The Hierarchy of Cyber Needs
It takes a lot of time, effort, expertise and money to protect an enterprise network against today’s cybersecurity threats. The security market thrives, and businesses have many products and consulting services to choose from. So how do you invest your security dollars most efficiently? Cybersecurity spending requires a plan, whether building IT infrastructure from scratch or improving an existing enterprise network. Consider the following Hierarchy of Cyber Needs, built from the experiences of an Incident Response team that has seen it all. This chart will help you identify and prioritize which layers of security need investment within your enterprise. Use this as a road map to improve your enterprise security as quickly and cost-effectively as possible.
[caption id="attachment_43" align="alignnone" width="745"]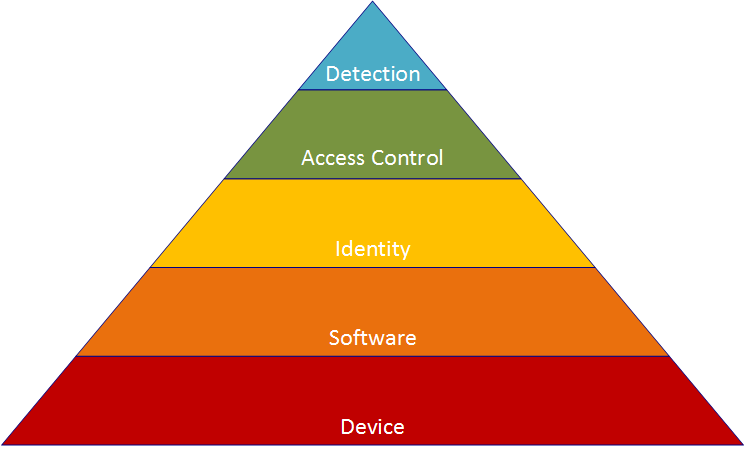 Captain's Hierarchy of Cyber Needs[/caption]
Captain's Hierarchy of Cyber Needs[/caption]
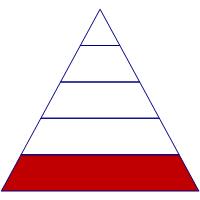 |
Device Management Needs |
The foundation of your enterprise security rests with your device management capabilities. Only machines that can be inventoried and centrally managed can reasonably be secured against advanced attackers. An accurate inventory is a critical first step to protecting a network. Any action to protect those assets will involve pushing tools to and pulling data from those devices. While device management software such as System Center Configuration Manager (SCCM) is not traditionally seen as security software, a company’s information security capabilities are only as good as their core device management capabilities allow.
From time to time our team gets called to respond to targeted attacks against enterprise networks that lack any central management. In such cases it invariably takes much longer to identify their critical infrastructure. Frequently the customer sends employees from computer to computer to run tools and collect data necessary for the investigation. In all such cases our primary advice for the customer is to invest in deploying SCCM, which most customers already have licenses to use. Third party alternatives also exist that are also up to the task of managing global corporate networks. Whichever solution you use, make sure you invest in your device management capabilities before you invest further in your cybersecurity infrastructure.
If you already have a central management solution, I encourage you to test your capabilities. While most customers have SCCM or a third party equivalent deployed, many of them do not use it regularly. Deploy a package such as the Microsoft Safety Scanner to all machines. Pull a small amount of data – such as the last patch time – from all computers and measure the time it takes. Slower package deployment times indicate slower response times during a breach, and slower response times limit response effectiveness. The slowest time recorded by one of our customers to deploy a scanner company-wide was seven months. Can your IT staff do better?
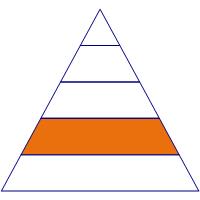 |
Software Management Needs |
The second layer of corporate cybersecurity is all about the software lifecycle. The Microsoft Security Intelligence Report (SIR) shows an industry-wide trend of a thousand high-severity vulnerability disclosures per year. Published vulnerabilities, especially those with proof of concept code, quickly become weaponized. To better understand the risk that users face with unpatched systems, go read about the Rolodex of Evil. Your ability to protect credentials and critical assets are limited if a large portion of your computers are vulnerable to exploits easily downloaded from the Internet. The risk is even greater with unsupported software such as Windows XP. Unsupported software no longer receives security patches but vulnerabilities are probably still being discovered. Consider the use of such software the same as implementing a corporate policy of never installing security patches.
There’s no such thing as a free lunch. Beware using pirated software or running license cracking tools, for they come with a hidden cost. The sites that distribute free software often come with unexpected extra software. One APT group in particular specializes in releasing cracked tools as a means of establishing a foothold in corporate networks, and the group is exceptionally successful.
How do you enforce software patching in your enterprise? Best practices call for an accelerated patch cycle for critical assets such as domain controllers and servers, and a regular patch cycle for all other devices. Also be sure to have a plan for emergency patching – for situations where very severe vulnerabilities require faster than normal patching. If your company delays security updates to perform tests and avoid business disruption, remember to balance that delay with the risks caused by unpatched software.
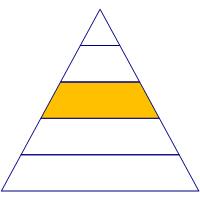 |
Identity Management Needs |
Enterprises with solid device and software management infrastructure spend most of their attention in the Identity Management layer of the hierarchy. Identity Management gets a lot of press due to the proliferation of powerful credential theft tools such as Mimikatz and Windows Credential Editor (WCE). Everything we do in business - with or without computers – is based on identity. Running an enterprise without robust Identity Management is like running a bank that doesn’t ask customers for identification when making withdrawals.
Identity management starts with several basic concerns about user accounts and passwords. Do not use shared accounts – make sure that your employees and customers are uniquely identified. Minimize or eliminate all guest and anonymous accounts. Verify your password policy for best practices regarding complexity, length, and expiration. Make sure that your service account passwords meet these requirements as well.
The local administrator account is an often overlooked weakness. If every computer shares a common local admin password, then the account is practically a Domain Administrator. Disable the local administrator account and rely on domain accounts instead, or better yet deploy the free Local Administrator Password Solution (LAPS), available from Microsoft here.
After the basic identity management steps comes the infamous Pass the Hash Whitepaper. Once steps have been taken to ensure credentials can reasonably identify users, the next step is to prevent credential theft and lateral account movement through your enterprise. This is part of the “Assume Breach” philosophy: assume that one or more user accounts will be compromised, and take steps to prevent one compromised account from compromising all accounts. Read more about the best practices for Securing Lateral Account Movement here.
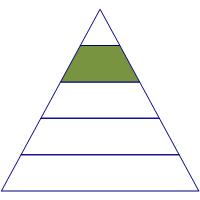 |
Access Control Needs |
Once you are able to inventory and manage your computers, keep systems up to date with security patches, and establish a reasonable measure of confidence with identity and account management, your next tier of security is the need for Access Control. The principle of least privilege is easily understood: the fewer people who know KFC’s secret blend of herbs and spices, the lower the risk of theft. Implementing least privilege in an enterprise is time-consuming and inconvenient but greatly reduces the risk and damages from a breach. Here are the top Access Control projects to invest in.
Make your users non-admin. Many enterprises make all users local administrators on their computers, and in doing so they make it easier for tools like WCE and Mimikatz to harvest credentials. Service accounts and third-party software frequently run as Domain Admin, when they very rarely need to. These service accounts widely expose DA credentials for theft. LUA Buglight is a fantastic tool that can help you lower the privileges of both your line of business software and third party software. And if you need assistance, Aaron Margosis lurks always in the shadows, waiting for an opportunity to remove another elevated application from the world.
Critical resources – the “crown jewels” of the company – are frequently not segmented away from the majority of the user accounts. In such an environment, compromising any account allows relatively unimpeded access to the corporate crown jewels. Compartmentalize your network and access to resources wherever possible. If your domain admins for the New York office are only tasked with administration of that one location, do not automatically grant them unlimited power over the London office. Users collaborating on highly sensitive documents such as upcoming SEC filings should store them on servers with limited access, not on your company’s general-purpose file server.
Your domain controllers, domain admin credentials, and trusted certificates are all part of your crown jewels and should be protected accordingly. Remember – and this really happened to a Fortune 500 company – you lower the risk of DA-level breach if you do not surf the web from your domain controllers. A best practice is to use dedicated workstations (PAW) to perform sensitive tasks such as administering domain controllers. Use a tiered containment model to protect critical credentials and resources as described in the PTH whitepaper.
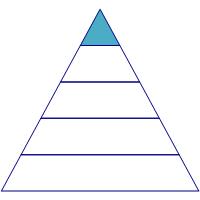 |
Detection Needs |
The apex of cyber needs is Detection. This layer is the most sophisticated to implement successfully and has the greatest number of prerequisites. I have seen companies invest in network intrusion detection systems that report threats that could not be mitigated with their limited device management capabilities. I have assisted customers who subscribed to expensive threat intelligence feeds for IOCs that their companies lacked the ability to leverage. The detection layer becomes more valuable and relevant once your IT staff has the capability to exert control over your enterprise network, your software is up to date, and access to network resources has been restricted and segmented where possible. Focus additional resources here once you are ready and able to respond to threats to your network.
Build your detection strategy with two thoughts in mind: passive versus active detection and on-site versus managed detection. Passive detection contains elements such as logging, which exists to facilitate everything from forensic investigations to IT debugging. The greatest challenges for passive detection involve the ability to collect all the data you need while filtering out enough of the data you don’t to make storage possible. Anyone who has tried event log forwarding at an enterprise scale has discovered the need to reduce the amount of logging. Learn from the experience of others and monitor what matters most. Active detection contains elements that send alerts and require action, such as intrusion detection systems and antivirus software. On-site detection capabilities cover investments such as a Network Operations Center and a SIEM, capabilities that require dedicated and trained personnel to operate effectively. Managed detection capabilities, on the other hand, are like home security monitoring services: they leverage remote experts to provide 24/7 protection for your enterprise. In theory, on-site detection has the ability to out-perform third-party managed detection due to greater knowledge of your network and better integration with your business. In practice, very few companies can retain the sort of specialists who hunt targeted attackers the way that dedicated cybersecurity companies can. Where possible, consider investing in managed detection services such as Microsoft Threat Detection Services (MTDS) and Advanced Threat Analytics (ATA).
Conclusion
Whether you are building your corporate security infrastructure from scratch or enhancing what you already have, it helps to have a plan. Companies that do not understand the implicit prerequisites that come with certain security products find themselves spending money on technology they cannot fully utilize. Using the Hierarchy of Cyber Needs to make security investment decisions helps you achieve the most with your time and money as well as build a multi-year plan of continuous security investment.
Comments
- Anonymous
January 26, 2016
Great article. I will be referencing it a lot with my customers as it does a great job of structuring a path to a secure environment. It gives people the path to success.Thanks!