, Chun LiuI perform the steps you proivided in SharePoint Foundation 2010 and got error as:Operation is not valid due to the current state of the objectPlease help me with this. I really need this. - Anonymous
September 06, 2010
The comment has been removed - Anonymous
September 07, 2010
CBB_II, thanks for you reply. I am able to resolve this issue. The issue was related to claim mapping. - Anonymous
September 07, 2010
CBB_II, thanks for your reply. I am able to resolve this issue. It was related to wrong claim mapping I used.One more thing. In the email address claim type I get empty string even though user has email address. Do you have any idea where I am going wrong. - Anonymous
September 16, 2010
The comment has been removed - Anonymous
October 12, 2010
I got error " The issuer of the token is not a trusted issuer" when i integrating sharepoint 2010 with acs v2 - Anonymous
October 12, 2010
I got error " The issuer of the token is not a trusted issuer" when i integrating sharepoint 2010 with acs v2 any solution - Anonymous
October 19, 2010
divyeshkotadia how did u resolve the error could u explain in realm and give some example - Anonymous
September 11, 2011
Hi Chun Liu,I am trying to create custom sts, i have completed all the steps like registering to sharepoint.problem is : at the time of the login to the sharepoint site, it is redirecting to the custom sts login page when i choose the login for custom sts at the sharepoint end. after checking the credentials it is not redirecting into the sharepoint site, it redirecting to the default.aspx page of custom sts. can u please check and do the needful.