Using TLS 1.2 with WCF
This article has been moved to it new home here: https://benperk.github.io/msdn/2014/2014-11-using-tls-1-2-with-wcf.html
NOTE: Security is a very serious topic and you should always engage an IT security expert before deploying an application that needs to be secure. This article is intended to share my experience versus being an article to use as a guideline.
With all the news about the different vulnerabilities like heartbleed and poodle, developers and companies alike are taking an extra hard look at the protocols, hashes, cyphers and encryption technology they have implemented in their environment. Rightly so.
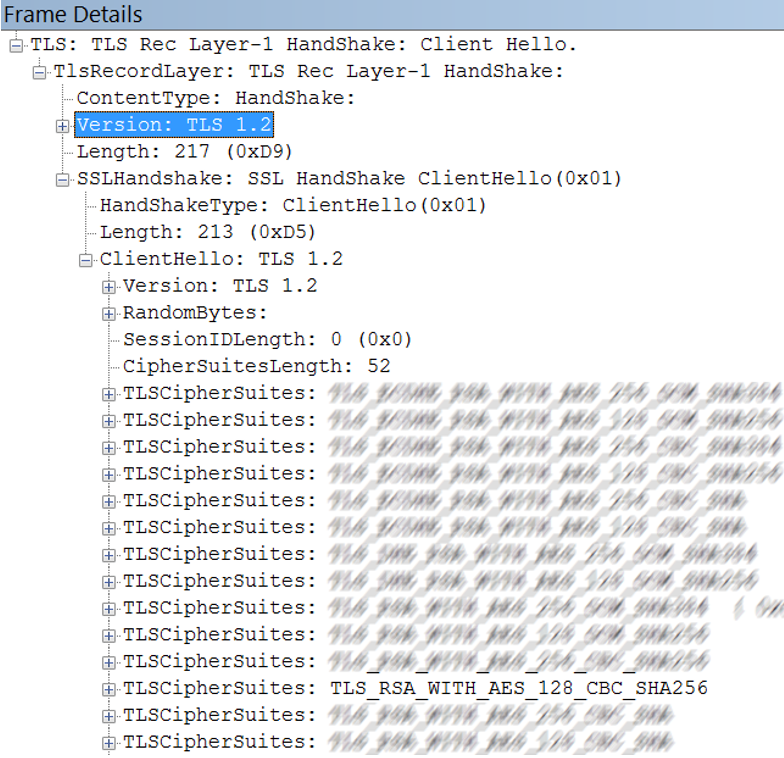
One thing I found was that when I was testing a WCF call to one of my test Azure Websites, the cypher suite which the client and server were agreeing on was TLS 1.0 and TLS_RSA_WITH_RC4_128_SHA, as shown in the Network Monitor trace, Figure 1.
Figure 1, WCF using TLS 1.0 instead of TLS 1.2
I confirm the agreed upon Cypher Suite by looking into the Server Hello message within the Network Monitor trace shown in Figure 2.
Figure 2, WCF TLS 1.0 agreed on TLS_RSA_WITH_RC4_128_SHA instead of 1.2
As per this article, Cypher TLS_RSA_WITH_RC4_128_SHA does support TLS 1.2. So why did it not use TLS 1.2?
Before I answer that question, when I used a browser like Internet Explorer 11, which was configured to support TLS 1.2 and accessed the same WCF service, I am indeed using TLS 1.2, as per Figure 3.
Figure 3, TLS 1.2 is supported on Azure Websites, based on my findings
The way I ultimately got my WCF client to use TLS 1.2 is by installing this hotfix, and you must use .NET Framework 4.5, please correct me if I am wrong, see below links…
I am not part of the development team nor do I have access to much of the information they use to determine what gets included or not in the framework, but it seems that the inclusion of TLS 1.2 into WCF is an opt-in decision. You opt-in to using TLS 1.2 by knowingly installing the hotfix.
Some additional articles in context:
- How to Determine the Cipher Suite for the Server and Client
- SslProtocols Enumeration .NET Framework 4.5 - notice TLS 1.2
- SslProtocols Enumeration .NET Framework 4 - notice no TLS 1.2 or 1.1
UPDATE: Check out a registry setting as well.
Under following keys for all the version key listed like V1.0, V2.0.50727,v3,v4.0.30319. Create key SchUseStrongCrypto(type dword, value 1)
HKLM\software\Wow6432Node\Microsoft\.NETFramework\
HKLM\software\microsoft\,NETFramework\
Comments
Anonymous
July 15, 2015
The comment has been removed- Anonymous
December 14, 2016
Yes it helped me. Thanks- Anonymous
December 14, 2016
Me too.
- Anonymous
- Anonymous
Anonymous
July 29, 2015
Thanks for sharing your solution, Appreciated.Anonymous
July 15, 2016
Sorry we're late to this party. We have a WCF service that doesn't seem to be accepting TLS 1.2.It seems to be that the System.Net.ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12; code needs to be added to the client, not the server... is that a correct assumption? We have many clients connecting thru other technologies like PHP, Java, etc... When we add the System.Net.ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12; code to our test client, it seems to get passed the https error. We've read that upgrading the server WCF API to .NET 4.6.1 should resolve all issues, but it doesn't seem to.Does anyone know of specific instructions of what needs to be done on the server side with settings and code to get this to work?Anonymous
December 14, 2016
Me Too. Thanks.