AD FS 2.0 Proxy Management
Overview
Since the AD FS 2.0 release candidate (RC), the AD FS product team got feedback that the experience of setting up AD FS proxy server and making it work with AD FS Federation Service is cumbersome, as it involves multiple steps across both AD FS proxy and AD FS Federation Service machines.
In AD FS 2.0 RC, after IT admin installs AD FS 2 proxy server on proxy machine, she runs proxy configuration wizard (PCW) and needs to:
- Select or generate a certificate as the identity of the AD FS 2 proxy server.
- Add the certificate to AD FS Federation Service trusted proxy certificates list
- Outside of AD FS management console, make sure the certificate’s CA is trusted by AD FS Federation Service machines.
Such above steps are needed to set up a level of trust between AD FS proxy server and AD FS Federation Service. The AD FS proxy server might live in DMZ and provides one layer of insulation from outside attack.
AD FS administrator need to keep track of the proxy identity certificate life time and proactively renew it to make sure it does not expire and disrupt its service.
There are several pain points around AD FS proxy setup and maintaining experience for AD FS 2 RC version:
- Setting up proxy involves touching multiple machines (both proxy and Federation Service machines)
- Maintaining AD FS proxy working state involves manual attention and steps
In RTW, above issues are addressed by:
- Easy provisioning: AD FS admin set up proxy with AD FS Federation Service by specifying username/password of an account that is authorized by AD FS Federation Service to issue proxy trust token to identify AD FS proxy servers. The proxy trust token is a form of identity issued by the AD FS Federation Service to the AD FS proxy server to identify established trust. By default, domain accounts which are part of the Administrators group on the AD FS Federation Service machines or the AD FS Federation Service domain service account are granted such privilege to provision trust by proxy from AD FS Federation Service. Such privilege is expressed via access control policy and is configurable via powershell. By default proxy trust token is valid for 15 days.
- Maintenance free: Over time, the AD FS proxy server periodically renews the proxy trust token from the AD FS Federation Service to maintain AD FS proxy server in a working state. By default AD FS proxy server tries to renew proxy trust token every 4 hours.
- Revocation support: If for whatever reasons, established proxy trust needs to be revoked by AD FS Federation Service, AD FS Federation Service has both powershell and UI support to do that. All proxies are revoked at the same time. There is no support for individual proxy server revocation.
- Repair support: When proxy trust expires or is revoked, AD FS administrator can repair such trust between AD FS proxy server and AD FS Federation Service by running PCW in UI mode or command line mode (fspconfigwizard.exe) .
Management support
Several management aspects are involved in the new trust mechanism. Events are added to proxy server for:
- AD FS proxy is set up correctly with AD FS Federation Service
- AD FS proxy server has renewed trust with AD FS Federation Service
- AD FS proxy failed to talk to Federation Service due to expired or invalid trust
Events are added to Federation Service server for:
- AD FS proxy trust is established from a proxy machine
- AD FS proxy trust is renewed from a proxy machine
Generic authorization event will be logged when:
- Some party tries to establish or renew proxy trust using invalid credentials.
Proxy trust token issuance is audited just as any other issued token when AD FS audit is turned on. There are several knobs to turn to configure various proxy trust parameters:
- AD FS proxy trust token lifetime
- AD FS proxy trust renew frequency
Work flow
Provisioning
The following picture shows AD FS admin running PCW and setting up trust from proxy server to Federation Service.
The following screen shows that trust is established from proxy server to AD FS Federation Service.
From event log on proxy machine, you can see proxy server has successfully established trust with AD FS Federation Service.
On the Federation Service machine, you will see following related events.
(Note: There are two 395 events created corresponding to provisioning of one proxy machine. It is a side effect of PCW validating user name and password and establishing trust at the end of the wizard.)
Proxy server automatic trust renewal
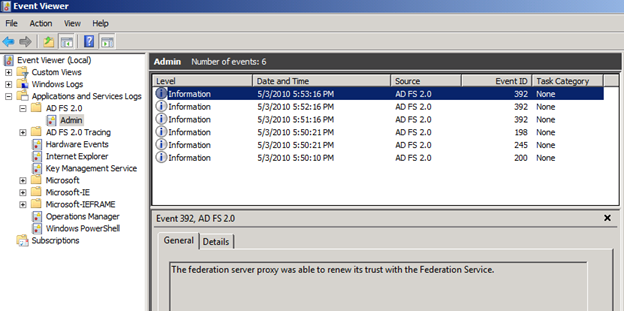
Proxy server automatically renews trust with AD FS Federation Service. When that happens, you will see following event in event log on proxy machine.
Revocation
When a proxy server is compromised, the administrator of the AD FS Federation Service needs to revoke trust for all proxy machines. The following picture shows how AD FS admin could do it from UI. After proxy trusts are revoked, all proxy machines need to provision again to gain access to AD FS Federation Service.
Related powershell cmdlets
Several PowerShell cmdlets have been updated to provide PowerShell management of this new functionality:
On the proxy machine:
Get-ADFSProperties, Set-ADFSProperties: (ProxyTrustRenewPeriod) get or set how often proxy server renew proxy trust with AD FS Federation Service
On the Federation Service machine:
Get-ADFSProperties, Set-ADFSProperties: (AddProxyAuthorizationRules, ProxyTrustTokenLifeTime): as property names suggest.
Revoke-ADFSProxyTrust: revoke issued proxy trust. Proxy machines need to provision again to gain access to AD FS Federation Service.
Comments
- Anonymous
November 03, 2011
I guess that on the proxy machine Get/Set-ADFSProxyProperties should be used insted of Get/Set-ADFSProperties.Kind regardsMartin - Anonymous
September 17, 2013
HiThanks for sharing these article marketing tips with people.This is very important information that you share. Article marketing tips are very useful for people