Security Patching and You
In a lot of my customer engagements at Microsoft I get to see how a lot of customers do their monthly patching and which of these customers view it as a priority. I have seen customers who patch immediately on release of the monthly bulletins, and I have also seen customers who are 3+ years out of date.
This blog post is to help highlight your role as an administrator to help maintain security patch levels for your environment. An interesting topic, I know. But, keep reading - I will make it worth your while, I promise.
Let's start with what exactly a security patch is. A security patch is a fix to a piece of code which exposes a security weakness in the OS or application. A security weakness could be the ability for an attacker to execute remote code, or gain elevation of privilege. Let's also get one thing straight - the person who is exploiting the vulnerability isn't necessarily the person who was crafty enough to find and write the exploit. Vulnerability code is often shared, or bought - but that is a topic for another day.
Now let's get into your responsibilities as an administrator. If you were a mechanic, you probably wouldn’t be reading this blog. You would likely be busy ensuring that the car you are servicing is going to keep the occupant safe. This mentality carries merit in the IT industry as well. Sure, If you forget to apply a security patch your customer might not die as a result of your negligence. However, if you are an organisation that provides critical health care, or you are support for deployed soldiers, an outage to a critical system as the result of an exploited known vulnerability may result in uncomfortable circumstances.
If it is a Government agency you work for, you might also be having a conversation with a person in dark glasses and a suit asking why you didn’t feel the need to be compliant with the Defence Signals Directorate (DSD) Information Security Manual (ISM).
Control 1144 in the DSD ISM is very specific "Agencies must apply all critical security patches within two days."
If you work for a private enterprise that doesn’t 'protect' or 'serve' you might think you got off lightly here. However, it may be an idea for you to think of the importance of your job. Picture it like this. If, as a result of a known security vulnerability, your employer suffers a security incident and the intellectual property that your company uses to make money is stolen. Your employer may no longer be able to compete, and in turn might not be able to pay your salary. In this instance, it won't just be you that they can't pay - it would likely be the majority of the company.
In my opinion the "Security is Everyone's Responsibility" tag line has made people lazy. Make it your responsibility to drive security patching - make the reason you patch selfish. "If the systems I look after are not patched it might affect me". The IT industry is not yet as regulated as highly as it could one day be. If you were a doctor or a lawyer, professional negligence could land you jail time. I hope we don't get there. However, with IT Security becoming more of a focus in the last few years this is what could become your motivation for patching your servers in an acceptable time frame.
What is an acceptable time frame you ask? Well, there is the argument that goes something like this - "It takes me time to deploy my patches because I want to make sure they are tested in my lower environments to make sure the patch doesn't mess up my production servers". To that I say, "What if by delaying your patches a known vulnerability is exploited and really messes up your production servers?". Like everything, there is a balance to be attained here. We maintain an exploitability index to help customers prioritise the release of security patches. This is a good starting point to help achieve this balance. There is the risk of deploying and the risk of not deploying quickly enough.
There is one exception to this balance - Out-Of-Band patches. Out-Of-Band patches are released outside of the standard 'Patch Tuesday' release cycle. These patches are critical fixes for vulnerabilities for which have already seen exploits that have had a significant impact. If we ever release an Out-Of-Band patch, sit up and take notice. Out-Of-Band patches should be applied immediately.
Do I need to patch anything else?
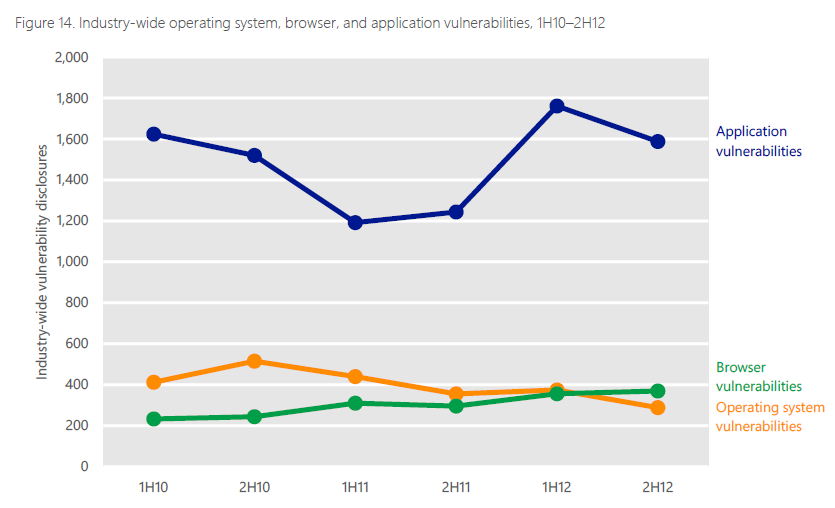
Patching doesn’t stop with simply patching the Operating System - applications are just as important. Microsoft puts a lot of time and money into security research. Below is a snippet from the Microsoft Security Intelligence Report . You can see a significantly higher number of vulnerabilities when it comes to applications. So, make sure you are keeping on top of updates to your 3rd party applications as well.
If you only have limited time, or limited resources - Operating System and Application patching will be one of the best things you can do in improving your organisations security posture. In fact it has made the DSD list of "Top 4 mitigation strategies to protect your ICT system".
If you want to be kept up to date on security patch releases, you should sign up for the Microsoft Technical Security Notifications.This will ensure that advance notification of all patches will arrive conveniently in your inbox while you sip your coffee.
We also post this information, and all sorts of other good stuff on the Microsoft Security Response Centre blog.
Now, for those who kept reading - I told you I would make it worth your while, so here it is. https://www.youtube.com/watch?v=Zce-QT7MGSE
Until next time.
Marc
Comments
- Anonymous
July 24, 2013
Q. But how do I know what patches I'm missing if I don't connect to the Internet?A. MBSA offline scan."You've got an orange peanut? For me? That's right." Quit watching YouTube and go patch your servers!